How Cybercriminals Hijack Payment Conversations
Summary
A Man-in-the-Middle (MITM) financial fraud attack happens when a threat actor monitors an email chain between two different parties. The threat actor will continue to intercept and read these emails prior to the email being sent to the proper destination. The threat actor will wait for when payment methods are talked about. The threat actor will then redirect the payment method to themselves for financial gain.
Blackpoint SOC has started to see an uptick in BEC (business email compromise) where there are indications that the start of this attack is happening. What we notice are inbox rules being created maliciously to target specific key words and redirect those emails to a folder that isn’t typically checked by a user. By doing this, it hides the email once that keyword is hit, giving the threat actor access to that email of all the sensitive information in the thread first. From there the email is spoofed and redirected to their own account to have the target send them the payment method willingly.
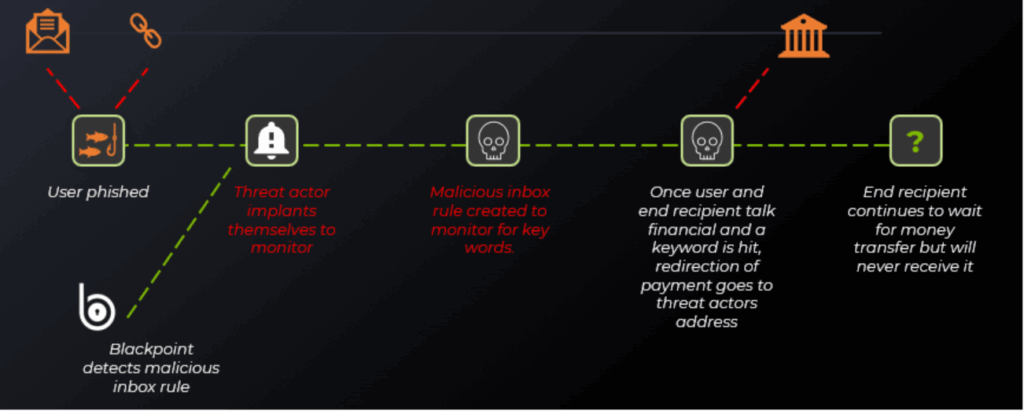
* Path example for MiTM BEC attacks
Some keywords often being targeted include but are not limited to:
Invoice, payment, transfer, account, statement, settlement, ach, wire transfer, bank, due date, closing date, refunds, trade, eft, donation, request, overdue, payment, outstanding, money, etc.
Initial access is generally through phishing emails, DNS/ARP spoofing, HTTPS downgrade attacks, or malware on a machine that allows a threat actor to change browser redirects.
We will cover three Incidents observed recently, the full timeline and the indication that the start of this attack is happening.
Incidents
Attack 1:

In this attack a user was likely phished. We then alert to a login event using Express VPN. This was the first red flag as Express VPN wasn’t previously observed for this user account. Within twelve minutes, threat actor then created a malicious inbox rule called “.” And will redirect emails to the “Conversation History” folder for this user. VPNs are commonly used by threat actors to bypass conditional access policies.
Details for inbox rule:
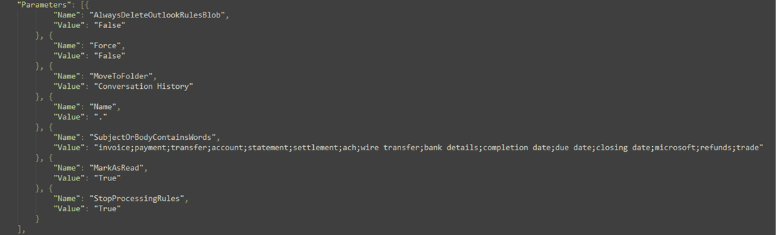
This threat actor was targeting specific words in the subject line “invoice”, “payment”, “transfer”, “account”, “statement”, “settlement”, “ach”, “wire transfer”, “bank details”, “completion date”, “due date”, “closing date”, “microsoft”, “refunds”, “trade” and if any email that comes through with any of these words in the subject line of the email, it will be redirected to the “Conversation History” folder.
Attack 2:

In this attack, it was similar to the first attack where the threat actor logins in with Express VPN to bypass conditional access policies. The first red flag was this being a first time VPN login from this user. At the same time as VPN login, threat actor created a malicious inbox rule using the same VPN.
Details for inbox rule:
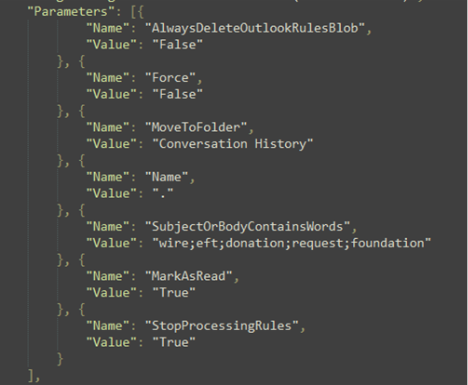
This threat actor is targeting the words “wire”, “eft”, “donation”, “request”, or “foundation” in the subject line of the email. If an email is received with any of these words in the subject line, it will be redirected to the “Conversation History” folder, marked as read, and stop processing the email.
Attack 3:
This attack involves two different user accounts.
1st user logged in with Express VPN and then created an inbox rule 2 minutes after using the same VPN.

Details for inbox rule:
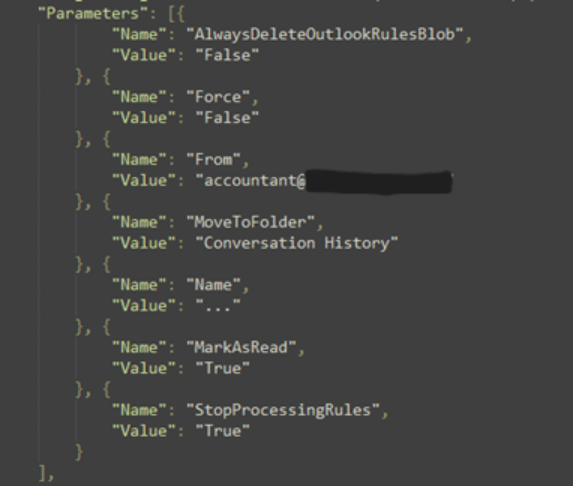
What this rule does is target any email that is sent from the “accountant” account and move the emails to the “Conversation History” folder. This suggests that there is another user account that was compromised.
2nd user. This user account has several IOCs (indicator of compromise). First, the threat actor logged in with Express VPN. Second, the threat actor logged in with a different VPN, Mysterium VPN. Third, threat actor is observed logging in from Nigeria not using a VPN, likely opsec failure due to forgetting to login with VPN. Fourth, using Express VPN, a malicious inbox rule is created.
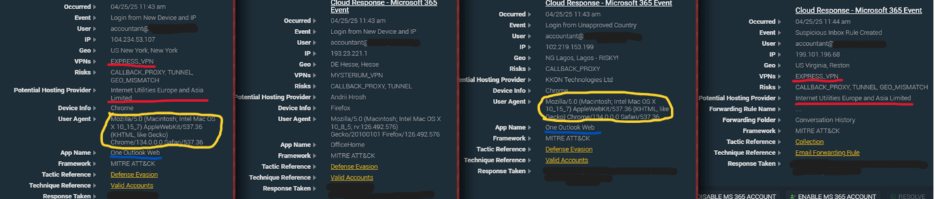
Details for inbox rule
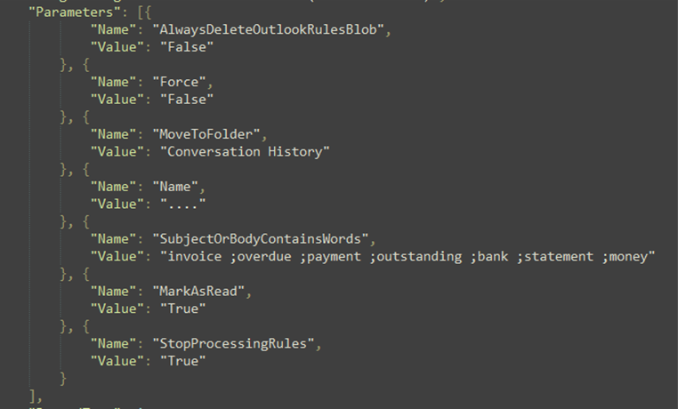
What this rule does is target the words “invoice”, “overdue”, “payment”, “outstanding”, “bank”, “statement”, or “money” in the subject line. If any email comes through with any of those words in the subject line, it will be moved to the “Conversation History” folder.
TLDR: For this incident. Two users were compromised, both likely in the accounting department. The threat actor was able to compromise one user, then using that account likely sent a malicious email to compromise another user. The threat actor then created malicious inbox rules to redirect emails targeting specific words to a folder that isn’t typically checked by users to hide their tracks.
Overview
Threat actors are relentless in their attempts to breach organizational defenses. One of their primary methods remains the use of malicious emails to gain initial access (people are the weakest link in all cyber defense). With the rise of readily accessible tools such as Evilginx and AI, crafting convincing malicious emails has made it easier for threat actors. Once inside a targeted network, they often spread laterally by sending additional phishing emails internally, targeting other users across the environment. After establishing a foothold, many attackers patiently monitor internal and external email communications, specifically seeking financial conversations. When they identify an opportunity such as a payment discussion, they will inject themselves into the thread to redirect or hijack the transaction for their own gain. To evade detections, threat actors frequently abuse commercial VPN services to bypass conditional access policies, to blend in with normal traffic. They also create malicious inbox rules that automatically forward, hide, or delete important emails, preventing their victims from noticing suspicious activity.
Organizations must stay vigilant. Implementing a plan that authorizes only trusted VPN providers, enforcing strong multi-factor authentication (MFA), providing security awareness, constant phishing simulations, and continuously monitoring login activity are crucial steps in disrupting these attacks before they escalate into costly financial fraud.
Mitigation
Never click on suspicious links
- Threat actors will send spoofed emails to harvest credentials or steal SessionIDs. Never click a link from an untrusted sender
- If a colleague sends a suspicious link, verify with them first before clicking, never input credentials into links sent to you
Use Strong Encryption
- Make sure all sensitive communications (especially financial ones) use strong protocols TLS/SSL, never HTTP as traffic is in cleartext or outdated SSL/TLS versions
Verify SSL/TLS Certificates
- Watch for certificate warnings
Network Security
- Always use trusted known networks, never public WIFI.
- Stay away from commercial VPNs
- Ensure conditional access policies are implemented to geoblock locations not needed for business operations
Multi-Factor Authentication (MFA)
- Even if credentials are stolen, MFA can block unauthorized transactions. Ensure it’s implemented on all administrator and accounts that deal with sensitive information
Email Security
- Implement DMARC, SPF, and DKIM to prevent email spoofing.
- Use secure email gateways to filter phishing attempts.
Endpoint Protection
- Keep devices updated and monitored for malware (like keyloggers or session hijackers).
Real-Time Monitoring
- Blackpoint’s Cloud Response integration
DATE PUBLISHEDJuly 17, 2025
AUTHORBlackpoint Cyber
SHARE ON
Subscribe to the Blackpoint Blog
Don’t let a lack of awareness leave the organizations you protect vulnerable to sophisticated and elusive attacks. Subscribe now for a weekly roundup of Blackpoint’s empowering articles.
Subscribe now!