No Encryption, No Problem: Extortionware on the Rise
The Road from Network Encryption to Organization Extortion
Ransomware attacks have posed a critical threat to organizations worldwide for more than 20 years – from floppy disks to USBs, then simple encryption to data theft and distributed denial of service (DDoS). However, the ransomware landscape is evolving yet again, this time eliminating the need for a payload and focusing purely on extortion, thus introducing extortion-only ransom demands.
Ransomware attacks initially meant that a network and files in a business were encrypted, effectively bringing a business to a standstill. An attacker would demand money to decrypt these files and relinquish the network back to the victim (in theory, not always in practice). In response to this threat, regular backups became more commonplace in enterprise environments. More products and services have entered the market to make backups of critical business files easier for IT departments. Emergency response security services began popping up to assist unprepared or underprepared organizations return to normal operations as soon as possible after an attack. This lowered the efficacy of ransomware attacks by mitigating the primary method of extortion.
Around 2019, threat actors were reported to adopt the double extortion model to increase the chances of a ransom payment. In addition to encrypting critical business systems, operators began exfiltrating sensitive data that would be leaked publicly or sold if the ransom was not paid. This increased the chance of payment in two ways – even if the victim has solid backups, they may pay to prevent a public breach, or they don’t, and the threat actor sells or leaks that information. By taking this twofold approach, a threat actor increased the likelihood of a ransom payment one way or another.
H1 2025 Ransomware Landscape
In the first half of 2025, Blackpoint’s Adversary Pursuit Group (APG) tracked 97 unique data leak sites. This allows us to maintain insight into the overall ransomware landscape and emerging trends to ensure a comprehensive view of ransomware targeting. While some of these operations are now considered extortion-only, Blackpoint’s APG tracks all data leak sites related to both types of extortion attacks.
From 01 January – 30 June 2025, Blackpoint’s APG identified 3,763 organizations listed across those 97 data leak sites, which is a 62% increase from H1 2024. It is likely that over H2 2025, the top 10 will shift as groups like Ransomhub are considered no longer active and groups like Clop are active after they become aware of high impact vulnerabilities, like targeting the 2024 Cleo vulnerabilities. Targeting zero-day vulnerabilities in file transfer software to target hundreds of victims over the course of weeks or months has become the roadmap for the Clop Ransomware operation, who has switched to the extortion-only approach as their primary method of financial gain. Additional H1 2025 statistics and details can be found in Blackpoint’s H1 2025 Threat Landscape Report.
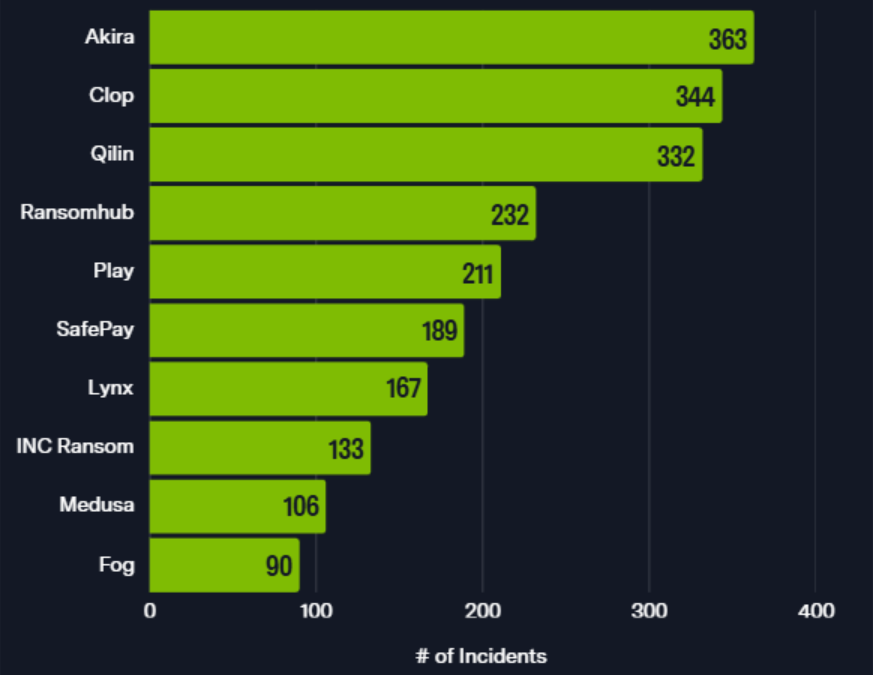
Figure 1: Most active ransomware operations in H1 2025
The top three targeted verticals in H1 2025 were Industrials (Manufacturing) with 696 listed victims, Industrials (Construction & Engineering) with 308 listed victims, and Technology and Professional & Commercial Services (Business Services) tied for third with 251 listed victims. These verticals accounted for 40% of all listed victims in H1 2025. Additionally, North America was the most frequently targeted geography, with 60% (2,258) of all listed victims being based in North America and 87.9% (1,984) of those victims based in the U.S.
Emergence of Extortion-Only Attacks
Ransomware attacks have a history of being noisy. The operators gain access, move quickly through the network while collecting as much sensitive information as possible, and then deploy the ransomware payload for encryption. Throughout 2025, there has been a reported increase in the number of ransomware operations shifting from encryption and double extortion to extortion-only ransom attacks – forgoing the encryption phase altogether. Like the shift to double extortion in 2019, the shift to extortion-only indicates a significant transition in financially motivated ransomware attacks.
Extortion-only ransomware attacks apply the same type of additional pressure to victims, including
- Preventing the leak of confidential data.
- Damage to the organization’s reputation.
- The likely legal requirements and responsibilities that often accompany this type of attack.
However, operating on an extortion-only model cuts out several steps in the traditional attack chain, resulting in less detection opportunities for defenders and a stealthier attack for threat actors.
There are several additional benefits:
- Ransomware encryptors are often treated as SaaS applications – criminals pay a subscription for access and/or the encryptor provider receives a cut of the profit. By eliminating the use of the encryptor completely, a threat actor no longer pays that cost.
- Traditional encryption of a network is incredibly noisy, giving defenders more opportunity to respond, and lowering the effectiveness of the attack. At minimum, the massive amount of lateral spread activity during the deployment of ransomware from an impacted machine is removed during an extortion-only attack.
- Law enforcement and private security companies periodically release decryptors for known ransomware variants, undercutting the effectiveness of a ransom operation. For example, in January of 2023, Avast released a decryptor for BianLian ransomware. Previously, the group had employed a double extortion model. With the encryption extortion method now moot, the group switched to data theft extortion as the sole method of ransoming a victim, at least for a time.
With encryption no longer critical leverage, the threat actor must only achieve sufficient sensitive data exfiltration to strongarm victims. This can be done using traditional infostealer techniques or through LOLBINs used for file transfer, such as Rclone, MegaSync or PuTTY, to steal and exfiltrate large amounts of data.

Kill chain of an extortion-only ransom attack
The security community has observed threat groups making those shifts in real time. In April 2025, Hunters International announced they would be suspending their operations and releasing their decryptor, no longer holding victims to ransom. After, they rebranded themselves as WorldLeaks, an extortion-only operation. With a shorter kill chain and less overhead costs, it’s easy to see why this broader shift is taking place. While Hunters International was not considered one of the most active groups in H1 2025, with 47 listed victim organizations, the WorldLeaks site has named 31 victim organizations since it’s identification in January 2025. This indicates that while the group has likely shifted to extortion-only attacks, their cadence of targeting is unlikely to have slowed.
Inside the SOC: Halting CLOP’s Kill Chain
Blackpoint has observed attempted extortion attacks within our client base. The target of one of these attacks, located within North America within the consumer cyclicals vertical, alerted on a suspicious PowerShell execution.
A complete review of the activity on the host and within the environment revealed the execution to be Base64 encoded. The execution ran under a service account with prior history of encoded PowerShell executions. However, the decoded execution showed elements of additional, attempted obfuscation – ultimately attempting to make an external connection to an IP tied to a Russian domain. Blackpoint SOC isolated the machine and prevented further malicious activity.
Further investigation revealed a running process consistent with Clop, a Russian affiliated extortion-only ransom group. Blackpoint determined that the machine was isolated prior to successful connection to the group’s C2 server by this process. Malicious connections to the host were revoked prior to privilege escalation, environment scanning, or information theft. Initial access was attributed to the following publicly exposed ports:
- FTP port 21
- SSH port 22

Kill chain of an attack attributed to an extortion-only group within client base
Detection and Hardening Opportunities
Extortion-only attacks are quieter, but that does not mean they are silent. There are several detection and hardening opportunities that defenders can implement to ensure these attacks are mitigated, or ideally, prevented entirely.
Regular Privilege Auditing
Implement the practice of least privilege and perform regular privilege auditing to mitigate the risk associated with privilege creep. Ensure users do not have administrative privileges on their machines. Require administrative credentials for software installation, PowerShell execution, and cmd usage.
Audit the presence and use of data transfer programs and protocols in your environment
Verify the presence and use of data transfer programs and protocols are known and authorized in your environment. Remove software that has not been vetted or approved.
Additionally, consider implementing application controls to block or restrict the use of these programs in the environment.
Strictly control protocols with file sharing capabilities (ex. FTP, SSH, RDP) and do not expose them to the public internet.
Consider utilizing a dedicated software center to ensure employees can access authorized programs necessary to complete work. Implement regular updates of the software to minimize the threat of vulnerability exploitation.
Network Edge Security
Do not expose VPN login pages to the public internet. Blackpoint SOC routinely identifies exposed VPN login portals as a common initial access vector leading to compromised environments. Enable MFA for remote logins (and anywhere MFA is available). Regularly patch these devices as well. Edge devices frequently have severe vulnerabilities that are specifically targeted by threat actors, including ransomware gangs.
Additionally, confirm hosts do not have protocols/ports exposed to public internet.
Configure Blocking/Alerting for Common File Transfer Programs
Once you’ve determined which (if any) file transfer programs are known and authorized, consider implementing detections for unauthorized programs. Several antiviruses enable organizations to create custom detections based on file hashes. Check every so often for updates to this software and implement new hashes.
This does take some administration on the part of the defender. Blackpoint offers a feature called “Managed Application Control”, which helps take the research and manual input out of it. MAC will detect common file transfer software (and other LOLBins) and automatically block those processes, as configured by clients.
Conclusion
As threat actors shift their ransomware attacks to extortion-only models, defenders must evolve to adequately address the threat. Standard security hygiene is still relevant – regular tests and updates of network perimeter devices help address common initial access vectors, and attacker abilities within a network can be limited through regular auditing and strict control of user privileges. Additional effective mechanisms of prevention include limiting user privileges to install software, blocking common LOLBINs that are not authorized within an environment, and configuring alerts for attempts to install or run those tools.
References
- https://blackpointcyber.com/report/2025-threat-landscape-report/
- https://www.microsoft.com/en-us/security/blog/2025/08/27/storm-0501s-evolving-techniques-lead-to-cloud-based-ransomware/
- https://www.group-ib.com/blog/hunters-international-ransomware-group/
- https://www.hipaajournal.com/ransomware-groups-increasingly-conductingextortion-only-attacks/
- https://flashpoint.io/blog/new-ransomware-as-a-service-raas-groups-to-watch-in-2025/?CRO3=%233007_control