Phishing in the Dark: A Case Study of AzureAiTMFunction Exploitation
Threat actors are leveraging new ways to phish for session tokens within business email compromises (BECs). A recent trend has shown the utilization of Axios within these man-in-the-middle phishing campaigns. Axios is a promised based HTTP Client for node.js, which is consistently abused by threat actors in phishing campaigns to proxy login requests from the legitimate account owner. Blackpoint’s SOC has observed a large increase of phishing campaigns utilizing this user agent across multiple clients. However, the Blackpoint SOC recently responded to an incident where a threat actor phished a user account using AzureAiTMFunction.
AzureAiTMFunction is an open-sourced GitHub project, which leverages Azure Functions for user phishing. This project focuses on creating a serverless phishing toolkit, which is more opsec friendly due to requiring not as many resources as a typical phish kit.
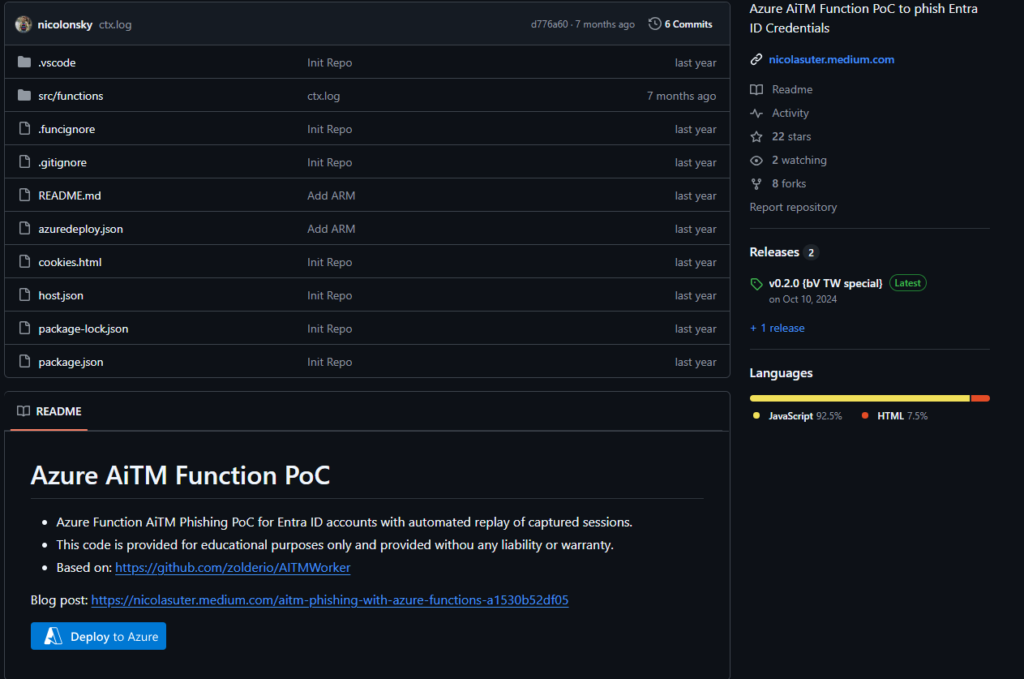
This specific project focuses on abusing Azure Function Application to host malicious Microsoft look-like phishing pages. Analysis into the source code found that this project does leverage the Axios framework for the man-in-the-middle aspect and session hijacking portion of this toolkit.
Key Takeaways:
- Threat Actors continue to adapt and leverage new tactics, techniques, and procedures (TTPs) within phishing campaigns
- Threat Actors are moving towards serverless methods within these phishing toolkits
- Credentials are not always the focus of these campaigns, threat actors are attempting to hijack and replay session tokens
Hook, Line, and Function. Catching Phish with Azure
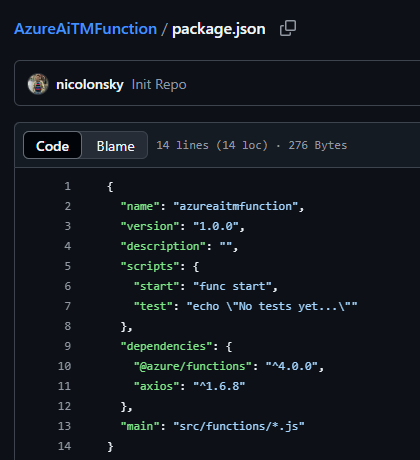
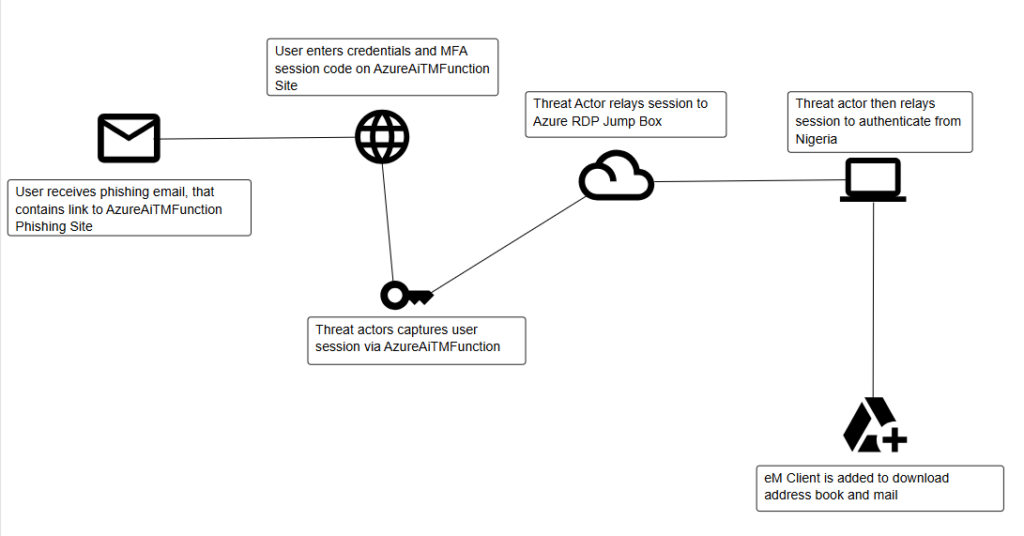
A recent incident handled by the Blackpoint SOC involved the utilization of AzureAiTMFunction. A threat actor leveraged this open-sourced toolkit to within a phishing campaign.
Investigation into this activity found that the threat actor was hosting this function app out of Switzerland. When the user fell for the phishing email, the TA leveraged this toolkit to relay the hijacked session token to an RDP Jump Box.
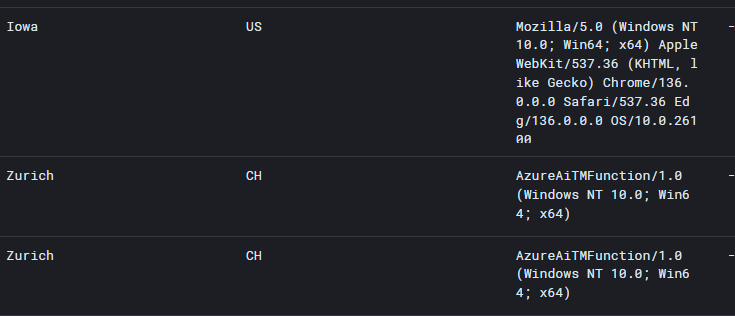
RDP Jump Boxes are Virtual Private Servers (VPS), which threat actors spin up to access compromised cloud accounts. The Blackpoint SOC calls them jump boxes as they are typically a hop threat actors utilize to try and further obfuscate their logins. These Jump Boxes typically have RDP publicly exposed, which is the preferred method for connection by a threat actor.
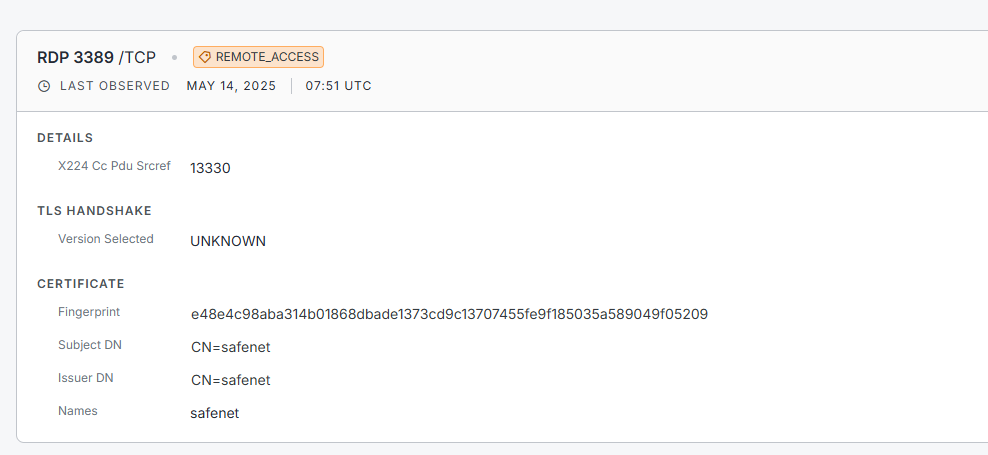
The CN name associated with the Cert for these RDP Jump Boxes is typically something abnormal, which is a telltale sign of the infrastructure being leveraged for malicious purposes. For this specific incident, checking Censys shows the name of the CN as “safenet”, which is not something that aligns with legitimate business purposes for the organization.
After relaying the session to this Jump Box, the threat actor then leveraged this stolen session to authenticate from Nigeria.
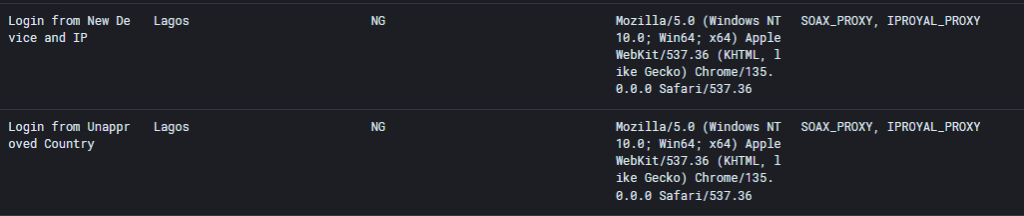
During the post exploitation of this Business Email Compromise (BEC), the threat actor consented to the Azure Application eM Client. This is a legitimate application, which is leveraged by threat actors in BEC’s for the exfiltration of mail and contact information. The threat actor will use the contacts in the user’s address book as targets in future phishing campaigns.
The Blackpoint SOC quickly identified this compromise and contained this account. The kill chain associated with this incident highlights the continuous utilization of new tools and techniques within these kill chains.
Recommendations to combat AiTM
Threat actors will continue to evolve their methods for successful phishing attacks with function such as AzureAiTM. To proactively defend against these threats, a multi-faceted approach is essential. This includes prioritizing comprehensive user education and training programs. Concurrently, implementing phishing-resistant authentication mechanisms and rigorously testing and fine-tuning Conditional Access Policies will significantly strengthen access controls. Finally, integrating and deploying advanced solutions like Blackpoint’s Cloud Response will provide critical capabilities for rapid detection and mitigation in cloud environments.