Q2 2025 SOC Insights
The cybercriminal landscape in Q2 2025 has not slowed down and organizations worldwide have continued to face critical threats. Despite disruptions, reported internal conflict, and groups targeting each other, ransomware operations continue to cause chaos and other cybercriminals continue to adapt to detections, improve malware capabilities, and identify ways to continue operations. Blackpoint’s Security Operations Center (SOC) is no stranger to these attacks, with our team continuing to respond 24/7 to threats facing our partners, consistently thwarting attempts to gain persistence, move laterally, and deploy malware throughout the second quarter of 2025.
From April 01 to June 30, 2025, Blackpoint’s SOC responded to a total of 7,368 incidents across on-premises, Microsoft 365, and Google Workspace protected environments. In this blog, we’ll dive into the two most prevalent threats Blackpoint’s SOC has observed in the second quarter of 2025 – rogue ScreenConnect installs and NetSupport RAT – why they matter for our partners, and possible mitigations using your existing tech stack alongside Blackpoint Cyber’s managed services.
Q2 High-Level Overview
From April 01 to June 30, 2025, Blackpoint’s SOC responded to incidents impacting nearly every vertical; however, the top three verticals targeted within incidents observed include:
- Technology (MSP)
- Industrials (Manufacturing)
- Healthcare
Critical infrastructure verticals, such as Technology, Manufacturing, and Healthcare are attractive targets for threat actors for several reasons, including
- The amount of sensitive data these organizations maintain,
- The profit these organizations are perceived to have available,
- The inability to suffer significant downtime, making the impact of a successful attack detrimental.
These factors make these industries attractive targets for all levels of threat actors including ransomware operators, information stealing groups, and initial access brokers (IABs). It is likely these verticals will continue to be primary targets for threat actors over the next 3-6 months.
Rogue ScreenConnect
ScreenConnect is a legitimate remote access tool widely used by organizations to remotely access machines and is an attractive option due to its ease of deployment and minimal configuration requirements. ScreenConnect enables full control of endpoints, the deployment of malicious payloads, lateral movement across networks, encrypted communication, persistent access, and operates in the background. These factors also make it an attractive tool for threat actors as it does not typically raise red flags. ScreenConnect serves as an initial access vector and persistence method due to its legitimacy and low cost – making it easy to adopt and harder for organizations to detect.
Blackpoint’s SOC observed a significant increase in incidents involving the use of Rogue ScreenConnect instances. Blackpoint’s SOC identified and responded to 53 total incidents in the Rogue ScreenConnect campaign from April to June 2025, impacting 11 different verticals.
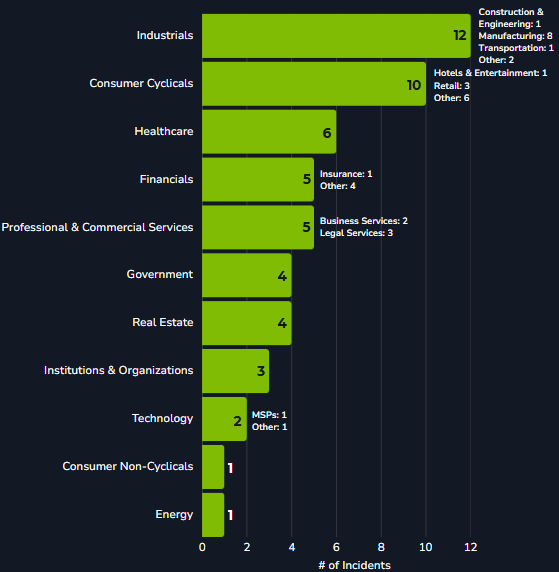
Figure 1: Verticals impacted by Rogue ScreenConnect campaign
Threat actors were observed weaponizing ClickOnce for stealthy, no-admin installs of the ScreenConnect tool. The user is typically targeted with a social engineering attack, such as phishing, malvertising, or fake browser update prompts to click a link. The following a successful social engineering attack, the following steps often take place:
- The malicious link points to a .application ClickOnce manifest file hosted on attacker infrastructure.
- The ClickOnce application installs a pre-configured ScreenConnect client;
- The rogue ScreenConnect instance establishes outbound C2 connection to the attacker and can be configured for auto-reconnect on boot.
ClickOnce is a living-off-the-land binary (LOLBins) for stealthy remote access and threat actors have been observed utilizing it to silently drop and persist rogue ScreenConnect clients without tripping common alerts. The scale and frequency of these attempts to indicate a coordinated effort to establish persistence on compromised networks. These incidents were likely a precursor to data theft, further lateral movement, or ransomware deployment. These installs grant full access to the user environment and could serve as launchpads for broader compromise across networks.
Blackpoint’s SOC continues to monitor threat actor’s use of LOLBins and the use of rogue software installed within managed environments. The use of Blackpoint’s Managed Application Control (MAC) can ensure that unapproved tools are blocked when install attempts are made.
NetSupport RAT
Over the previous quarter, Blackpoint’s SOC has continued to identify and thwart incidents related to the ongoing Fake CAPTCHA campaign. This campaign directs users to pages that mimic CAPTCHA verifications and luring victims into copying scripts and executing them, effectively deploying malware within the compromised environments. Blackpoint’s SOC has successfully stopped 96 attempted Fake CAPTCHA incidents during Q2, with more than 30% of these being an attempt to download the NetSupport RAT.
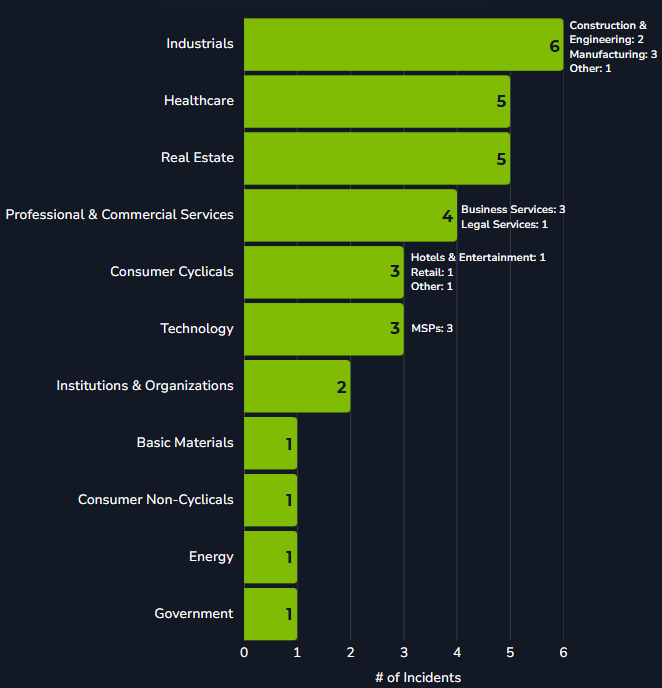
Figure 2: Verticals impacted by NetSupport RAT Fake CAPTCHA April 01 – June 30, 2025
In these incidents specifically, victims are directed to a legitimate website that has been compromised and is hosting malicious JavaScript. The victim is presented with a fake CAPTCHA prompt and is instructed to press Win + R and paste the command into the Windows Run dialog box. The victim then effectively deployed the NetSupport RAT payload onto their own machine. Blackpoint has published a detailed blog related this activity.
NetSupport RAT is a legitimate remote support tool that is frequently abused by threat actors for illicit purposes. NetSupport RAT maintains the ability to transfer files, provide persistent remote access, perform keylogging, and control system resources – these abilities make this an attractive tool for malicious purposes.
Due to the widespread use and availability for both malicious and legitimate use cases, the use of NetSupport RAT cannot be attributed to a single threat actor/group. The use of NetSupport RAT leads to a variety of initial access methods; however, social engineering appears to remain a top choice for deploying this tool.
Conclusion
Blackpoint’s APG assesses that it is very likely that threat actors will continue to deploy legitimate tools, including ScreenConnect and NetSupport RAT, for malicious purposes through the second half of 2025. This assessment is based on the frequency of SOC-observed incidents and external reporting related to the use of these tools.
Threat actors find both ScreenConnect and NetSupport RAT attractive because they’re widely used by legitimate IT teams and can often evade basic security tools due to the legitimate status. Once deployed, these tools allow adversaries to control systems, disable protections, exfiltrate data, and stage further attacks. Both of these tools are often reported to be used by threat actors of all levels, including ransomware operations.
With malware operators increasingly turning to living-off-the-land (LotL) techniques, it is imperative for users to remain vigilant against social engineering tactics and for organizations to be aware of rogue installs of trusted software. Implementing Blackpoint’s Managed Application Control (MAC) offering can be particularly effective against these threats. Restricting which binaries are allowed to execute can prevent unauthorized instances of NetSupport Manager and other remote access tools from launching.
Blackpoint’s SOC has repeatedly identified and prevented these types of attacks throughout the second quarter of 2025 and will continue to thwart these threat actors from successfully targeting our partners. Blackpoint’s SOC and APG will continue to monitor the threat landscape and keep our partners up to date on the current threats.