Q3 2025 SOC Insights
This quarter, 01 July – 30 September 2025, underscored that critical infrastructure sectors remain prime targets for a wide range of threat actors. These industries continue to attract attention due to their high operational impact, valuable data, and limited tolerance for downtime, making them ideal candidates for extortion-drive operations. Throughout the quarter, Blackpoint’s Security Operations Center (SOC) team identified an increase in pre-ransomware activity, exploitation of edge devices, and the use of remote access trojans (RATs) as precursors to larger campaigns.
From July 01 to September 30, 2025, Blackpoint’s SOC responded to nearly 7,000 incidents across on-premises, Microsoft 365, and Google Workspace protected environments. In this blog, we’ll dive into some of the trends Blackpoint’s SOC observed in the third quarter of 2025, why they matter for our partners, and possible mitigations using your existing tech stack alongside Blackpoint Cyber’s managed services.
Q3 High-Level Overview
From July 01 to September 30, 2025, Blackpoint’s SOC responded to incidents impacting nearly every vertical; however, the top three verticals targeted within incidents observed include:
- Industrials (Manufacturing)
- Healthcare
- Technology (MSP)
Critical infrastructure verticals, such as Manufacturing, Healthcare, and Technology are attractive targets for threat actors for several reasons, including
- The amount of sensitive data these organizations maintain,
- The profit these organizations are perceived to have available,
- The inability to suffer significant downtime, making the impact of a successful attack detrimental.
These factors make these industries attractive targets for all levels of threat actors including ransomware operators, information stealing groups, and initial access brokers (IABs). It is likely these verticals will continue to be primary targets for threat actors over the next 3-6 months.
Pre-Ransomware Activity
Blackpoint’s Adversary Pursuit Group (APG) team reviews SOC-observed incidents for accurate tracking, categorization, and, where possible, attribution. During this review, Blackpoint’s APG identifies incidents that are very likely precursors to ransomware activity.
This determination is based on observed behavioral indicators, tools deployed, and alignment with well-known ransomware tactics, techniques, and procedures (TTPs). While there is an even chance that additional SOC-observed incidents during Q3 2025 may have had the potential to escalate into ransomware, the number of incidents highlighted here have been specifically identified as reconnaissance, persistence, lateral movement, or staging activity consistent with ransomware deployment.
Most importantly, all these incidents were disrupted prior to the execution of malware or ransomware payloads.
SOC-observed incident Review
In August 2025, Blackpoint’s SOC detected a privileged remote execution of a malicious file from a device that did not have a SNAP agent installed. Additionally, another alert was triggered for the execution of an encoded PowerShell command. Further investigation revealed that a command was executed that was designed to silently create a new local Windows user account redirecting all output and errors to a hidden file. The execution chain exhibited behavior consistent with Impacket’s WMIExec tool.
Blackpoint’s SOC identified an account that was observed attempting to mount shares across multiple devices. Additionally, SOC determined that an SSL VPN appliance was publicly accessible, which likely served as the initial access vector. Blackpoint’s SOC isolated all impacted servers, effectively thwarting what would likely be an attempt to deploy ransomware.
The observed tactics—including use of an exposed VPN appliance, privileged account misuse, and WMIExec-style execution—align with common pre-ransomware activity. This underscores the urgency of closing visibility gaps; ensuring comprehensive deployment of SNAP agents across all endpoints significantly enhances SOC’s ability to detect and disrupt pre-ransomware operations before threat actors can establish persistence or deploy malicious tooling within the network.
Throughout Q3 2025, Blackpoint’s SOC responded to 74 incidents that have been assessed to be related to pre-ransomware activity.
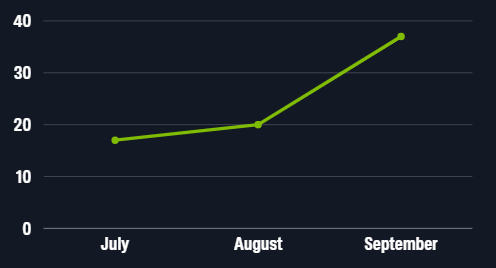
Figure 1: SOC-observed pre-ransomware incidents 01 July – 30 September 2025
These incidents increased 85% from August to September, which was likely due to a significant increase in targeting of SSL VPN appliances by multiple threat actors, including Akira, Play, and Qilin operations. Along with pre-ransomware activity, Blackpoint’s SOC has been actively tracking the ongoing activity related to the targeting of SonicWall appliances since July 2025.
Blackpoint released a threat bulletin related to the activity on August 03, 2025 and the activity was reviewed in SOC’s Beyond the Alerts episode on September 10, 2025. Additionally, external research supports the assessment of this activity being linked to likely ransomware activity.
These devices are attractive targets for threat actors, including ransomware operators, because they serve as the front door to an organization’s network, controlling and filtering all traffic between internal systems and the internet. Their constant exposure, combined with their privileged position, making them highly valuable to threat actors. Compromising an edge device like a firewall or VPN gateway can grant attackers deep visibility, remote access, or control over sensitive network flows. These devices often suffer from delayed patching due to operational constraints and misconfigurations/weak credentials remain common.
Remote Access Trojans
Over the previous quarter, Blackpoint’s SOC has excelled at identifying and thwarting incidents related to the deployment of remote access trojans (RATs). A RAT is a type of malware that allows an attacker to remotely control an infected device by creating a backdoor int the system, giving the attacker unauthorized administrative access. RATs provide threat actors with numerous capabilities on a compromised device including, but not limited to:
- Capturing keystrokes allowing them to collect passwords and other sensitive information.
- Using screen capture and abuse the webcam to watch the user in real time, potentially activating the microphone to record conversation.
- Access, browsing, copying, deleting, and downloading files from the infected device.
- Modifying system settings, which can provide additional persistence and the ability to install additional payloads – external research found that the deployment of RATs are a top indicator of pre-ransomware activity
- Using the compromised device to pivot deeper in the network to other valuable targets within the environment.
SOC-observed incident Review
In September 2025, Blackpoint’s SOC alerted to suspicious PowerShell execution by an end user with a Healthcare partner. Further investigation found the PowerShell was calling out to a suspicious URL to grab the contents ofa file and execute the malicious code into memory. The execution of the PowerShell script created a staged directory and dropped the NetSupport RAT. The infection chain observed was indicative of the end user falling for a fake CAPTCHA attack. As a result of the suspicious activity, Blackpoint’s SOC isolated the impacted machine and reached out to the partner.
This incident illustrates how quickly a simple social engineering lure can escalate into a potential full-blown compromise if not detected and contained. Security controls and SOC’s intervention broke the attack chain before it reached that stage, demonstrating the tangible value of layered defenses, rapid detection, and skilled analysts in preventing what could have been a business-impacting incident.
In Q3 2025 (July 01 – September 30, 2025), 13.9% of SOC-observed incidents involved the identification of a RAT malware. The three most observed variants this quarter included:
- NetSupport RAT – a legitimate remote access tool that has been adopted by malicious actor to target organizations and steal sensitive information including screenshots and files; and has the ability to deploy second stage payloads
- AsyncRAT – an open-source remote access tool that has been used in malicious campaigns to deploy second-stage payloads, harvest system information, and gain persistence
- Interlock RAT – a remote access trojan (RAT) that is distributed by the Interlock Ransomware group and provides attackers with unauthorized remote control over a compromised computer system, enabling data theft and further attacks.
The deployment of the Interlock RAT aligns with external reporting of the malware being deployed as part of the ClickFix and FileFix campaigns.
These incidents most frequently impacted the financials, healthcare, and institutions & organizations industries. In August 2025, Blackpoint published a blog related to an increase in observed impacts to the institutions & organizations industry. These industries host a gold mine of customer data, are critical to the operation of the economy, and have a significant downstream impact if successfully targeted – all making them attractive target for threat actors deploying RATs.
Conclusion
Blackpoint’s APG assesses that it is very likely that ransomware operators will continue to target all industries worldwide over the next 12 months; by understanding the most common behaviors and tools, identifying incidents prior to the deployment of a ransomware payload becomes possible. This assessment is based on the frequency of SOC-observed incidents and eternal reporting related to the identification of pre-ransomware incidents and ransomware operators’ TTPs.
Additionally, Blackpoint’s APG assesses that it is very likely that threat actors will continue to deploy RATs in an attempt to gain persistence on compromised devices, including legitimate tools like NetSupport RAT. This assessment is based on SOC-observed incidents involving the identification of RATs and reporting indicating the frequency of RATs in reported incidents.
Blackpoint’s SOC has repeatedly identified and prevented these types of attacks throughout the third quarter of 2025 and will continue to thwart these threat actors from successfully targeting our partners. Blackpoint’s SOC and APG will continue to monitor the threat landscape and keep our partners up to date on the current threats.