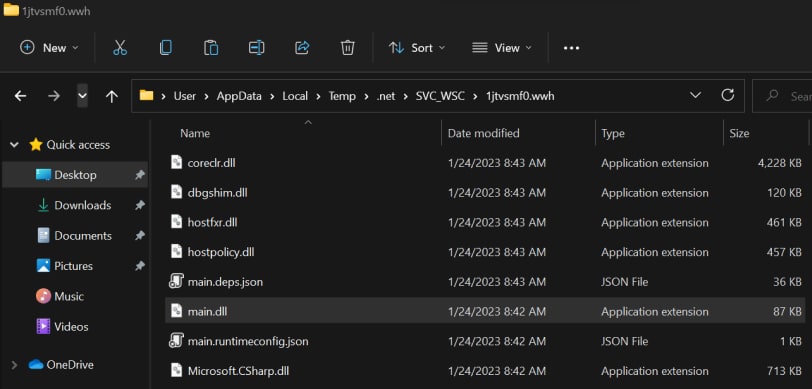
Blackpoint Cyber’s Adversary Pursuit Group (APG) and Security Operations Center (SOC) analyzed a recent attack conducted by the Lorenz ransomware group. Lorenz has been active in the wild since early 2021 and is known to leverage a vulnerability in MiVoice Connect (CVE-2022-29499), one of many Mitel Voice-over-IP (VoIP) products that are used by organizations in critical sectors worldwide. This is done in order to exfiltrate data using FileZilla and encrypt data using Microsoft’s BitLocker Drive Encryption. The attack method involves a double extortion technique, requesting payment for decryption and destructing exfiltrated data from their leak site. It appears Lorenz targets larger, English-speaking, enterprise environments and requests a ransom between $500,000 and $700,000. During the SOC’s analysis of the incident, they were able to recover the malicious executable used to launch the encryption phase of the attack.
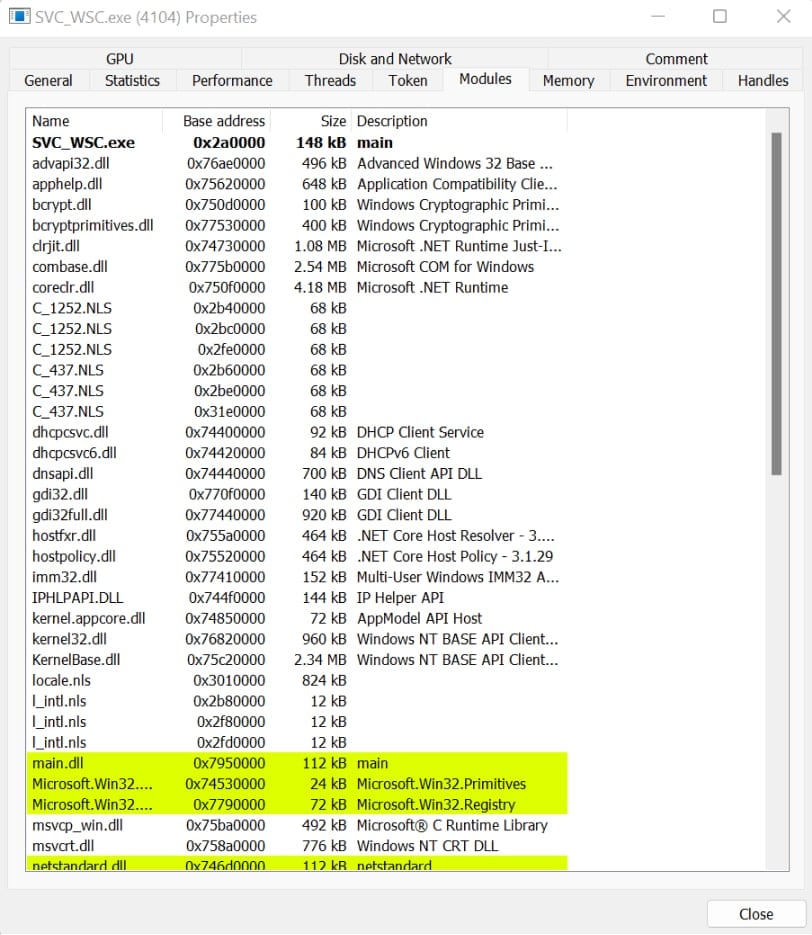
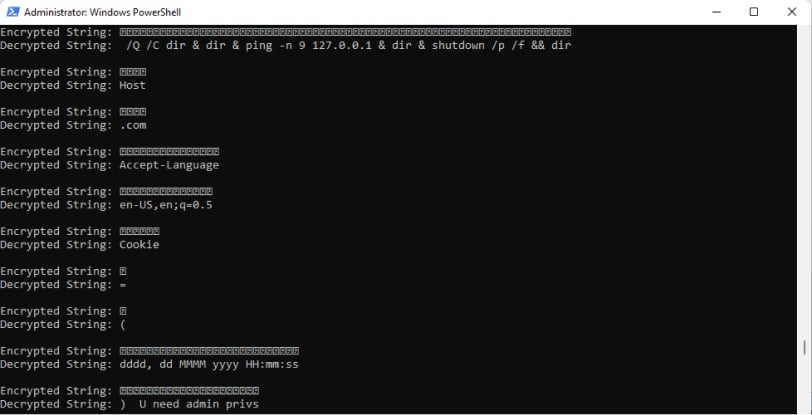
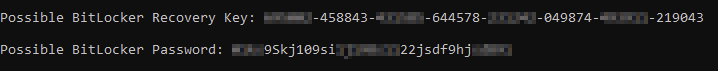
The APG analyzed the malicious executable, SVC_WSC.exe, and discovered the extraction and use of .NET Core and custom .NET dynamic link libraries (DLLs). This allows for the execution of the final BitLocker encryption payload instead of PowerShell, which has been seen in previous attacks. The switch to .NET Core DLLs is concerning because it is harder to detect and is a cross-platform framework, meaning the ransomware group could be targeting a wider variety of operating systems (OSs). APG also discovered the use of a hardcoded BitLocker recovery key, BitLocker password, and victim domain information, indicating the attack was targeted rather than a randomized widespread attack.