Vulnerability Review – April 2025
This blog is a recap of the most critical vulnerabilities disclosed in April 2025 that most likely impact software utilized by managed service providers (MSPs). While not all MSPs use the software discussed in this blog, the software has been labeled as a priority software by Blackpoint’s APG due to the overall number of MSPs and other organizations that use it.
Key Findings
- There were more than 4,000 vulnerabilities disclosed in April 2025; with more than 1,900 vulnerabilities being scored with a high or critical Common Vulnerability Scoring System (CVSS) rating.
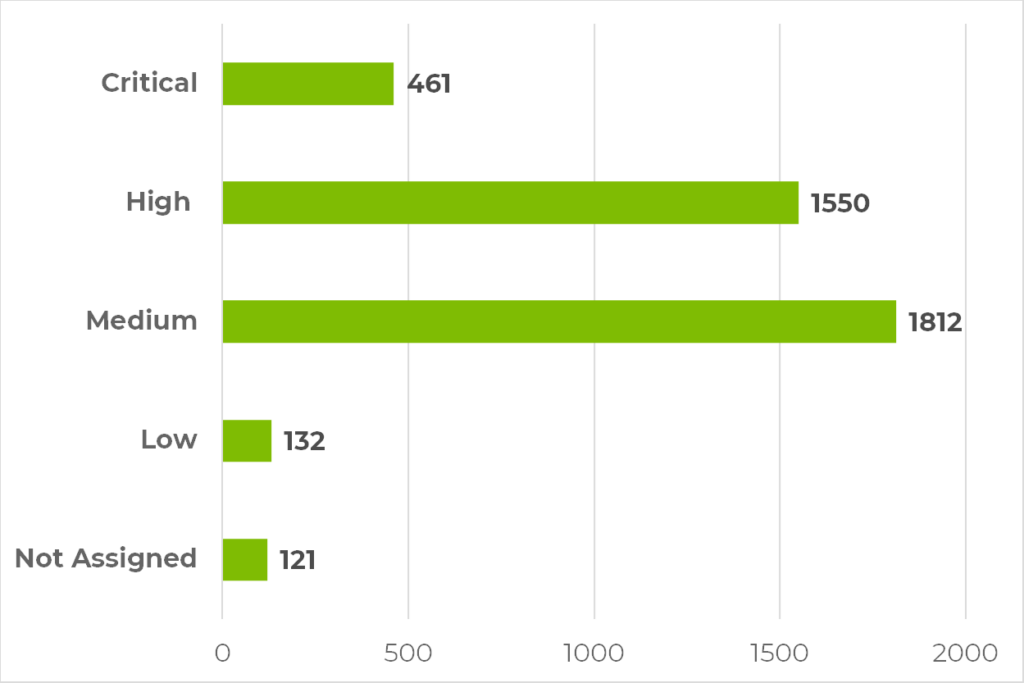
- Several that have been actively exploited, and 11 of the high and critical vulnerabilities were added to the U.S. CISA Known Exploited Vulnerabilities (KEV) Catalog, indicating reliable reports of active exploitation.
- Blackpoint’s APG assesses with high confidence that threat actors will continue to leverage known and unknown vulnerabilities in ubiquitous software and services over the next 12 months.
Blackpoint’s APG Analysis
Blackpoint’s APG assesses with high confidence that threat actors will continue to target, or begin targeting, these vulnerabilities over the next 12 months to deploy malware, steal sensitive information, and gain unauthorized access to organizations. It is likely that these vulnerabilities will be targeted by multiple types of threat actors, including both nation-state and financially motivated threat actors over the next 12 months.
Vulnerabilities
Enterprise Software
Enterprise software solutions are essential to business operations and are frequently targeted by threat actors due to the level of access, as well as the ability to deploy malware, gain persistence on a network, and move laterally through a compromised environment.
SAP
On April 24, 2025, SAP disclosed a vulnerability, CVE-2025-31324, within SAP NetWeaver’s Visual Composer Metadata Uploader component. CVE-2025-31324 (CVSS 10) is an unrestricted file upload vulnerability, allowing attackers to upload malicious files directly to the system without authorization. The vulnerability impacts the Visual Composer Framework 7.50.
CVE-2025-31324 could allow threat actors to upload malicious executable files without logging in, potentially leading to remote code execution and/or full system compromise. The vulnerability has been actively exploited and was added to the U.S. CISA’s KEV Catalog on April 29, 2025.
Fortinet
On April 8, 2025, Fortinet released security patches for CVE-2024-48887, a critical vulnerability impacting FortiSwitch devices. It consists of an unverified password change vulnerability in FortiSwitch GUI and impacts versions:
- FortiSwitch 7.6.0
- FortiSwitch 7.4.0 through 7.4.4
- FortiSwitch 7.2.0 through 7.2.8
- FortiSwitch 7.0.0 through 7.0.10, and
- FortiSwitch 6.4.0 through 6.4.14
CVE-2024-48887 can be exploited in low-complexity attacks that don’t require user interaction, and it could allow an attacker to change credentials using a specially crafted request sent via the set_password endpoint.
At the time of writing, there is no confirmed exploitation of this vulnerability.
Backup & Recovery Management
Backup & Recovery Management software is a critical type of software that protects data and systems by creating copies and providing tools to restore them in case of data loss or system failure. These devices are critical to ensuring business continuity for both intentional and unintentional threats. Threat actors frequently target this type of software because it is typically the last line of defense for an organization and by successfully targeting them, threat actors can conduct devastating attacks.
Targeting this type of software can enable threat actors to destroy recovery options, gain privileged access to sensitive data, steal stored credentials, and potentially gain access to other victim organizations.
Commvault
On April 11, 2025, Commvault released an advisory warning of a critical vulnerability, CVE-2025-34028 (CVSS 9.0), impacting the Command Center. CVE-2025-34028 is a Server-Side Request Forgery (SSRF) vulnerability in Commvault Command Center Innovation Release. The issue is rooted in an endpoint called “deployWebpackage.do,” triggering what’s called a pre-authenticated SSRF because there is no filtering as to what hosts can be communicated with. This vulnerability impacts only the 11.38 Innovation Release, from version 11.38.0 through 11.38.19. The vulnerability has been resolved in versions 11.38.20 and 11.38.25.
CVE-2025-34028 can be exploited to allow threat actors to conduct arbitrary code execution on affected installations and could lead to a complete compromise of the Command Center environment.
This vulnerability was added to the U.S. CISA’s KEV Catalog on May 02, 2025, indicating reliable reports of active exploitation.
File Sharing Software
File sharing software enables organizations to store files on a server and transfer them to a computer, another user, or another server. This type of software is frequently used by MSPs to enable secure remote access, collaboration, and data mobility across client environments. Threat actors often target this type of software because it allows widespread access to sensitive information, can provide threat actors an opportunity to elevate privileges, gather credentials, and move laterally; and can be utilized to exfiltrate data that can be sold or used for extortion purposes.
The most well-known targeting of this type of software has been conducted by the Clop Ransomware operation. This group has consititently targeted zero-day vulnerabilities in file transfer protocol (FTP) software, including Cleo, MoveIT, GoAnywhere, and more since at least 2020.
Gladinet CentreStack
On April 03, 2025, Gladinet disclosed a vulnerability, CVE-2025-30406 (CVSS 9.8) impacting CentreStack and Triofox servers. The vulnerability is a deserialization vulnerability due to the CentreStack and Triofox portal’s hardcoded machineKey use. The vulnerability impacts Gladinet CentreStack through version 16.1.10296.56315 and TrioFox below version 16.4.10317.56372.
Exploitation of this deserialization vulnerability provides a threat actor remote code execution against the host running CentraStack or Triofox. Threat actors are leveraging this remote execution to enumerate the targeted host and Active Directory Environment. The vulnerability has been reported to be actively exploited since at least March 2025; the vulnerability was added to the U.S. CISA’s Known Exploited Vulnerabilities (KEV) Catalog on April 08, 2025.
CrushFTP
On March 21, 2025, a critical CrushFTP vulnerability, CVE-2025-31161 (CVSS: 9.8), was reported and has been actively exploited. This vulnerability was originally reported as CVE-2025-2825; however, it is important to note that this CVE has been rejected as it is a duplicate of CVE-2025-31161. The vulnerability is an authentication bypass vulnerability that allows attackers to gain unauthorized access due to parameter overloading in lookup_user_pass boolean flag. The vulnerability impacts CrushFTP versions 10.0.0 through 10.8.3 and 11.0.0 through 11.3.0.
There have been multiple reports of active exploitation of this vulnerability, which allows threat actors to gain unauthorized access without providing any password. This vulnerability was added to the U.S. CISA’s KEV Catalog on April 07, 2025.
References
DATE PUBLISHEDMay 13, 2025
AUTHORBlackpoint Cyber
SHARE ON
Subscribe to the Blackpoint Blog
Don’t let a lack of awareness leave the organizations you protect vulnerable to sophisticated and elusive attacks. Subscribe now for a weekly roundup of Blackpoint’s empowering articles.
Subscribe now!