Vulnerability Review – May 2025
This blog is a recap of the most critical vulnerabilities disclosed between 01 May and 27 May 2025 that most likely impact software utilized by managed service providers (MSPs). While not all MSPs use the software discussed in this blog, the software has been labeled as priority software by Blackpoint’s APG due to the overall number of MSPs/organizations that use it.
Key Findings
- There were more than 3,600 vulnerabilities disclosed between 01 May and 27 May 2025, with more than 1,400 vulnerabilities being scored with a high or critical Common Vulnerability Scoring System (CVSS) rating
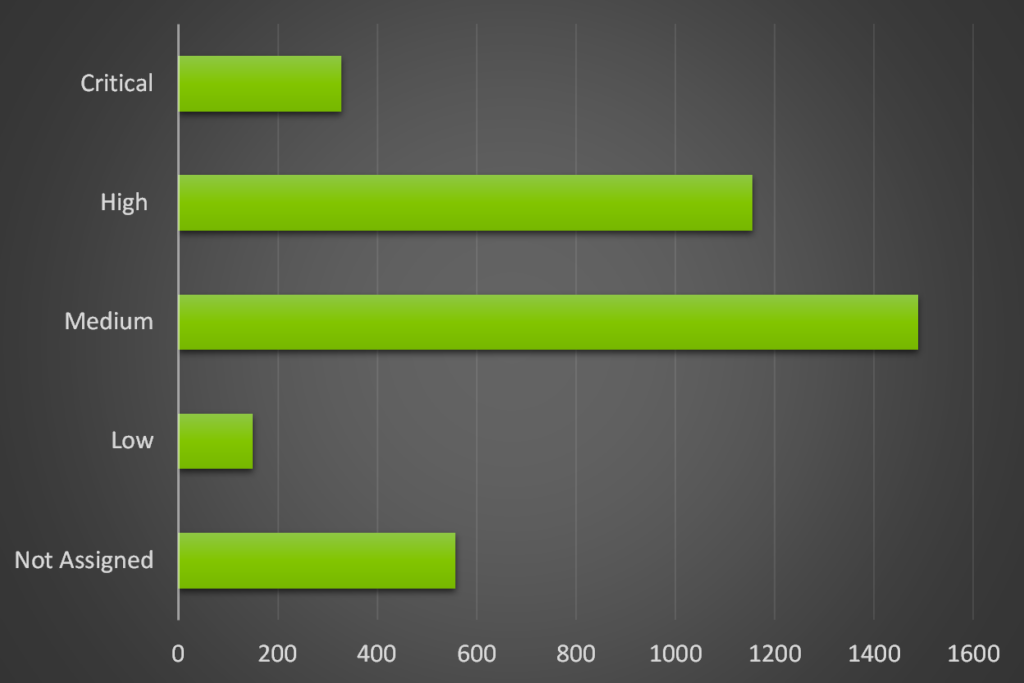
- There are several that have been actively exploited and 25 that have been added to the U.S. CISA Known Exploited Vulnerabilities (KEV) Catalog, indicating reliable reports of active exploitation.
- Blackpoint’s APG assesses with high confidence that threat actors will continue to leverage known and unknown vulnerabilities in ubiquitous software and services over the next 12 months.
Vulnerabilities
Enterprise Software
Enterprise software solutions are essential to business operations and are frequently targeted by threat actors due to the level of access, the ability to deploy malware, gain persistence on a network, and the ability to move laterally through a compromised environment.
SAP
SAP disclosed a vulnerability, CVE-2025-42999, within SAP NetWeaver. This comes shortly after SAP disclosed another vulnerability, CVE-2025-31324, in SAP NetWeaver in April 2025; more information on this vulnerability can be found in April’s Vulnerability Recap blog.
CVE-2025-42999 is a deserialization vulnerability that could allow attackers to execute arbitrary commands. Security researchers reported that these two reported vulnerabilities were chained together to target victim organizations and provide the attackers with remote code execution.
This vulnerability was added to the CISA KEV Catalog on May 15, 2025.
VMware
In May 2025, VMware disclosed seven vulnerabilities in various products that could lead to authenticated remove code execution (RCE), denial of service (DoS), information disclosure, and more. The vulnerabilities include:
- CVE-2025-41225: Authenticated RCE via alarm scripts in vCenter Server that allows arbitrary command execution with alarm privileges
- CVE-2025-41226: Authenticated DoS via Guest Operations in ESXi that causes service disruption but no code execution
- CVE-2025-41227: DoS from guest users on Workstation, Fusion, ESXi that is exploitable by non-admins inside VMs
- CVE-2025-41228: Reflected XSS in ESXi/vCenter web interface that requires interaction
- CVE-2025-41229: Directory Traversal in VMware Cloud Foundation that could allow access to internal services
- CVE-2025-41230: Information Disclosure via Endpoint in VMware Cloud Foundation that could allow access to sensitive information
- CVE-2025-41231: Missing Authorization in VMware Cloud Foundation that could allow a threat actor to perform certain unauthorized actions and access sensitive information
VMware products are critical software/solutions that enable internal and external communication, file and data hosting, management, storage, and sharing. Targeting this type of environment can enable threat actors to exfiltrate data, install persistence malware or ransomware, harvest credentials, and map out other areas of a compromised network.
Browsers
Browsers, such as Google Chrome, Microsoft Edge, and Mozilla Firefox/ESR, are often attractive targets for threat actors due to the user-level privileges these run with, sit at the intersection of user interaction and the internet, and the large attack surface. Targeting browsers can allow threat actors to access and steal browser-stored credentials, execute code on the system; and escape browser-based protections and sandboxing to access the operating systems.
Google Chrome
Google released an emergency update for the Chrome browser to patch a critical vulnerability, CVE-2025-4664. CVE-2025-4664 is an insufficient policy enforcement in the Chrome Loader component, which handles resource requests. The vulnerability is caused by the security policies not being applied properly to Link headers.
When a user visits a website related to sensitive information, the URL may include a secret code as proof of the user’s legitimacy. Due to this vulnerability, a threat actor can trick your browser into sending a secret code to a malicious website by embedding an image or other resource there. The threat actor can then harvest the full URLs allowing them to steal private information without the victim’s knowledge.
This vulnerability was added to the CISA KEV Catalog on May 15, 2025.
Network Edge Devices
Network edge devices – firewalls, routers, VPN gateways, etc. – are the critical gatekeepers between internal networks and the internet. These devices manage and filter traffic, enforce security policies, and often provide remote access capabilities making them high-value targets for threat actors.
Threat actors can exploit these devices to bypass perimeter defenses, capture traffic, pivot deeper into the network, establish persistence, or deploy malware while evading detection. Edge devices often operate with elevated privileges and are typically exposed to the internet, they’re frequently targeted via vulnerabilities, exposed devices, or misconfigurations.
SonicWall
SonicWall disclosed a series of vulnerabilities impacting SonicWall Secure Mobile Access that enable privilege escalation and remote code execution as root user. The vulnerabilities impact SMA 200, SMA 210, SMA 400, SMA 410, and SMA 500v devices. The vulnerabilities include:
- CVE-2025-32819 enables threat actors to delete the primary SQLite DB, reset the password of the default SMA admin account, and log in with that user on the web interface.
- CVE-2025-32820 is a path traversal vulnerability enabling the attacker to make the /bin directory writeable.
- CVE-2025-32821 enables the attacker to gain RCE as root.
The attacker does require a valid set of credentials, access to the login portal, and for SMA to be present with the vulnerable versions.
While these vulnerabilities have not been added to the CISA KEV catalog, the agency did add an older vulnerability, CVE-2023-44221 impacting SMA100 appliances to the catalog indicating that these products are attractive targets for threat actors, even several years after vulnerabilities are disclosed.
Identity and Access Management (IAM)
Identity and access management (IAM) products are systems that control who can access what within an organization’s digital environment. These products handle authentication and authorization, managing everything from user accounts and passwords to single sign-on (SSO), multi-factor authentication (MFA), and privileged access. Threat actors can exploit these devices to impersonate users, elevate privileges, bypass security controls, and move laterally across networks. Threat actors can target these devices to takeover accounts, exfiltrate data, gain persistence, and deploy malware.
Samlify
Security researchers disclosed a critical vulnerability, CVE-2025-47949, impacting Samlify, a high-level authentication library, versions prior to 2.10.0. It is frequently used for building or connecting to identity providers and service providers using SAML.
CVE-2025-47949 is an authentication bypass vulnerability due to a SAML wrapping flaw. Samlify correctly verifies that the XML document providing a user’s identity is signed but still proceeds to read fake assertions from a part of the XML that isn’t.
Threat actors holding a valid signed SAML response through interception or via public metadata can modify it to exploit the parsing flaw in the library and authenticate as someone else. Threat actors can then completely bypass SSO, allowing unauthorized access where threat actors can perform privilege escalation and log in as administrators.
Blackpoint’s APG Analysis
Blackpoint’s APG assesses with high confidence that threat actors will continue to target, or begin targeting, these vulnerabilities over the next 12 months to deploy malware, steal sensitive information, and gain unauthorized access to organizations. It is likely that these vulnerabilities will be targeted by multiple types of threat actors, including both nation-state and financially motivated threat actors over the next 12 months.
Additionally, as observed with the SonicWall vulnerability, it is likely that threat actors will continue to target older (2+ years) vulnerabilities in widely used software over the next 12 months to gain initial access, persistence, elevate privileges, and deploy malware.