When Good Causes Become Big Targets: The Rise in Attacks on Mission-Driven Organizations
In the first half of 2025, Blackpoint’s APG team has tracked an increase in targeting of organizations in the Institutions & Organizations industry. The Institutions & Organizations industry includes religious organizations, civic and social organizations, environmental organizations, charity organizations, and professional organizations. These mission-critical organizations have increasingly become the target of cybercriminal activity, including ransomware, remote access trojans, and the ongoing fake CAPTCHA and rogue ScreenConnect campaigns.
In this blog, Blackpoint’s APG discusses the trends observed, what could be leading to the increase, and why it matters.
Blackpoint Observed Increases
Between January 01-July 31, 2025, Blackpoint’s SOC responded to 59 incidents impacting an organization in the Institutions & Organizations industry. While this does not appear to be a large number compared to all incidents, incidents impacting this vertical increased 555% from the same time period 2024 to 2025 (9 to 59).
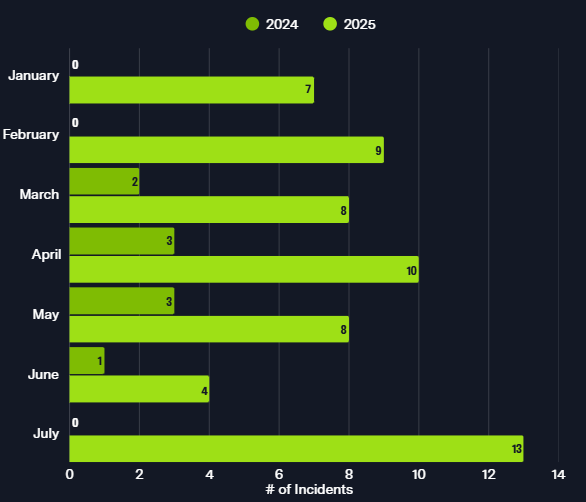
Figure 1: Incidents impacting Institutions & Organizations industry organizations January – July 2025
Blackpoint’s SOC has thwarted threat actor attempts to deploy a variety of malware variants to these organizations, including RuRAT, NetSupport RAT, Lumma Stealer, RedLine Stealer, malicious ScreenConnect instances, SecTopRAT, and more. A significant number of these incidents (30.5%) were related to the Fake CAPTCHA campaign, where a user is tricked into solving a CAPTCHA puzzle to lure victims into downloading malware onto their systems.
Overall Ransomware Landscape
Blackpoint’s APG tracks victim organizations listed on ransomware data leaks sites to maintain insight into the overall ransomware landscape and emerging trends for a comprehensive view of ransomware targeting.
That knowledge is used to ensure we are aware of the larger trends and threats facing our partners each day.
From January 01-July 31, 2025, there were a total of 109 organizations in the Institutions & Organizations industry listed on ransomware data leak sites, up 23.9% compared to 2024 (69).
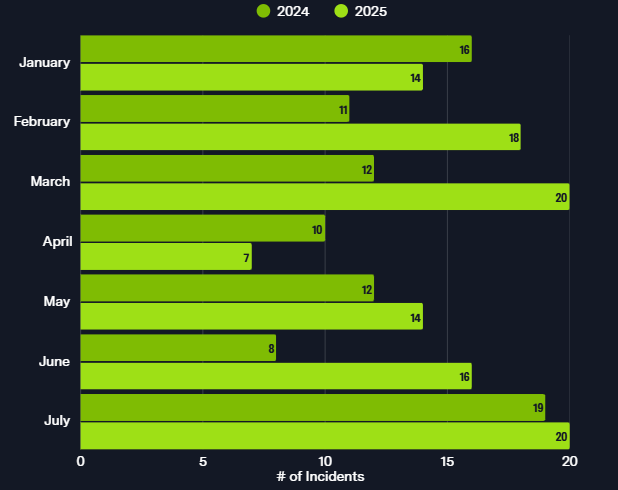
Figure 2: Institutions & Organizations victim organizations listed on ransomware data leak sites January – July 2025
The most active ransomware operations that had listed Institutions & Organizations victims from January 01 – July 31, 2025 were INC Ransom (17), Qilin (14), and SafePay (12).
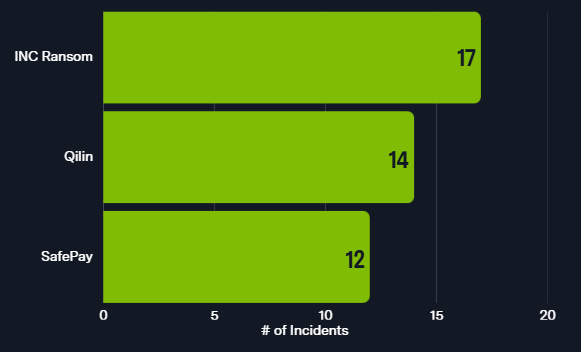
Figure 3: Top 3 operations targeting Institutions & Organizations victims January – July 2025
Why Institutions & Organizations?
There are multiple reasons why threat actors are likely to find these organizations an attractive target for various types of cyber threats, which include:
- Lack of IT budgets and staff: Institutions & Organizations companies often operate on a limited IT budget and a lack of full-time security teams. These factors lead to a lack of endpoint protection, patch management, or even services such as MFA and VPN.
- Type of information: Institutions & Organizations often host a plethora of valuable information, including information related to vulnerable populations and information related to donors. Donor lists are likely a gold mine for threat actors that can be used for follow-on targeting for financially motivated cyberattacks.
- Inability to suffer downtimes: while these organizations have a lower budget than enterprise organizations, they are still considered likely to pay a ransom payment due to the inability to pause services. Many of these organizations provide vital services for vulnerable populations – coupled with a lack of security – they are a prime target for ransomware operators.
- Geopolitical tensions: many of these organizations operate with civil and social services – including human rights – which likely makes them an attractive target for nation-state threat groups. These groups are often reported to target these organizations to harvest data related to services and actions that are opposed by the interested government.
- Increased ideological tensions: organizations linked to advocacy and human rights are likely an attractive target for political ideology groups and hacktivists. These organizations have entered the spotlight as ideological tensions continue to rise, which likely makes them more of a target by groups and individuals with opposing views.
Why now?
Institutions & Organizations companies are not a new concept, with human rights organizations going back decades, and the significant increase of targeting within a year piqued our interest. There are a variety of factors contributing to these organizations being targeted now, some of which overlap with the previous section.
- Economic pressures: As larger organizations get better at thwarting cyber threats and have the ability to invest more money into security; Institutions & Organizations are often under-funded and unable to follow-suit – combined with the inability to suffer downtimes, they are likely viewed as more likely to pay a small to medium ransom payment.
- Geopolitical tensions: Global political activism has increased visibility surrounding Institutions & Organizations involved in civil and social services, which likely puts them on the radar for both financially motivated and nation-state threat actors.
- Ideological tensions: rising politicization and polarization has put these types of organizations in the spotlight, bringing attention to the general public, but also to those that have opposing beliefs. Hacktivists and some nation-state operations aim to disrupt these organizations as a result.
- Threat automation: malware-as-a-service (MaaS) operators are increasingly running scalable, automated global malware campaigns, which are not focused on a single industry but often include hundreds to thousands of organizations. For these campaigns, it doesn’t matter who gets the emails, but rather who clicks – in organizations where training is limited or non-existent and emails appear legitimate, it is more likely to be successful.
Outlook
Without a major change in the defensive posture of these organizations, which requires significant increases in budgets, staffing, and funding, it is likely these organizations will continue to be increasingly targeted by threat actors of all types.
As “big-game hunting” ransomware (enterprise targeting) becomes riskier for ransomware operations with increased law enforcement attention, more ransomware operations are focused more on mid-tier, soft targets. Additionally, as more ransomware operations drop encryption and focus more on extortion-only attacks, it is likely these organizations will increasingly become an attractive target.
With geopolitical tensions and ideological tensions increasing, Institutions & Organizations companies will very likely continue to be targeted for information collection related to humanitarian organizations and disruption campaigns by both nation-state and hacktivist operations.
Outside of ransomware and nation-state activity, it is likely that these organizations will increasingly fall victim to cyberattacks such as Fake CAPTCHA campaigns and malspam campaigns as threat actors increase scalability and automation while large enterprise organizations increase security. Organizations operating on minimal budgets and a lack of staff are more likely to fall victim to social engineering attempts that often lead to the deployment of malware such as NetSupport RAT, AsyncRAT, SocGholish, and more.
Blackpoint’s SOC continues to monitor and action persistence and lateral movement attempts within our managed environments, including those within Institutions & Organizations partners. Additionally, Blackpoint’s Managed Application Control (MAC) can help identify and block unauthorized software installed within the environment, including but not limited to unauthorized remote monitoring and management tools, remote access tools, data exfiltration tools, and more.
Call to Action
The alarming surge in cyberattacks against mission-driven organizations paints a picture of increased targeting. The exponential increase in attacks, coupled with the growing sophistication of threats like ScreenConnect exploitation, fake CAPTCHA attacks, AI-powered phishing, ransomware, and the exploitation of vulnerabilities, highlights the urgency of proactive measures. A multi-layered approach should be considered such as robust employee training to address social engineering and fake CAPTCHA types of scams, vigilant patch management for all remote access tools like ScreenConnect, advanced threat detection, and comprehensive incident response planning.