In the face of the menacing activity by FIN8, the vigilant monitoring and swift response of Blackpoint Cyber’s Security Operations Center (SOC) played a pivotal role in halting the attack in its tracks. The SOC was initially alerted to an RDP connection from an unmonitored, compromised machine, marking the initial red flag of malicious activity. This early detection was instrumental in stopping the threat actor’s movements within the compromised network.
The notorious FIN8 threat group, also known as Storm-0288, has once again demonstrated its tactics, techniques, and procedures (TTPs) in a recent cyberattack. This is a reflection of the group’s consistent effort to refine its malicious toolkit and outmaneuver defensive measures deployed by targeted organizations.
In this recent incident, FIN8 leveraged Remote Desktop Protocol (RDP) from a compromised machine using a hijacked privileged support account, showcasing their adeptness at gaining initial access. This move, detected by the SOC, is consistent with their financially motivated agenda, which primarily targets sectors like hospitality, retail, entertainment, and finance.
Following the initial intrusion, the attackers deployed a network scanning tool, “netscan,” to identify additional targets within the victim’s network, typically aiming to compromise the domain controller. This level of lateral movement emphasizes their methodical approach to escalating privileges and broadening the attack scope.
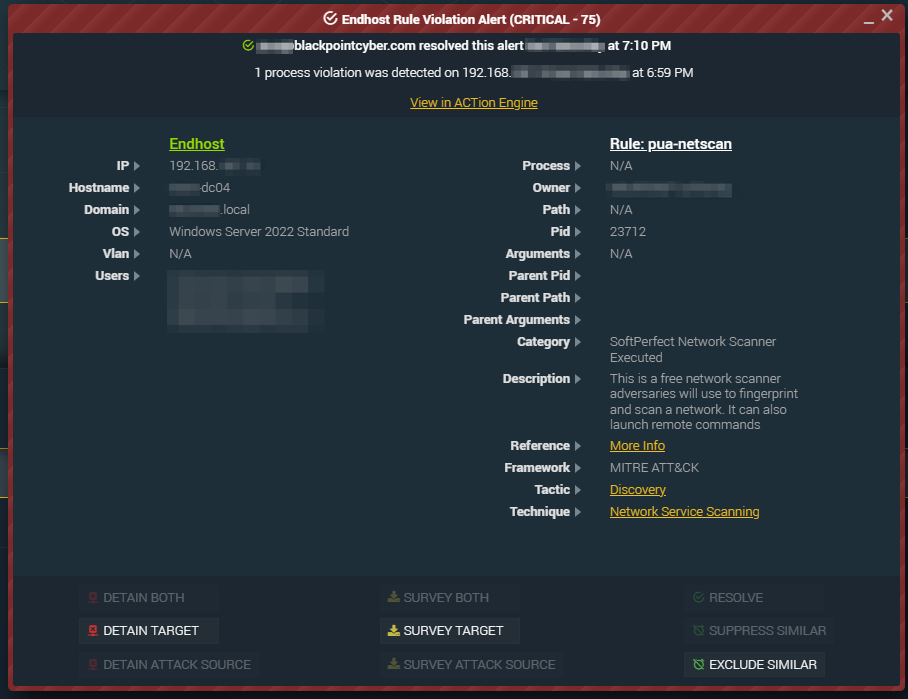
SNAP-Defense alert notifying the SOC of the use of netscan
Furthermore, alerts were triggered at the SOC when remote command execution (RCE) was observed on multiple machines. This was a clear indicator of the threat actor attempting to maneuver through the network and execute malicious commands to further their nefarious agenda.
A significant part of the attack involved running a batch file to disable legitimate Remote Monitoring and Management (RMM) software, hindering the victim’s ability to manage or mitigate the unfolding threat. Coupled with this, they executed a script named ‘C:\Temp\check_users.ps1,’ which, while its exact function remains unclear, potentially assessed user permissions to further their malicious objectives. Additionally, multiple files and folders were extracted into the C:\temp\ directory for further use in their exploitations.
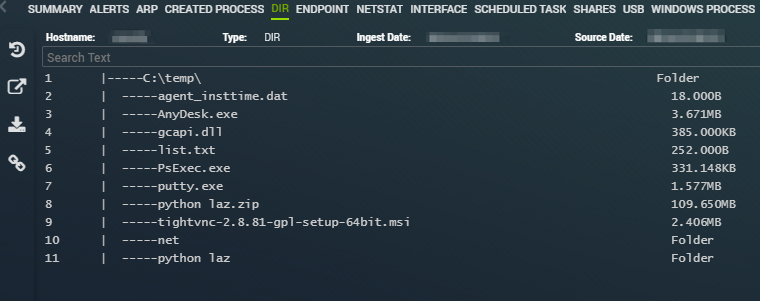
List of items that were found in the C:\temp directory
The primary maneuver involved executing a PowerShell command fetched from a remote server. This script was instrumental in establishing a TightVNC connection back to the threat actors, modifying ‘OneDriveSetup.exe,’ and altering system certificate settings. These modifications not only provided a backchannel for the attackers but also showcased a sophisticated level of system manipulation.
The attackers went on to launch malicious versions of ‘OneDrive.exe’ and ‘FileSyncConfig.exe,’ while also tweaking the registry to enable Remote Desktop, further solidifying their hold on the compromised system. Such actions underscore the multi-faceted threat posed by FIN8, with capabilities spanning from initial access to establishing persistence and command control over the infected systems.
A notable aspect of this attack was the utilization of backchannels like Anydesk and tightVNC for command and control (C2), hinting at a possible use of the Wave EMBASSY Remote Administration Server, although this remains unconfirmed. Such tactics provide robust control over compromised assets, aiding in data exfiltration and further malicious activity.
The decisive and well-coordinated post-incident response by the SOC was paramount in ensuring that the threat was effectively neutralized. They engaged in thorough post-incident procedures which included validating the remaining RMM software to ensure it hadn’t been tampered with, re-imaging compromised devices to eliminate any lurking threats, rotating credentials to lock out the threat actors, and conducting other cleanup operations to restore the network’s integrity.
Reflecting on their historical activities, such as the deployment of Ragnar Locker and White Rabbit ransomware in 2021 and 2022 respectively, it’s evident that FIN8 continues to evolve its TTPs. With significant modifications noted in the Sardonic backdoor, used to deploy Noberus ransomware, their ability to adapt and overcome defensive measures remains a pressing concern.
Cybersecurity professionals must heed the evolving TTPs of FIN8 as indicative of the broader trend among threat actors to refine and adapt their methods. Ensuring up-to-date protective measures, continuous monitoring, and an educated user base are crucial steps in defending against such highly skilled adversaries, safeguarding organizational assets in an increasingly hostile digital landscape.
