In a recent disclosure, Microsoft and the Cybersecurity and Infrastructure Security Agency (CISA) revealed a significant security incident that affected multiple Exchange Online and Outlook.com customers. Unfortunately, the threats may not have stopped there.
According to Microsoft, the incident was linked to a threat actor known as Storm-0558, attributed to China. The attacker obtained a private encryption key (MSA key) and used it to forge access tokens for Outlook Web Access (OWA) and Outlook.com, exploiting vulnerabilities in Microsoft’s token verification process.
Initially, Microsoft’s analysis stated that only Outlook.com and Exchange Online were impacted by the token forging technique. However, researchers from WIZ Research uncovered in their article that the compromised MSA key had more extensive capabilities than previously thought.
The researchers at WIZ Research believe the compromised key had the capability to sign OpenID v2.0 access tokens, which could have allowed the threat actor to forge access tokens for various Azure Active Directory applications, including:
- SharePoint
- Teams
- OneDrive
- applications supporting the “login with Microsoft” functionality
- certain multi-tenant applications
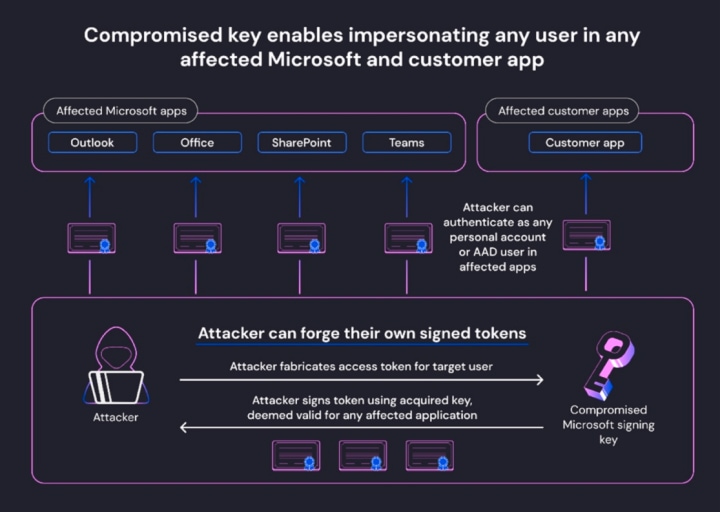
The impact of the incident was substantial, as the compromised key could have allowed unauthorized parties to forge valid access tokens and gain unauthorized access to sensitive information, including email boxes, file services, and cloud accounts.
The incident highlighted the critical importance of identity provider signing keys, which are among the most powerful secrets in the modern world. A compromised signing key for major identity providers like Google, Facebook, or Okta could have severe and wide-ranging consequences.
While Microsoft took action to mitigate the risk by revoking the impacted encryption key and sharing attacker Indicators of Compromise (IOCs), detecting the use of forged tokens against applications proved challenging due to the lack of crucial logs related to token verification.
In response to the incident, Microsoft recommended several steps for Azure users to protect their environments. They advised updating the Azure SDK to the latest version and refreshing the list of trusted certificates to prevent the use of compromised keys for authentication. Users were also encouraged to identify potentially affected applications in their environment and review application-specific logs for signs of token forgery.
As the full extent of the incident remains uncertain due to the lack of comprehensive logs, application owners were urged to take the necessary precautions to secure their systems and prevent unauthorized access.
This incident serves as a wake-up call for the industry and cloud service providers to enhance security measures and transparency concerning the protection of critical keys to prevent future incidents and limit potential impacts on user data and privacy.
Read APG’s original threat notice regarding the incident here.
