In a recent investigation by Doctor Web, an IT security solutions vendor, they have discovered a new multi-component trojan downloader known as Trojan.Fruity.1, which enables threat actors to infect computers with different types of malware based on their malicious goals.
To avoid detection and ensure a successful attack, the attackers have employed various tricks, including multi-stage infection processes, using harmless apps to launch trojan components, and attempting to bypass antivirus protection.
This trojan has been infecting Windows-based computers for the past year with spyware, including the notorious Remcos RAT. To deceive users and distribute the trojan effectively, the threat actors are exploiting legitimate software.
The attack begins with malicious websites hosting specifically crafted software installers, often disguised as tools for fine-tuning:
- CPUs
- graphic cards
- BIOS
- PC hardware-monitoring tools
- other applications
These installers serve as a decoy, luring unsuspecting users into downloading them, containing the Trojan.Fruity.1 downloader alongside the legitimate software.
Once the victim extracts and launches the installer, the standard installation process for the decoy app commences, simultaneously allowing Trojan.Fruity.1 to infiltrate the computer without raising suspicion. The trojan is implanted into legitimate software, such as Python programming-language libraries, VLC media player, and VMWare virtualization software. This technique enables the malware to bypass security measures and remain undetected.
The Trojan.Fruity.1 downloader operates in multiple stages to infect the target system effectively. It decrypts its components from encrypted files, creating an intricate chain of infection. As a part of its complex process, the malware makes use of the steganography method to hide executables and shellcode inside an image file, making detection even more challenging.
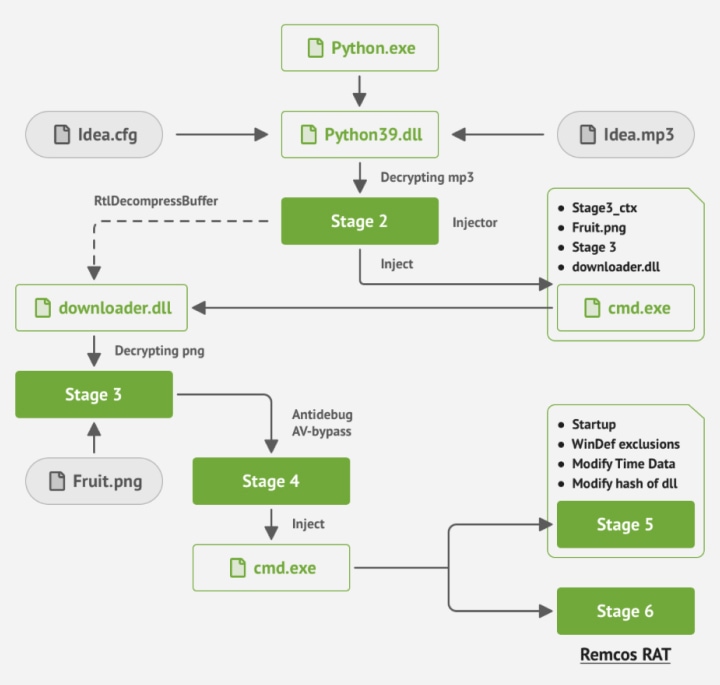
Attack Chain of Trojan.Fruity.1 (Dr.WEB)
The trojan employs various evasion tactics to avoid detection and analysis by security researchers. It attempts to inject itself into trusted processes, such as MSBuild, cmd.exe, and Notepad, using techniques like Process Hollowing and Process Doppelgänging. This allows Trojan.Fruity.1 to replace legitimate processes with its malicious code, ultimately achieving persistence on the infected system.
The ultimate goal of this downloader trojan is to distribute the Remcos RAT spyware, granting threat actors remote access to compromised machines. However, the versatility of Trojan.Fruity.1 means that it can be used to deliver other types of malware, providing cybercriminals with numerous attack possibilities.
In conclusion, the discovery of Trojan.Fruity.1 highlights the evolving tactics used by cybercriminals to distribute malware. By leveraging legitimate software to deliver trojans, threat actors can evade detection and compromise systems effectively. Vigilance and a robust cybersecurity posture are essential to protect against these sophisticated threats in the digital landscape.
