An uncovered security vulnerability in Windows allows threat actors to sign and load malicious kernel-mode drivers using expired or pre-2015 certificates. These actors leverage open-source tools to alter the signing date of drivers, bypassing Windows’ certificate policies.
The majority of the observed drivers have metadata indicating Simplified Chinese language code, suggesting they are frequently used by native Chinese speakers according to Cisco Talos.
The Windows operating system consists of two layers, user mode and kernel mode. Kernel-mode drivers facilitate communication between these layers and allow access to the system’s underpinnings. Exploiting a malicious driver can compromise the system by bypassing the security barrier between user and kernel modes.
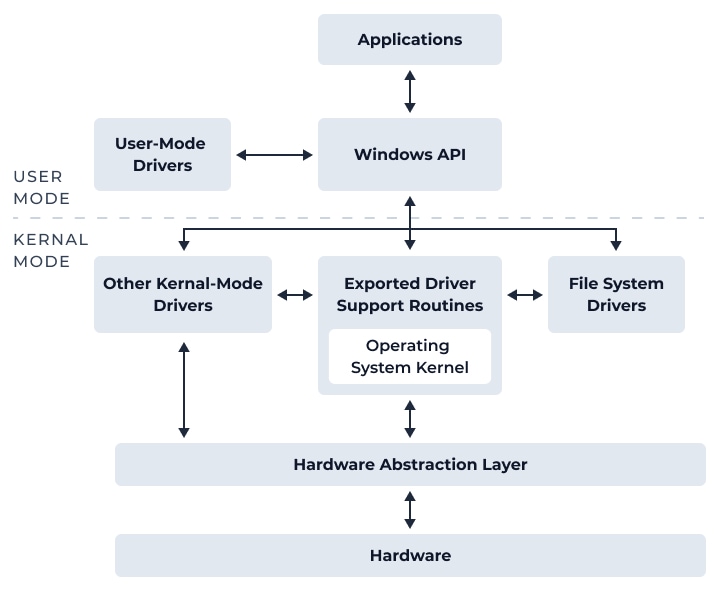
Windows Kernel Architecture. Credit: Microsoft
