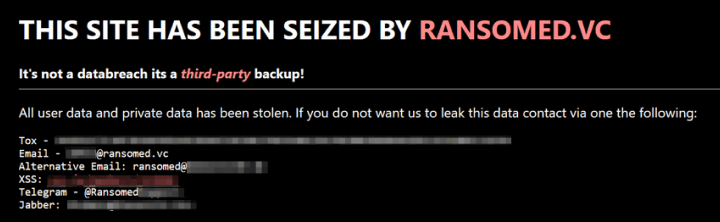
An example of the message left by Ransomed.vc to their victims.
Ransomware continues to haunt organizations worldwide, with groups like Ransomed.vc making headlines for their bold attacks. Here are some of the motivations, tactics, and ethical considerations of this emerging threat actor, shedding light on their operations.
Ransomed.vc came onto the scene in August 2023 when an individual known as “Ransomed” took to Telegram to announce the birth of their forum and chat channel. This event marked the genesis of a new player in the ransomware landscape, with the domain ransomed[.]vc hastily registered and an initial victim disclosed on their blog.
In an interview with Ransomed.vc’s operator conducted by the DailyDarkWeb, it became clear that financial gain ranks high on their list of motivations. The group boasts 77 affiliates and partners, primarily driven by the allure of monetary rewards. They are also occasionally motivated by political agendas, demonstrating a multifaceted approach to their attacks.
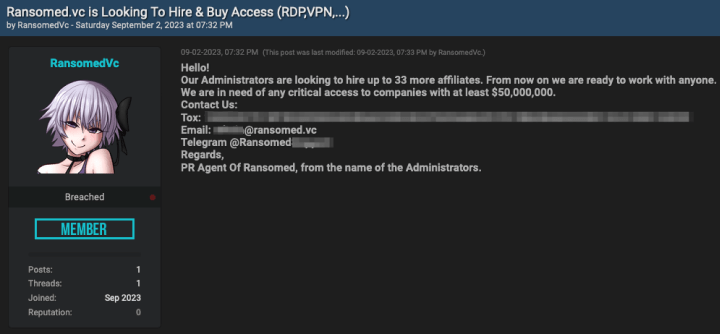
Ransomed.vc appears to still be hiring based on this BreachForums post.
Ransomed.vc has attacked companies in USA, Canada, Italy, and the European Union, and doesn’t cast its net indiscriminately. They target organizations with at least $5 million in revenue, indicating a calculated approach, allowing them to maximize their returns on each attack.
While Ransomed.vc didn’t delve into the specifics of their attack methods, they hinted at sophisticated techniques. During the interview, they refused to discuss anything about cryptocurrency or encryption methods. However, affiliates within the group are known to develop zero-day exploits, suggesting a high level of technical expertise.
When asked about the impact on victims, Ransomed.vc showed no remorse, attributing blame to the compromised entities for allowing security breaches. They remain unfazed by the consequences of their actions.
One notable tactic is the use of General Data Protection Regulations (GDPR) fines as leverage against victims. Ransomed.vc believes this approach forces companies into larger payments, enabling them to maximize their illicit gains.
According a SOCRadar article, Ransomed.vc has also worked in collaboration with Everest Ransomware, which emphasizes their well-established partnerships within the cybercriminal network.
Ransomed.vc remains tight-lipped about their plans and the composition of their teams, keeping their operations veiled in secrecy. While they claim they’ve earned enough, Ransomed.vc divulges little about how they spend their ill-gotten gains, apart from mentioning laundering through legitimate businesses.
Despite being relatively new to the cyberthreat landscape, Ransomed.vc’s swift rise to infamy includes a claim of successfully compromising Sony, marking a severe breach in the entertainment conglomerate’s security. The threat actors boldly declared their intentions not to ransom the compromised data but to sell it, citing Sony’s reluctance to meet their demands. This move showcases the audacity and confidence of Ransomed.vc, as they threatened to release sensitive data obtained from their intrusion.
Although not many details have been released on the extent of the compromised data, it underscores the serious implications of such attacks, not only for high-profile targets like Sony but also for businesses and individuals whose data may be at risk.
What sets Ransomed.vc apart is its assertion of being a secure solution for addressing data security vulnerabilities while operating in strict compliance with GDPR and data privacy laws. This commitment includes reporting violations to the GDPR agency in cases where payments are not received.
As Ransomed.vc continues to evolve and adapt, staying ahead of their tactics and motivations remains a critical endeavor for cybersecurity professionals. Understanding their operations is the first step toward developing effective countermeasures in an increasingly dangerous digital landscape.
