Leverage deep tradecraft knowledge
Blackpoint’s curated list of applications to block is based on real-life attacks our SOC witnesses firsthand.
Security Posture Rating
NEWMeasure cybersecurity maturity and get clear, actionable insights that expose gaps, prioritize improvements, and demonstrate real progress.
Managed Detection and Response (MDR)
NEW24/7 SOC combined with contextual intelligence, patented detection logic, and AI-enhanced alerts for rapid threat detection and response
Asset Inventory
NEWComplete visibility across your organization’s attack surface.
Vulnerability Management
NEWIdentify vulnerabilities and prioritizes which ones truly matter within your organization’s context
Cloud Posture
NEWPersistent monitoring, drift detection, and alignment with cloud security best practices to close security gaps
Application Control
NEWExpert currated list of application block rules to simplify management and customize application protection
LogIC (Streamlined SIEM)
NEWHyper-efficient, real-time event collection and automated mapping
Tenant Administrator
NEWIdentify at-risk tenants, track billing and renewals, and instantly act on time-sensitive security issues
Integrations
NEWIntegrations allow your business to streamline its security operations. Centralizing threat detection, response, and monitoring within a unified platform.
Endpoint Detection and Response (EDR)
NEWLightweight, patented technology delivering 24/7 endpoint protection with real-time visibility, threat detection, and response.
Visibility Across Attack Surface
NEWComprehensive visibility across client environment through a unified, contextual view that enables quicker actions, lowers risk, and delivers measurable results.
Prioritize What Matters
NEWCorrelate vulnerabilities, misconfigurations, and threat activity to determine which issues pose the greatest risk
Secure Cloud Identities
NEWProtect your cloud identities from attacks due to misconfigurations, policy drift, excessive permissions, and credential theft
Scale Security Operations
NEWStreamline the entire security lifecycle from asset discovery to threat response with automation, contextual insights, and enhanced efficiency
Meet Compliance Requirements
NEWSimplified logging and compliance with push button deployment and real-time reporting
Improve Cybersecurity Maturity
NEWAssess, monitor, and improve cybersecurity maturity with real-time insights and guided, prescriptive actions
Unified Security Posture
NEWCompassOne Platform
NEWSecurity Operations Center
NEWDedicated threat hunters and remediators, on call 24/7/365, with unparalleled cybersecurity expertise
Adversary Pursuit Group
NEWThis elite team is armed with real-time threat intel, delivering rapid response and unmatched protection.
Managed EDR
NEWUsing our patented technology and arming our 24/7/365 MDR with context to resolve threats faster.
Cloud MDR
NEWExpert security monitoring & rapid, context-driven response for your cloud environments.
Streamline your business with simplified oversight into what matters most – staying secure. Our customizable application settings are based on our SOC’s deep experience in stopping sophisticated attacks.
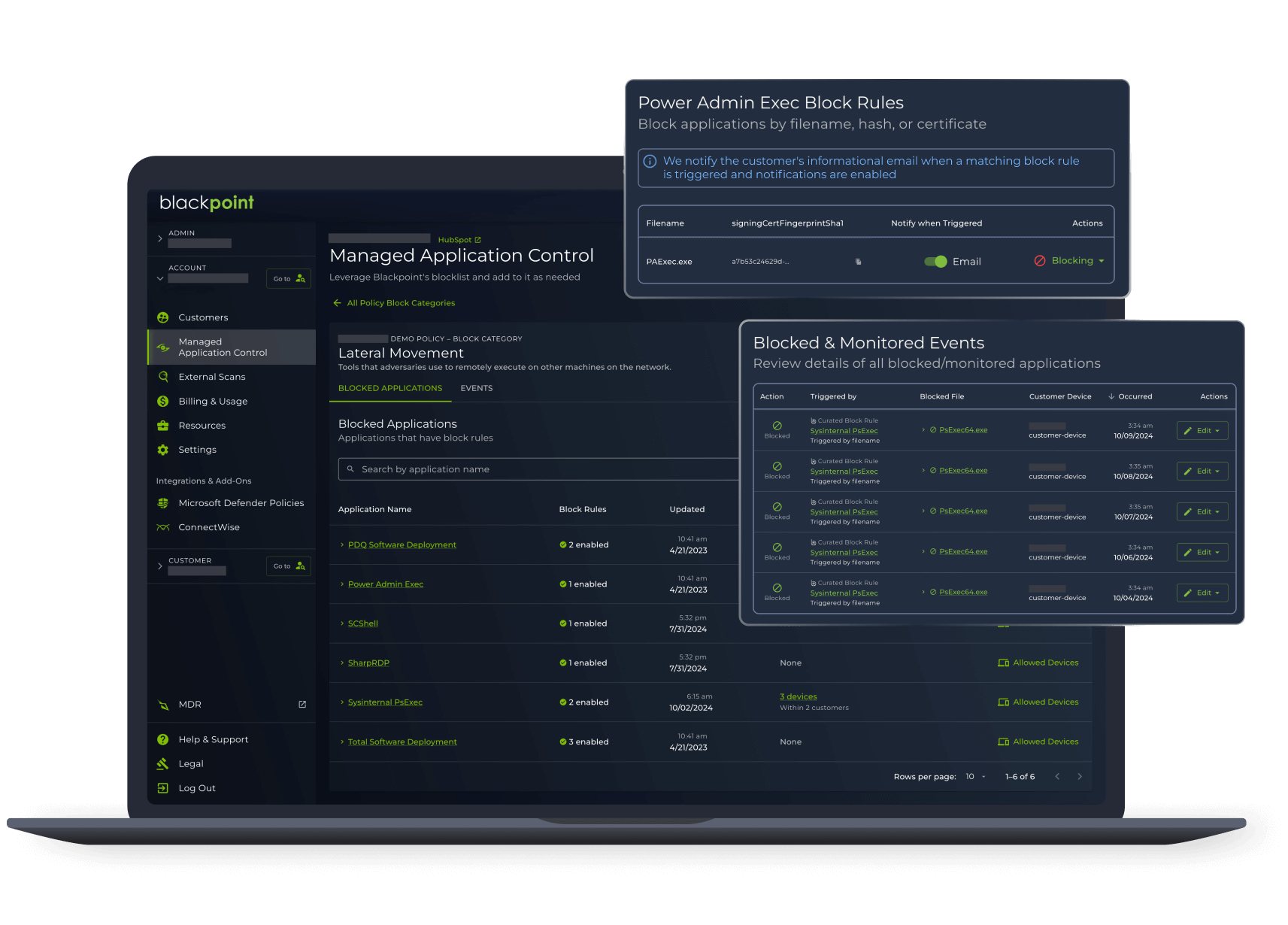

Remove the resource burden of managing a strict zero trust strategy and replace it with the expertise of a 24/7/365 SOC. Secure your data gateways with curated application settings and real time response on threats, tailored for your individual business.
Blackpoint’s curated list of applications to block is based on real-life attacks our SOC witnesses firsthand.
Create custom rules for your customers’ specific needs to avoid false positives, over-generalizations, and inadequate oversight.
Available through our product bundle, Blackpoint Response, you can add our modern take on zero trust for one cost-effective price alongside an ever-growing ecosystem of product offerings.
Curated block lists free up teams and help them get ahead of threats.
Application blocking enhances your defenses and keeps both you and your clients safeguarded against bad actors.
Continuously monitor emerging threats and update blocklist entries instantly, so you can operate with confidence.
Managed application control provides our partners with the visibility and control over their individual application security needs. With Blackpoint Cyber’s deep expertise and threat insight, you can apply curated application settings to your and your clients’ extended perimeters and reduce operational bottlenecks while improving user experience.
Partner with APG’s threat intel for a recommended application block list and our 24/7/365 SOC’s management to immediately detect and block malicious requests based on our combined settings.
Create custom rules for your various customers to gain visibility into device activity across extended perimeters to enforce security policies. This will ensure endpoints are always properly configured, improving your overall security posture.
Deliver elite, customized security protection without interrupting your customers’ productivity with endless verification requests, false positives denying correct users access, and time-consuming maintenance of settings.
Enable access to organizational resources and data from anywhere and from any device, while ensuring that all endpoints meet your security requirements.
Experience Blackpoint Cyber’s Active Cybersecurity in action – see a demo now and witness threat elimination in real-time.
Discover Active Cybersecurity