Authentication Bypass
Most elements of ScreenConnect server administration are secured behind a web login page that will not allow a user to proceed without proper credentials (Figure 1).
Figure 1: ScreenConnect Login Portal
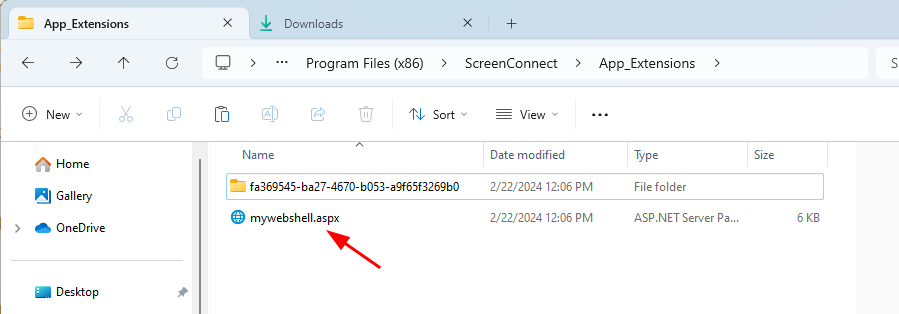
CVE-2024-1709 is an authentication bypass that allows even an unskilled attacker to bypass this page and directly access ScreenConnect administrator functionality. Ultimately, an attacker adds an administrative user with a predetermined username and password, then logs into the created account to instantly gain administrative privileges. For example, launching our Proof-of-Concept (PoC) script to create an account named “Administrator” with a lengthy password (Figure 2).
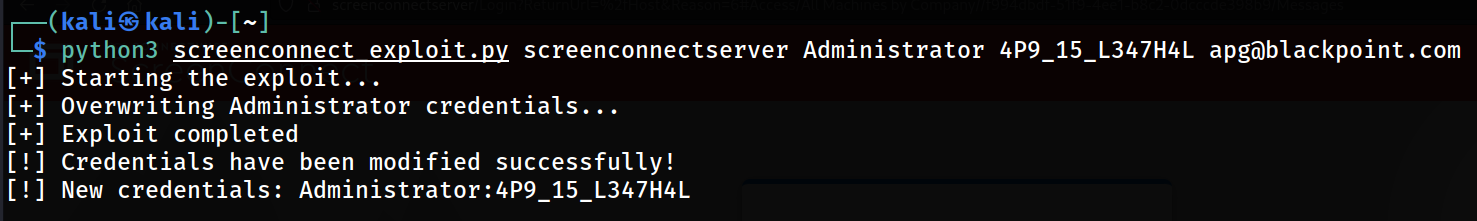
Figure 2: Authentication Bypass Script
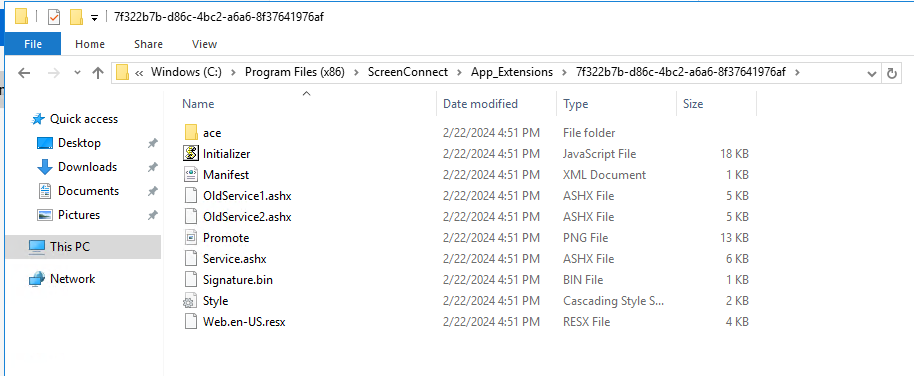
The addition of this created account will be recorded in ScreenConnect’s Users.xml file. It It is strongly recommended that this is one of the files included regularly in any internal audit. Figure 3 is an example of one of these Users.xml files that was taken from one of our compromised Honeypots.
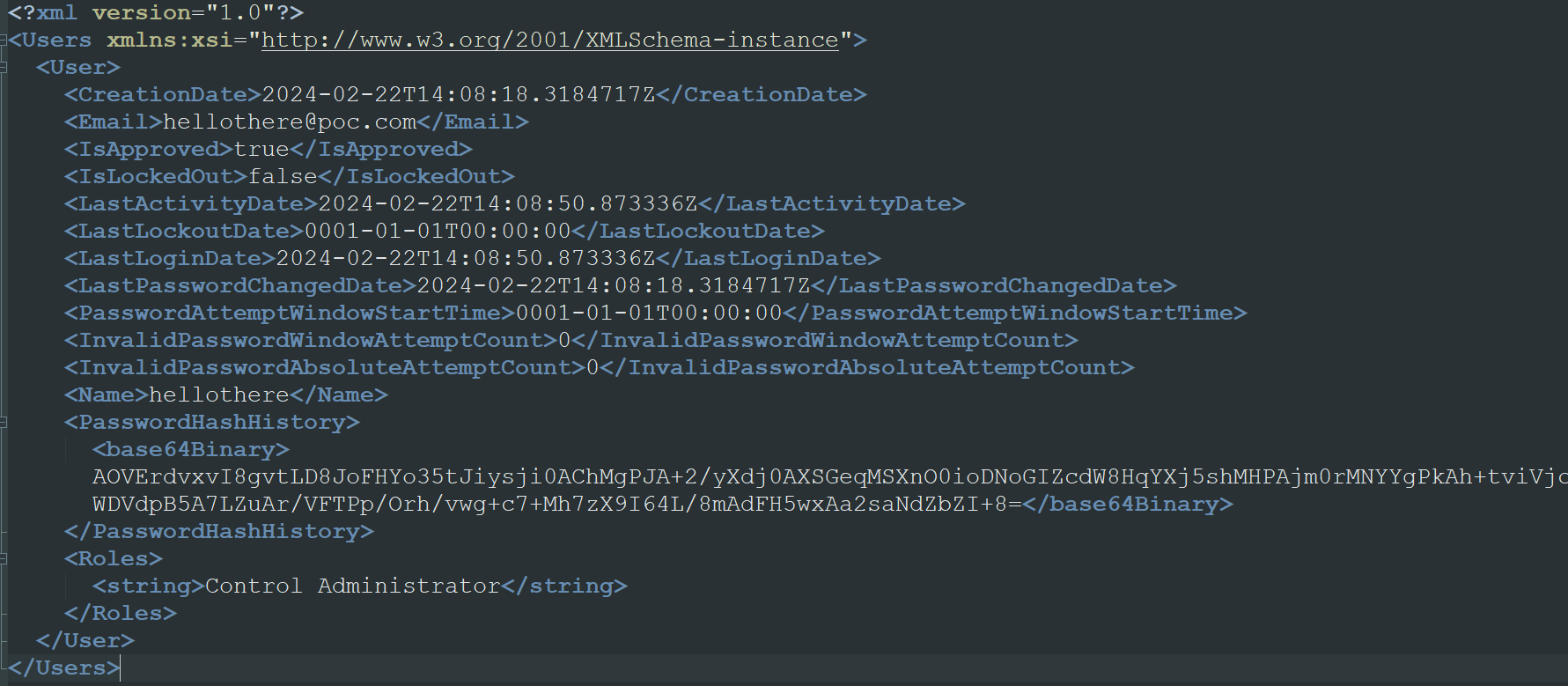
Figure 3: Compromised Users.xml
With the account added, an attacker can simply log into the portal using the same credentials they supplied during exploitation. They are now an administrator of the ScreenConnect server (Figure 4).
 Figure 4: Administrator Login
Figure 4: Administrator Login
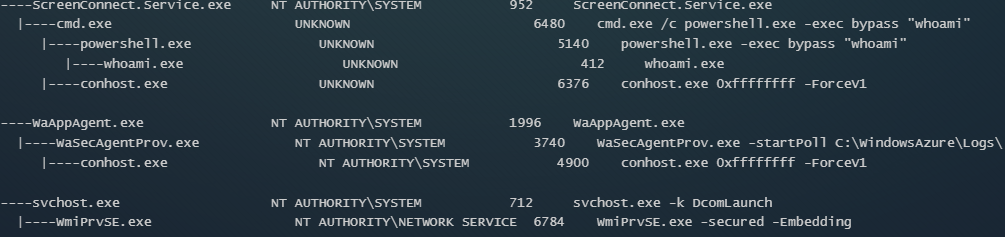
Note with extreme caution that, even without additional exploitation, the attacker now has an alarming amount of access to the victim’s IT capabilities. A ScreenConnect server administrator can view all ScreenConnect client desktops remotely, transfer files, and deploy software on them (Figure 5). This could enable mass compromise or lateral movement through the ScreenConnect client devices.
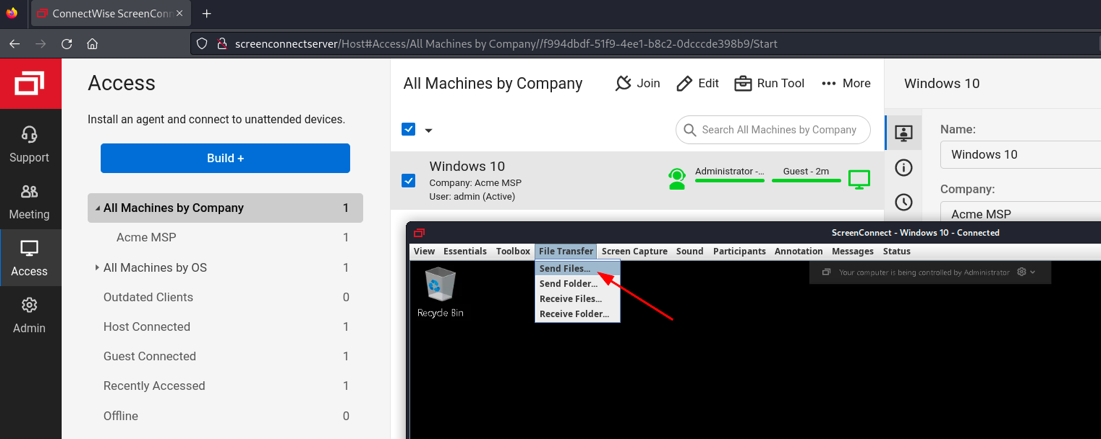 Figure 5: Send File
Figure 5: Send File
The use of remote monitoring and management (RMM) tools in the deployment of malicious payloads is something that we first brought to light in 2022 and was further supported by the CISA advisory in 2023. These tools are heavily relied upon in the MSP space, meaning the impact of this exploit could have significant financial and reputational ramifications for any organization that has not deployed a patch.
These risk factors make CVE-2024-1709 a dangerous issue when used alone. However, alongside CVE-2024-1708, an attacker might go a step further.




 Figure 4: Administrator Login
Figure 4: Administrator Login Figure 5: Send File
Figure 5: Send File