Blackpoint is continuing to monitor the exploitation in the wild of the ScreenConnect vulnerabilities.
To recap:
CVE numbers have been allocated to the exploits as follows:
- CVE-2024-1709: An authentication bypass using an alternate path or channel (CVSS 10)
- CVE-2024-1708: A path traversal issue (CVSS 8.4)
Exploitation of these vulnerabilities is trivial. ConnectWise has provided guidance for mitigating attacks at their advisory page.
Our guidance remains the same: ensure ScreenConnect installations are patched to the latest version.
Additionally, ConnectWise has provided version 23.9.10 that removes license restrictions, available from the ConnectWise website.
In the Wild Exploitation
Blackpoint’s Adversary Pursuit Group has been identifying and recording indicators of compromise (IoCs) from ongoing exploitation. The most common flow of compromise is threat actors compromising vulnerable ScreenConnect instances to establish persistence. In one instance, we identified a threat actor dropping a second remote access tool, SimpleHelp, as demonstrated in the diagram below:
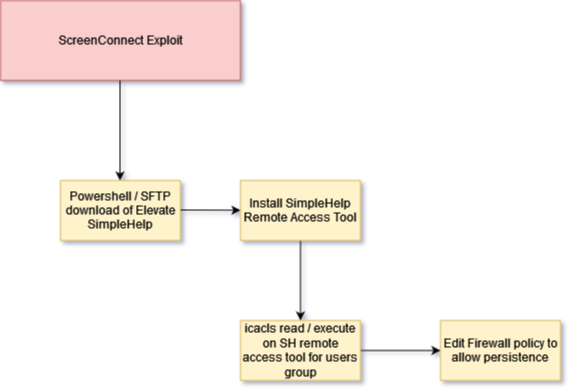
The Blackpoint SOC identified and stopped this attack from progressing further.
We have observed the following indicators in the wild:
IP Address: 91.92.254.193
Description: SimpleHelp Connection
IP Address: 98.159.157.56
Description: SimpleHelp Connection
File Hash (SHA 256): 5d1df950b238825a36fa6204d1a2935a5fbcfe2a5991a7fc69c74f476df67905
Description: SimpleHelp Installer
Some of these indicators have also been identified by CISA as part of the BlackCat campaigns in the healthcare sector. While we cannot specifically confirm the behavior we observed was BlackCat activity (as the indicators are only related to SimpleHelp and do not contain additional BlackCat indicators), we do believe the common activity supports our assessment that threat actors are using this vulnerability to stage and perpetrate ransomware attacks.
What happened?
On Feb. 19, 2024, ConnectWise advised of two vulnerabilities in ScreenConnect versions 23.9.7 and prior. These vulnerabilities are rated critical:
- CWE-288 Authentication bypass using an alternate path or channel (Severity 10)
- CWE-22 Improper limitation of a pathname to a restricted directory (“path traversal”) (Severity 8.4)
Both vulnerabilities could allow an attacker to remotely execute code or view and impact potentially sensitive data.
What should I do?
If you use ScreenConnect, you should patch to version 23.9.8 immediately. Given the criticality of these vulnerabilities, if you are unable to patch, we recommend that you do not use ScreenConnect until you can patch.
How is Blackpoint protecting me?
Blackpoint customers running Managed Application Control in blocking mode are protected against ScreenConnect. Be aware that previously approved installations are still approved – these approvals should be rejected until patched. Once vulnerable versions have been patched across all systems, Blackpoint customers can allow ScreenConnect execution via the Managed Application Control console.
The Blackpoint SOC is also constantly monitoring for the use of ScreenConnect across our customer base and reaching out as we identify vulnerable versions.
Blackpoint will continue to monitor this developing situation.
This blog has been updated continuously throughout the incident from February 20-22 and February 28.
Written By:
Nick Hyatt
Director of Threat Intelligence
Nick Hyatt has extensive expertise in technology, support, and information security, with experience spanning small businesses to Fortune 500 companies across various industries. He has a deep understanding and practical experience in incident response, threat intelligence, digital forensics, and malware analysis. His hands-on skills encompass malware forensics, data mapping, threat hunting, and e-discovery in diverse environments.
Connect with Nick on LinkedIn.
