The cybersecurity landscape is constantly evolving, and a new player has emerged on the scene: the Rhysida Ransomware Group. According to a recent SOCRadar article, this Ransomware-as-a-Service (RaaS) group made its first appearance in May 2023 and quickly established itself as a significant ransomware operation. Their initial high-profile attack targeted the Chilean Army, and since then, they have been targeting various sectors and industries worldwide.
Rhysida portrays itself as a “cybersecurity team,” claiming to highlight potential security issues while simultaneously threatening victims with the public distribution of their exfiltrated data. The group’s attack methods include deployment via Cobalt Strike, a penetration testing tool misused by threat actors, and phishing campaigns.
Their ransom notes have been written as PDF documents as well as system messages, providing insights into the types of systems they target.
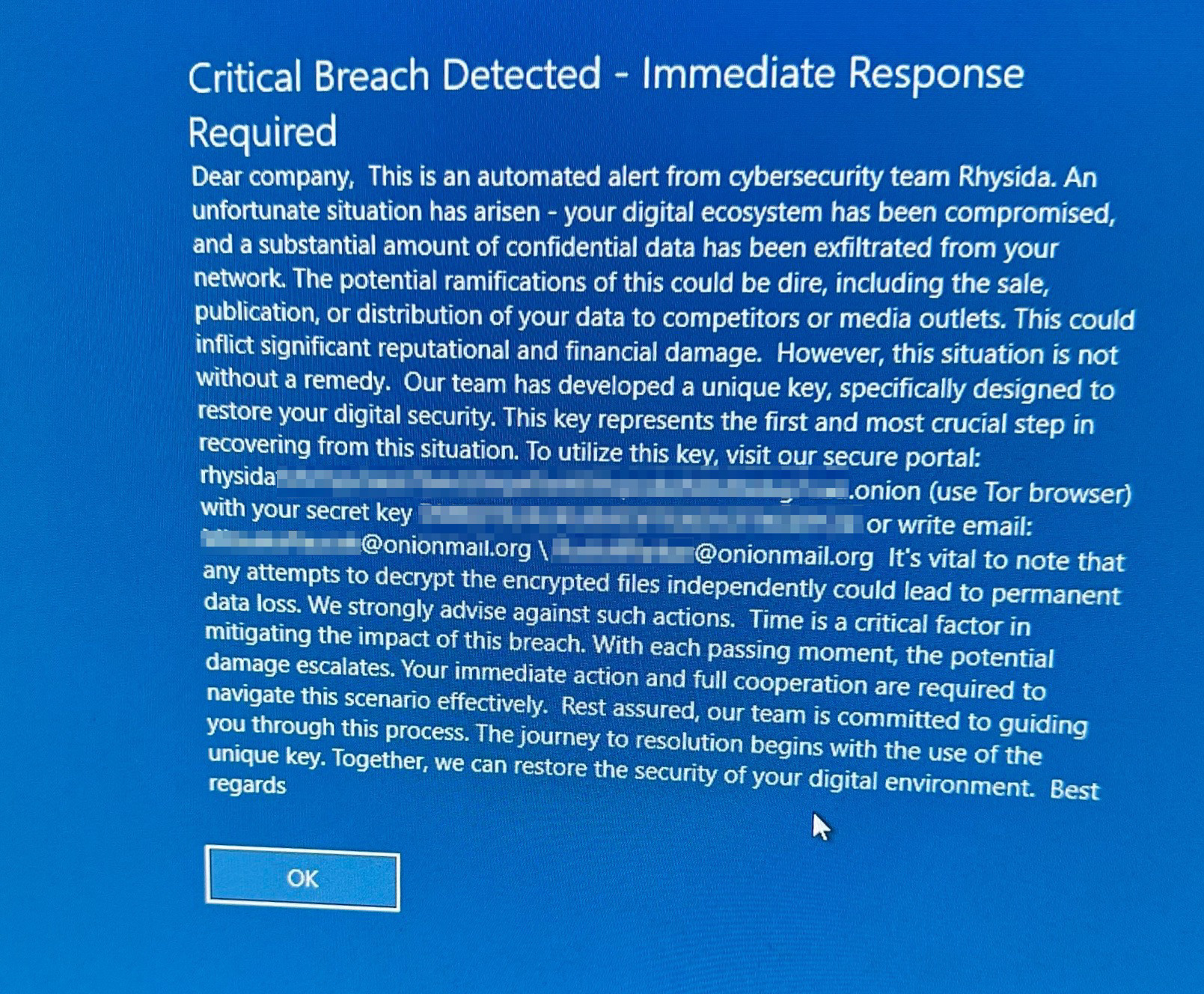
Ransom Note Via System Message–Recently Delivered to Medical Facility
The group follows a double extortion strategy, threatening victims with both data encryption and public data exposure. According to SOCRadar, their ransomware is a 64-bit Windows cryptographic application using a 4096-bit RSA key with the ChaCha20 algorithm.
Like many other ransomware groups, Rhysida’s TOR page features their logo, auctions, victim lists, and data shares. This is where they instruct you to go in their ransom note to communicate with them and settle the ransom. They have mainly targeted the education, manufacturing, and healthcare sectors. Victims in the United States, Italy, Spain, and the United Kingdom are the focus of over half of their attacks.

Image of the Rhysida TOR Page (SOCRadar)
Although the ransom note is written in grammatically correct English with a “helpful” tone that expresses they want to work with the victim to fix the problem, some of the content on their TOR site has misspellings, bad grammar, and threatening language. An image from Secplicity showed their contact form which included the following statement: “We have your documents, we know where you live, we know your childrens scool. You are welcome on the dark side of the Internet.”
To protect against Rhysida Ransomware, organizations are advised to:
- implement virtual patching,
- conduct phishing awareness training,
- use endpoint security solutions,
- maintain immutable backups, and
- employ network segmentation.
Firewalls, intrusion detection systems, and a well-defined incident response plan are also crucial in mitigating potential damage from an attack. In addition, implementing the principal of least privilege, which limits user and application access, can also help prevent the spread of ransomware throughout a network.