Businesses of all sizes are at risk of a myriad of online threats. One of the stealthiest among them is Business Email Compromise (BEC). At its core, BEC is a form of cyber fraud, wherein hackers compromise legitimate business email accounts to conduct unauthorized transactions or extract sensitive information. This type of attack capitalizes on the trust relationships between employees, and its repercussions can be financially devastating. It’s essential for business owners to recognize this threat and take necessary precautions.
Understanding Business Email Compromise
A Threat to Modern Enterprises
Introduction
What is Business Email Compromise?
BEC is not just a sophisticated phishing attempt; it’s a targeted attack. Criminals begin by choosing a company and then researching its organizational structure, roles, and responsibilities. The attacker might compromise an executive’s email account or pose as them, sending requests for wire transfers or sensitive data to subordinates. In some cases, the BEC scams might even impersonate vendors or partners, requesting changes in payment details. Because these emails appear to come from trusted sources, they can be particularly difficult to spot. Here are a couple of examples:
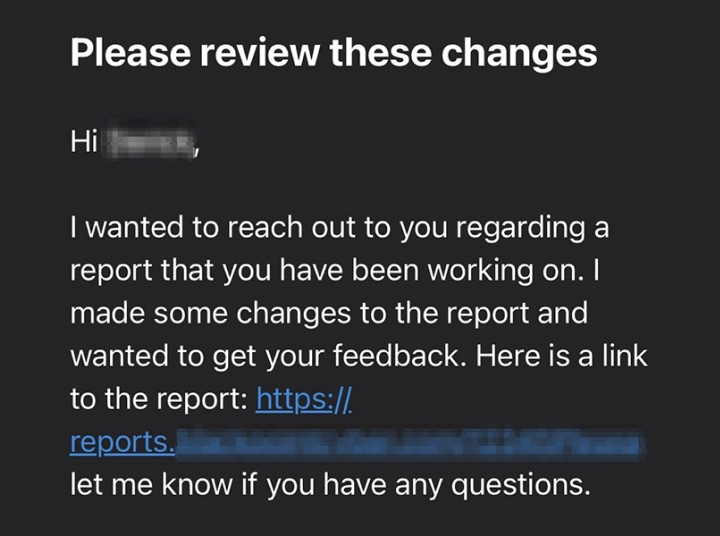
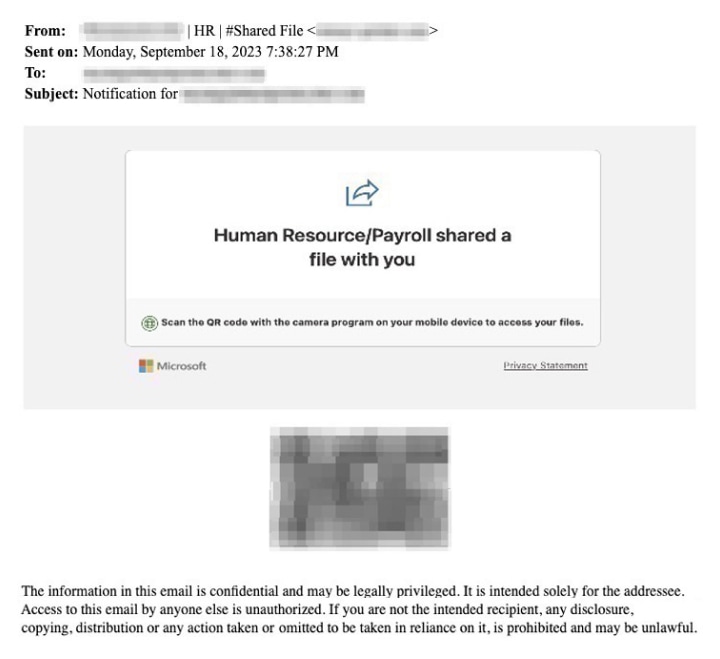
The Prominence of the Threat
The scale and impact of BEC cannot be overstated. According to the FBI’s Internet Crime Report in 2022, there were 21,832 BEC complaints resulting in adjusted losses of over $2.7 billion. The true cost might be even higher, as many businesses may not report these incidents due to reputational concerns. The prevalence of remote work has only increased the vulnerability of businesses, as employees often rely heavily on emails for communication when working from home. In fact, Verizon found that BEC attacks have almost doubled, now representing more than 50% of incidents within social engineering attack patterns. Additionally, IBM found that BEC was one of the top three actions on objectives in 2022. Most recently, threat actors are using generative AI, such as WormGPT, to create highly persuasive, fake emails as part of their BEC attack chains.
Combatting the Threat
Protection against BEC requires a multifaceted approach. First, businesses should prioritize employee education. Staff members, especially those in finance or HR roles, should be trained to recognize signs of BEC and verify any unexpected or unusual requests, regardless of the apparent source. Technical measures, like multifactor authentication (MFA), can help safeguard email accounts from unauthorized access. Additionally, setting up policies that require dual approval for significant transactions or changes in payment details can add another layer of protection.
While implementing measures like MFA can help safeguard email accounts from unauthorized access, relying on them alone is insufficient. Modern threat actors are evolving, often bypassing these measures using sophisticated techniques. This is where Managed Detection and Response (MDR) services come into play. MDR provides businesses with continuous monitoring and proactive threat hunting, identifying anomalies that traditional tools might miss. Moreover, a 24/7 Security Operations Center (SOC) ensures that potential threats are identified and mitigated in real-time. At Blackpoint, we’ve been stopping an average of 60 BEC attacks a week! Together, cybersecurity training, MFA, MDR, and a dedicated SOC provide a robust defense against the complex threat landscape that includes BEC and other cloud threats.
Summary
Business Email Compromise is a sophisticated and highly effective form of cybercrime, which leverages trust within organizations to cause financial and informational loss. Its rise in prominence underscores the need for businesses, regardless of size or industry, to prioritize cybersecurity. By prioritizing training, implementing technical safeguards, and investing in around-the-clock protection, businesses can significantly mitigate the risks associated with BEC and ensure a safer digital future.
About Blackpoint Cloud Response
Are you ready to combat business email compromise with strong internal measures, backed by a true MDR and 24/7 SOC? Through our product bundle, Blackpoint Response, you can get Cloud Response: active response for your cloud. Cloud Response extends Blackpoint’s MDR service and expert SOC to support hybrid and cloud environments, minimizing your attack surface so you can operate your business safely. Currently, Cloud Response supports Microsoft’s 365 service including Azure Active Directory (AD), Exchange, and SharePoint, with further support to come! To learn more, book a demo today.
DATE PUBLISHEDSeptember 26, 2023
AUTHORBlackpoint Cyber
SHARE ON
Subscribe to the Blackpoint Blog
Don’t let a lack of awareness leave the organizations you protect vulnerable to sophisticated and elusive attacks. Subscribe now for a weekly roundup of Blackpoint’s empowering articles.
Subscribe now!