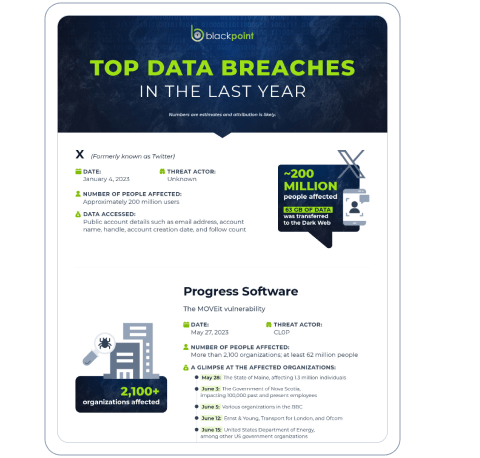
In this infographic, we highlight significant cybersecurity incidents since November 2022. These data breaches affected major companies like X (formerly known as Twitter) and T-Mobile, as well as government entities like the State of Maine and the U.S. Department of Energy. It reveals the scale of the breaches, with millions of individuals impacted and various types of sensitive data compromised. The MOVEit vulnerability, exploited by threat actor CL0P, notably affected over 2,100 organizations, demonstrating the widespread reach of these attacks. Therefore, businesses of all sizes must maintain cybersecurity measures able to combat the most advanced threat actors, including BlackCat and Money Message.