In a recent blog post, Trellix’s Advanced Research Center has unveiled a novel attack technique that leverages the “search-ms” URI protocol handler, a lesser-known feature of the Windows operating system. This innovative method allows threat actors to exploit unsuspecting users by crafting deceptive emails and compromised websites that trick users into executing malicious code disguised as trusted files.
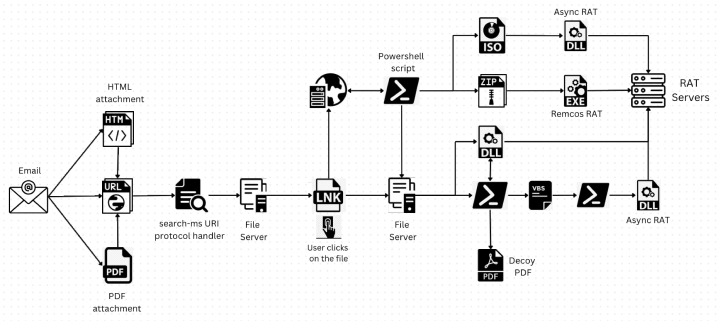
Attack chain example
The attack begins with the threat actors directing users to websites that exploit the “search-ms” functionality using JavaScript hosted on the page. This technique has even been extended to HTML attachments, thereby expanding the attack surface. The attackers cleverly disguise the search results of remotely hosted malicious shortcut files as PDFs or other trusted icons, just like local search results. This technique conceals the fact that the user is being provided with remote files, creating an illusion of trust. As a result, the user is more likely to open the file, assuming it is from their own system, unknowingly executing malicious code.
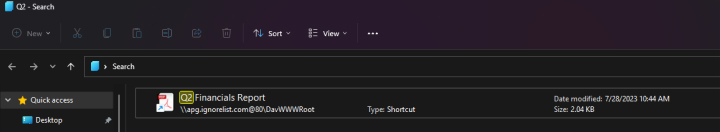
Opening remote file in Explorer
The malicious payloads delivered through this campaign are primarily remote access trojans (RATs), specifically Async RAT and Remcos RAT. These RATs are nefarious programs that provide cybercriminals with unauthorized remote control over a compromised system. Upon successful infection, these RATs can carry out a wide array of malicious tasks. These tasks can range from pilfering confidential data, keeping tabs on user behavior, or executing remote commands, to propagating themselves to other devices connected to the infected system.
Mitigating this attack is as simple as deleting the following registry keys:
- HKEY_CLASSES_ROOT\search
- HKEY_CLASSES_ROOT\search-ms
Upon further analysis, we have successfully created a detection mechanism for this type of attack. This strategic development significantly enhances the protection of Blackpoint’s partners, fortifying their defenses against such threats.
In summary, the “search” / “search-ms” URI protocol handler has become a powerful tool for cybercriminals, and we can expect more attacks using this method. It allows attackers to deliver harmful payloads while avoiding standard security defenses. To stay safe, users should be cautious with unfamiliar links, avoid clicking on suspicious URLs, and avoid downloading files from unknown sources.
