What Has Occurred
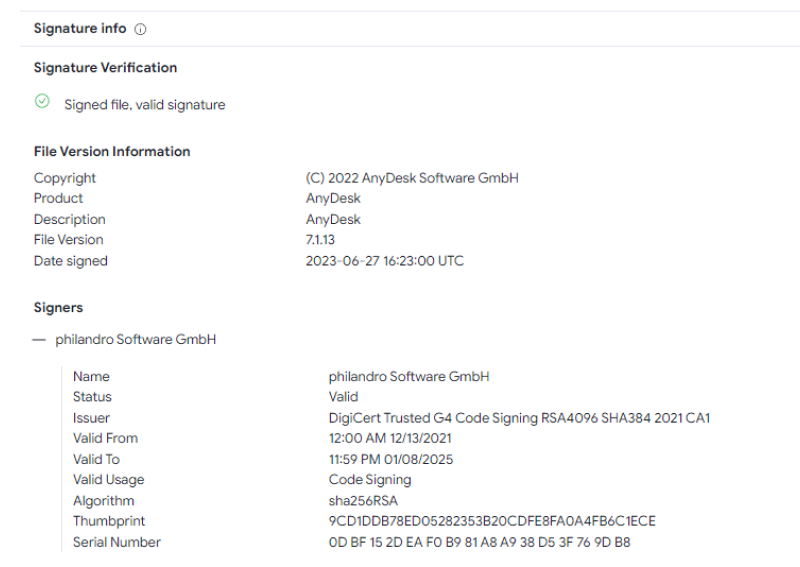
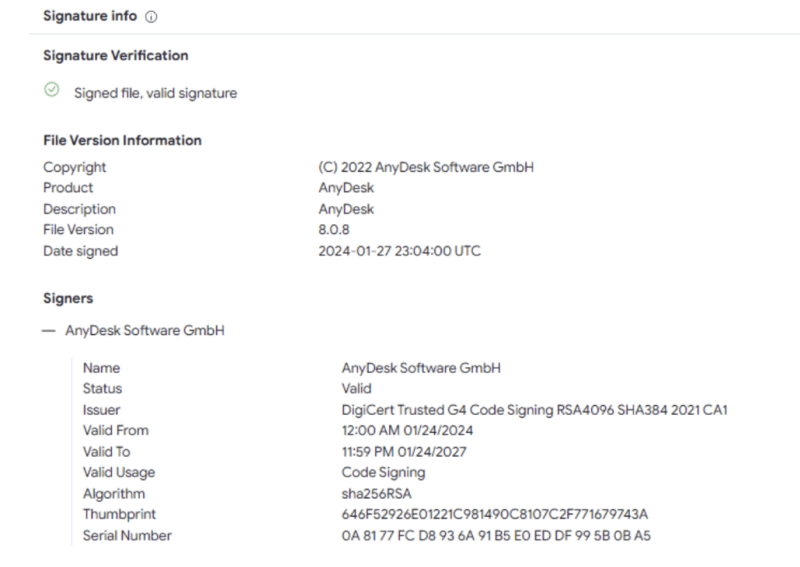
On Friday, February 2nd, AnyDesk put out a public statement that some production systems had been compromised. AnyDesk, a remote desktop application, is used by many Managed Service Providers (MSPs) to provide remote assistance, system management, and monitoring to their end clients. AnyDesk reported they believe their services are safe to use and that end-user devices were not impacted. With this announcement, AnyDesk also noted they are revoking all certificates, potentially indicating that a threat actor gained access to their private key for certificate signing.
After AnyDesk’s statement, Blackpoint’s SOC immediately began an investigation and found that we had blocked applications running the old certificate over 2,000 times since May of 2023. After reviewing the security blocks in place, we found no evidence suggesting that threat actors are currently using the compromised certificate to deploy their own malware against the partners and end clients we protect.
Since the announcement on February 2nd, we blocked over 200 attempted executions with the old certificate. We blocked and reported these actions to our partners, advising them to update to the latest version of AnyDesk. Any customers using Blackpoint’s Managed Application Control offering with AnyDesk blocked are protected from malicious usage of the old certificate. Taking into consideration the potential for abuse, on Friday we started blocking the old certificate in a new category, ensuring protection for customers who opted out of blocking AnyDesk.
For a behind-the-scenes look at how the certificate can be used to add extra validity to malware, view the SOC’s video here:
A real-world example of this certificate abuse technique occurred in August 2023. Threat actors were observed using Ivacy VPN’s certificate to sign their malware. The certificate belonged to PMG PTE LTD and was the same one that was used to sign Ivacy VPN’s installer. By leveraging trusted certificates, threat actors gain legitimacy, enabling them to bypass some security measures.
Why It Matters
Considering the critical importance of safeguarding against supply chain attacks, especially those targeting companies providing remote access solutions, it is evident that such vulnerabilities and attacks, like this one, pose a significant threat. Threat actors exploiting these vulnerabilities can deploy malware to end systems, leveraging the trusted relationship between MSPs and their end clients. Situations such as these remind us how critical it is to employ robust security measures capable of neutralizing these threats. Managed Application Control is designed specifically to address this challenge, offering an advanced layer of protection against unauthorized software and ensuring that only verified applications are allowed to run.
The Certificate That Will Be Revoked:
The New Certificate:
Written By:
Jason Rathbun
Technical Director of Threat Operations
Jason Rathbun is a cybersecurity leader who has been with Blackpoint Cyber for over three years. He is the current Technical Director of Threat Operations, responsible for directing a team of analysts on how to identify and swiftly address potential threats in real-time to ensure company IT systems are protected. Jason is a highly-ranked competitor in Capture the Flag (CTF) challenges, ranking within the top 1% on multiple platforms. Prior to his current role, Jason held positions in development and engineering at Data Federal Inc. and BDK Inc. Drawing on his prior expertise and being a Certified Red Team Operator, Jason excels in testing out new exploits, tactics, and techniques to ensure detections are accurate and in place at all points of the kill chain.
Connect with Jason on LinkedIn.