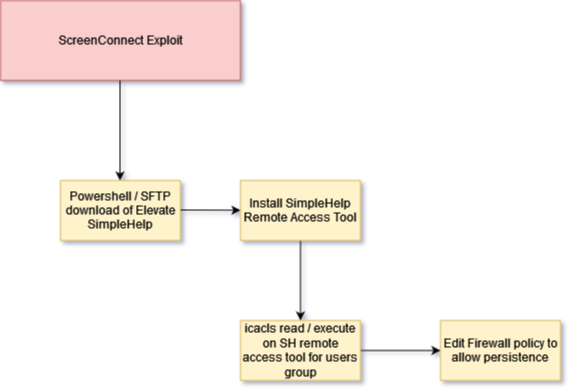
Blackpoint is continuing to monitor the exploitation in the wild of the ScreenConnect vulnerabilities.
To recap:
CVE numbers have been allocated to the exploits as follows:
- CVE-2024-1709: An authentication bypass using an alternate path or channel (CVSS 10)
- CVE-2024-1708: A path traversal issue (CVSS 8.4)
Exploitation of these vulnerabilities is trivial. ConnectWise has provided guidance for mitigating attacks at their advisory page.
Our guidance remains the same: ensure ScreenConnect installations are patched to the latest version.
Additionally, ConnectWise has provided version 23.9.10 that removes license restrictions, available from the ConnectWise website.