Introduction
Cybersecurity frameworks’ primary purpose is to provide organizations, such as Managed Service Providers (MSPs), with best practices, guidelines, and procedures to improve their cybersecurity posture, in turn, improving their end clients’ cybersecurity posture. A security framework is designed to help businesses identify risks, protect assets, detect threats, respond to incidents, and recover from breaches. There are many security frameworks to choose from. Options include:
The Benefits of Framework Alignment
Aligning to one of the above frameworks, or a combination of a couple of them, has numerous benefits. They include:
- Gaining best practices and a structured approach for addressing cyberthreats, both pre-existing and brand new.
- Receiving guidance on how to identify, assess, and manage risks effectively, before they become breaches.
- Enabling a consistent level of security across your business and end clients.
- Using common language to communicate cybersecurity issues with your team and end clients.
- Reviewing your security posture frequently to stay one step ahead of evolving threats.
- Increasing the speed and effectiveness of your incident response efforts.
- Creating a baseline for vendor assessment to ensure standards are met.
- Enhancing credibility and reliability with stakeholders, board members, and end clients.
- Meeting or exceeding industry-related requirements.
- Learning how to justify budget requests and allocate resources for maximum impact.
How Do You Choose?
Unsure which one to align to?
Opt for Blackpoint’s enhanced version of NIST.
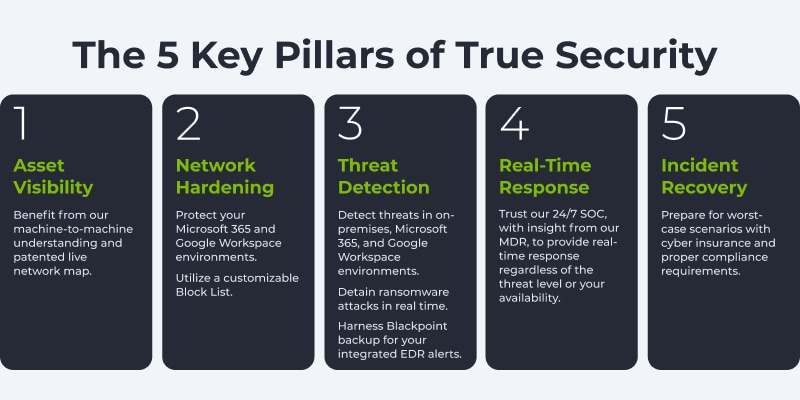
The NIST Cybersecurity Framework includes the following functions: Identify, protect, detect, respond, and recover. At Blackpoint, we’ve taken these pillars a step further. We’ve examined the five pillars of NIST and asked ourselves, “What does that look like?” The pillars therefore became asset visibility, network hardening, threat detection, real-time response, and incident response. With more specific naming conventions and the MDR-powered solutions we provide, we answer that question for you every step of the way.
A Closer Look at Blackpoint’s Security Framework
- Asset Visibility: An up-to-date inventory of all devices and cloud services, along with their involved security risks, is key to staying on top of cybersecurity initiatives.
- Network Hardening: Proactive measures include firewalls, IAM, strong login requirements, AV, anti-malware, EDR, regular backups, & encrypted data. These foundational practices are no longer sufficient against advanced threats but are still critical to protecting against easily manipulated points of entry.
- Threat Detection: Continuous monitoring, log collection for compliance, and proactive threat hunting ensure that an organization’s finger remains on the pulse of cyberthreats. Know what may be coming and keep an eye out for it.
- Real-Time Response: Live threat detection and cyberattack detainment are key to stopping threats before lateral spread, payload deployment, and data encryption/exfiltration occurs.
- Incident Recovery: A plan for how to respond if an incident occurs is important. It should include who does what, how you’ll maintain or regain operations, and how you’ll recover.
How To Navigate Stack Alignment
How do you align your stack to it? Follow these steps:
- Understand the framework you’re adhering to.
- Take inventory of your current security tools, solutions, and processes, and note each one’s primary function.
- Map each tool, process, or control to the relevant framework subcategory.
- Note any instances where you don’t have a solution in place to address that subcategory.
- Develop a plan to address each of the above gaps, prioritizing them based on risk level.
- Ensure your organization’s policies, procedures, and documentation are updated to reflect framework alignment. Document any exceptions or justifications.
- Review and update your security stack to align with evolving requirements.
- Train your team and end clients; raise awareness to ensure new implementations are communicated clearly and abided by.
- Consider having a third party validate your alignment for additional credibility. This outside perspective may further improve your strategy.
Adhere to Blackpoint’s Security Framework with Blackpoint Response
Blackpoint Response includes everything to protect modern hybrid workflows with comprehensive, next-generation endpoint protection and application control, supported by our industry-leading cloud and on-premises MDR. Elevate your security stack with the best in active response through one cost-effective package.
Get Started Today
Adhere to industry best practices, increase credibility amongst customers, and stop threats actors in their tracks, all while saving money and simplifying your security stack. Maximum coverage, impeccable ROI, and industry-leading response times—built just for you.