Bytes & Insights: The Key Takeaways
In Summary: This article provides an in-depth analysis of Quick Response (QR) codes, detailing their origins, functions, applications, and the potential security risks they present. It emphasizes the need for vigilance in the face of growing cyberthreats and offers protective measures to ensure a safe and efficient user experience.
Why It Matters: The rise of QR codes presents both an opportunity and a challenge. On one hand, they are a seamless integration tool for various digital services, streamlining operations and user experiences. On the other hand, the potential security vulnerabilities associated with malicious QR codes highlight the critical need for enhanced cybersecurity measures. MSPs must be proactive in educating their clients about these risks, ensuring that both their infrastructure and their end users are protected. Furthermore, with businesses increasingly relying on QR codes for daily operations, the responsibility of MSPs to provide robust security solutions has never been greater.
What are QR Codes?
Quick Response (QR) codes are a form of two-dimensional barcodes that have become increasingly popular in recent years, integrating with various aspects of our digital lives. Originating in Japan in the 1990s, they were initially designed for the automotive industry. Today, they have expanded into sectors such as retail, food service, advertising, and health, facilitating quick data sharing and mobile payments.
How Do They Work?
QR codes function by representing information in a square grid of black and white dots. When these codes are scanned using a camera, the encoded data, which can be a URL, text, or other information, is quickly decoded by the scanning device, such as your mobile device. This swift transition from the physical to digital realm make QR codes attractive for businesses and consumers alike.
The Convenience of QR Codes
The versatility of QR codes has been evident in numerous applications. Restaurants replaced traditional paper menus with QR code-based digital ones, streamlining the dining experience. Marketers use QR codes to effortlessly transition potential customers from a physical advertisement to a digital landing page. During the height of the COVID-19 pandemic, QR codes were instrumental in providing contactless services, from ticketing to health status verifications. And it would be hard to forget Coinbase’s Super Bowl commercial last year, which simply featured a QR code bouncing across tv screens nationwide for 60 seconds.
Hidden Dangers Amidst the Convenience
But as with most technologies, there is a flip side. The widespread adoption of QR codes has piqued the interest of cybercriminals. What most users see as a simple tool for convenience, hackers view as an opportunity to exploit unsuspecting users. A malicious QR code can redirect a user to a phishing website, initiate a download of malware, or even extract personal data from a device.
- Phishing: A QR code can easily lead a user to a fake website where they are prompted to enter personal or financial information. Since many users trust the authenticity of QR codes, they may not double-check the URL before entering sensitive data.
- Malware Downloads: Some QR codes are programmed to initiate an automatic download when scanned. If a user isn’t vigilant, they could unintentionally download malicious software onto their device.
- Rogue Network Connections: QR codes that auto-connect users to Wi-Fi networks can be manipulated to connect devices to rogue networks. These can be rigged to connect users to malicious networks, where attackers lie in wait to snatch sensitive data.
Decrypting QR Codes
Decrypting or previewing the content of a QR code before acting upon its embedded instruction is like peeping through a peephole before opening a door. By doing so, users can ensure they’re not being directed to malicious websites, unintentionally downloading harmful software, or sharing sensitive information unknowingly. Just as one wouldn’t blindly click on an unfamiliar link in an email, the same prudence should be applied to QR codes. Decrypting them offers an essential layer of protection, helping users to navigate the digital realm safely and confidently.
- The camera on Apple and Android devices allow users to preview the QR code link prior to opening it.
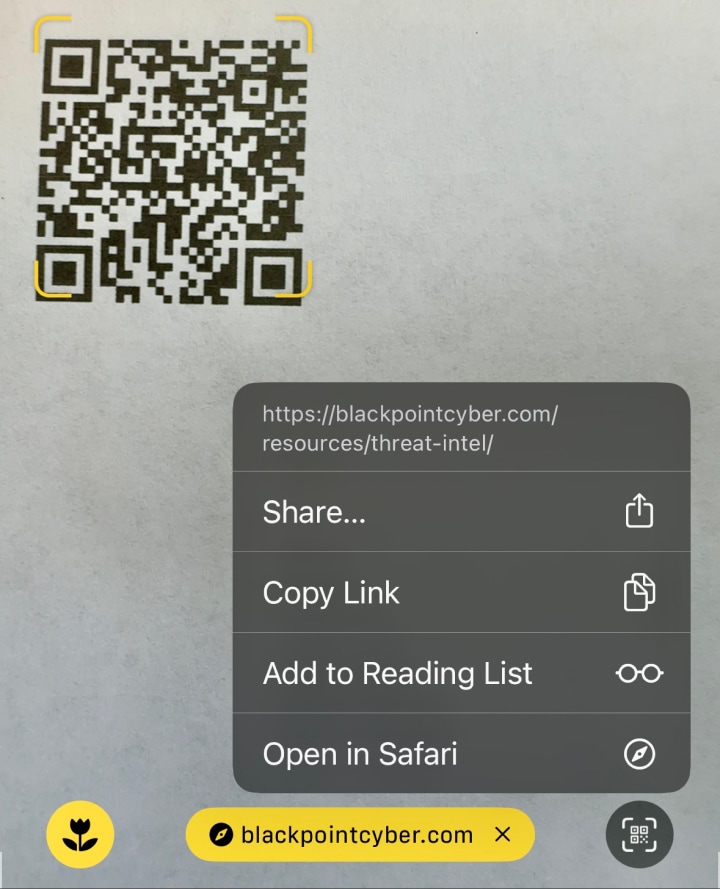
An Apple example of viewing and verifying the full link before clicking on it.
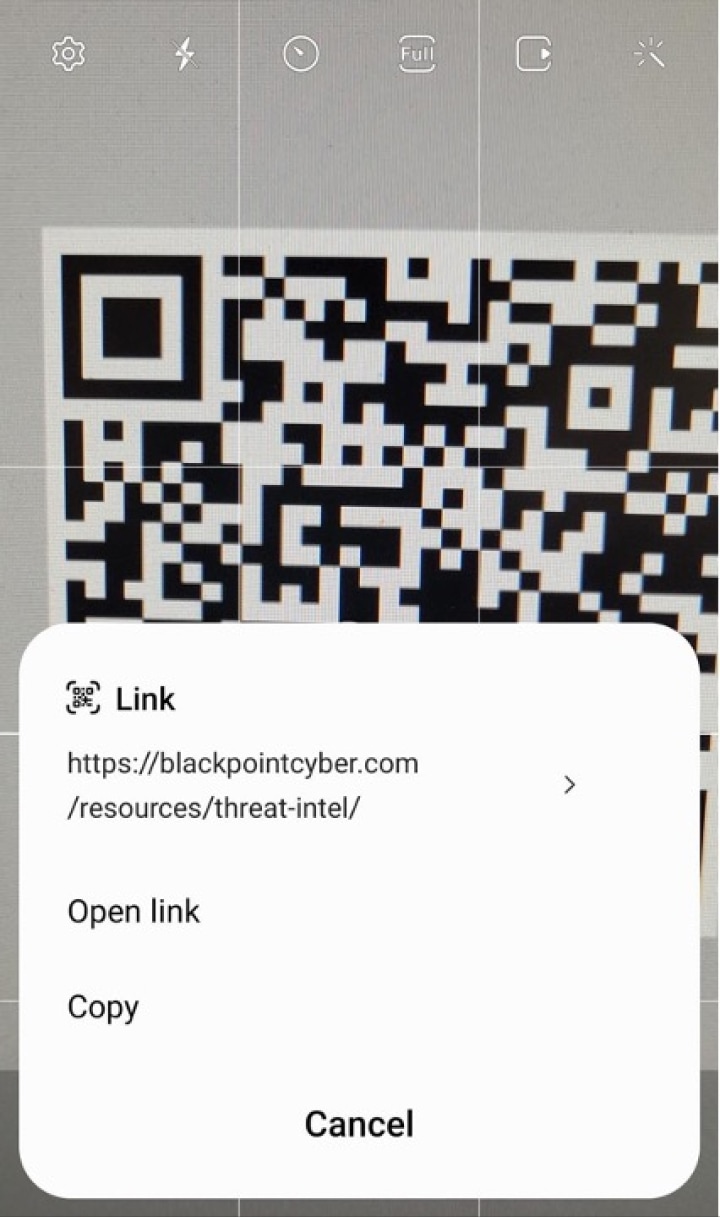
An Android example of viewing and verifying the full link before clicking on it.
- Tools such as CyberChef have the ability to upload a QR Code image and decrypt it into the plaintext output using the “Parse QR Code” recipe.
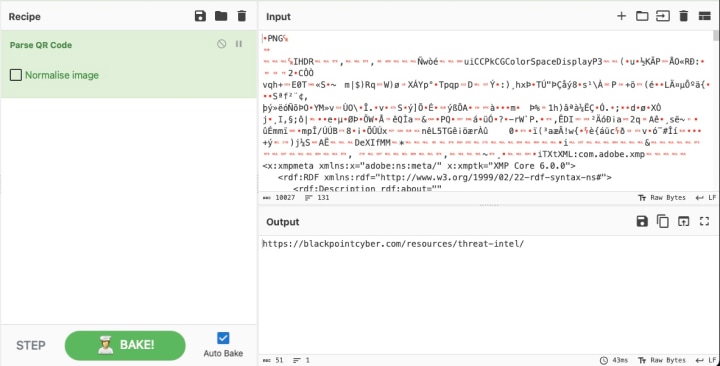
CyberChef allows users to upload and parse QR Codes into plaintext.
Protective Measures
Given these security concerns, it’s essential for users to exercise caution when scanning QR codes:
- Use Trusted Scanners: Opt for native or reputable QR code scanning apps that offer security features and URL previews.
- Verify URLs: Always check the decoded URL to ensure it directs to a legitimate website, especially before entering any personal information.
- Avoid Scanning Random Codes: Be wary of scanning QR codes from untrusted sources or those found in public places without clear context.
- Beware of Covered Codes: There has been a trend of people placing a malicious QR code over a valid one. For example, they’ll cover a restaurant menu QR code with a malicious one.
Conclusion
While QR codes offer unmatched convenience in today’s digital world, it’s imperative to approach them with a discerning eye. As they continue to permeate various sectors, understanding the potential risks and practicing safe scanning habits will be essential to ensure a secure user experience.
