An uncovered security vulnerability in Windows allows threat actors to sign and load malicious kernel-mode drivers using expired or pre-2015 certificates. These actors leverage open-source tools to alter the signing date of drivers, bypassing Windows’ certificate policies.
The majority of the observed drivers have metadata indicating Simplified Chinese language code, suggesting they are frequently used by native Chinese speakers according to Cisco Talos.
The Windows operating system consists of two layers, user mode and kernel mode. Kernel-mode drivers facilitate communication between these layers and allow access to the system’s underpinnings. Exploiting a malicious driver can compromise the system by bypassing the security barrier between user and kernel modes.
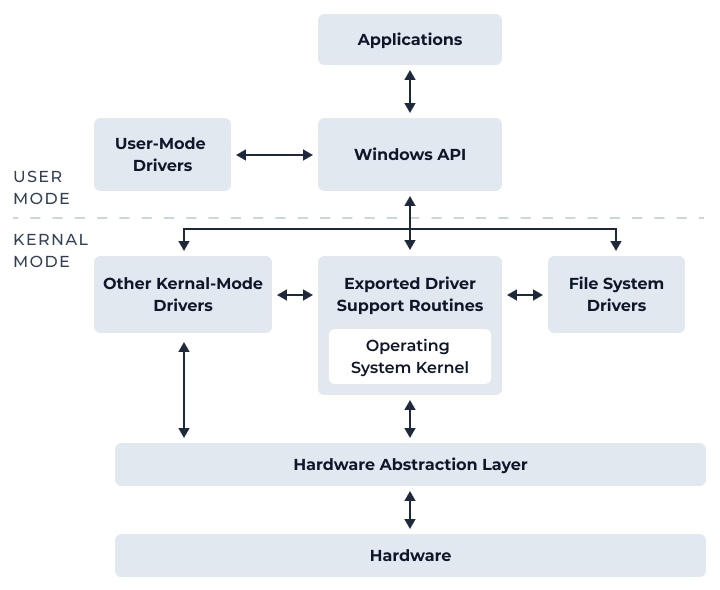
Windows Kernel Architecture. Credit: Microsoft
Microsoft requires kernel-mode drivers to be digitally signed by a verified certificate authority, which ensures driver integrity and defends against malware. However, a policy exception allows signing with non-revoked certificates issued or expired before July 29, 2015, if they chain to a supported cross-signed certificate authority.
Malicious drivers pose a significant threat as they can provide attackers with kernel-level access, potentially compromising the entire system. In addition to evading endpoint detection, threat actors can manipulate processes and maintain persistence on infected systems.
Talos identified open-source tools (HookSignTool and FuckCertVerifyTimeValidity) being used to sign malicious drivers as well as re-sign cracked drivers to bypass digital rights management (DRM).
These tools are being used to forge signature timestamps on drivers, taking advantage of the policy exception. When previously seen used for game cheats, they manipulate the signing date of the drivers, and enable the loading of malicious drivers signed with expired or non-revoked certificates.
Microsoft has blocked the certificates discussed in the blog post and released an advisory, suggesting the installation of the latest Windows updates to mitigate the threat.
To stay up to date on all APG intel, follow them on Twitter and Reddit.
