The SocGholish malware family has been haunting the digital realm for over five years. It was first seen in the wild in April 2018, according to Red Canary. It has used a variety of tactics to elude detection, but their overall end goal remains the same: gain initial access.
With this specialty, they sell SocGholish as a service to other malware or ransomware threat actors, allowing them to drop their payload as a follow-on attack.
SocGholish has been able to survive for over five years due to its advanced techniques that allow it to remain difficult to detect and stop. Its primary distribution methods are drive-by-downloads and phishing campaigns that drop a .zip or .js file that users are tricked into launching.
They use masquerading techniques to evade detection from users and security software, such as masquerading as a software update for a web browser, but fake Microsoft Teams and Adobe install files have also been seen utilized.
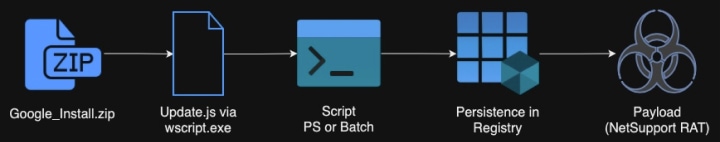
This is a typical attack pattern seen from SocGholish
In addition to masquerading techniques, SocGholish is selective about its targets and the environments and systems they attack. According to Proofpoint, they use Traffic Directing Services (TDS) to:
- determine if targets are acceptable
- obscure the attack
The initial JavaScript file is used to collect information such as operating system versions, geographic locations, IP addresses, browser cookies, and previous attack indicators to determine if they want to proceed with the attack and connect it to the command and control (C2) infrastructure for additional exploitation.
The follow-on scripts, payloads, and C2 subdomain are customized for that victim’s system or environment, which is used to deter incident response from being able to analyze, reproduce, or collect information post incident or outside the infected environment.
The final payload will ultimately be determined by the threat group using SocGholish to gain initial access. That said, the attack pattern has shown they typically use a Batch or PowerShell script to gain persistence in the registry and then detonate their final payload. This payload may be a remote access trojan (RAT), ransomware, or other malware variant.
The biggest mitigation strategy is informing end users not to open emails or click on links from untrusted sources. You should also monitor for JavaScript files in the downloads folder or unauthorized scripts (wscript.exe, powershell.exe, cmd.exe) being run on the machine.
Learn more about prominent threat actors and their heightened focus on initial access in Blackpoint Cyber’s Annual Threat Report.
