Take a journey with me to Anytown, USA where a CEO has just approved the purchase of the latest Security Information and Event Management (SIEM) solution, boasting log monitoring and advanced threat detection. It was a move met with much optimism to strengthen their cybersecurity efforts amidst an ever evolving and advancing digital landscape. His team spent many hours over many months deploying and configuring the solution, and at long last, the project is finally complete.
After some time, the SIEM detected unusual behavior patterns and generated an alert. A threat actor was attempting to access and exfiltrate sensitive data. However, the security team, inundated with a high volume of security alerts and false positives, struggled to respond in a timely manner. By the time they fully grasped the severity of the situation, the threat actor had advanced further into the organization’s network, exploiting vulnerabilities, and attempting to cover their tracks.
While the SIEM had done its job, the time-consuming task of processing and actioning on the data had hindered the organization’s ability to stop the threat in real time.
This scenario is all too common in today’s business world. Organizations are struggling to keep up with the increasingly sophisticated threats where attackers are moving faster within networks, prioritizing attack speed over extended periods of stealth. In Mandiant’s M-Trends 2023 Special Report, they discovered that the global media dwell time (the time from intrusion to detection) has decreased from 21 days to 16 days. Over at Sophos, they discovered it dropped to eight days in the first half of 2023. This trend highlights the growing opinion that traditional SIEMs are exceptional at being sources of record for incident response and digital forensics, but in their current form they cannot stop the advanced attacks that are being seen in today’s digital landscape.
Beyond being a system of record, traditional SIEM solutions are built upon the idea that not all parts of an attack are addressable in one attack vector (endpoint, network, cloud, etc.) and to get a complete picture, you must be able to stitch all this data together. In the case of a traditional SIEM solution, the various data sources are sending logs that are processed once they are ingested. And while the flavors of SIEM solutions will vary, with one solution touting one feature over another, at their core, you can expect the following functionality across the board:
- Aggregation and Correlation of Security Events
The main value of a traditional SIEM solution is that they will collect and organize security events from various sources to provide a view of activities in an IT environment. - User Behavior Analytics
Another function of traditional SIEM systems is that they use user behavior analytics to analyze the normal work patterns of users and detect deviations from normal behavior, raising alerts on potential threats. - Behavior, Signature, & Anomaly Detection
Traditional SIEM solutions incorporate anomaly detection to distinguish regular behavioral patterns from potential threats. - Log Management and Analysis
A large function of traditional SIEM solutions involve the collection, analysis, and secure archiving of log and alert data to gain better visibility into various activities and meet IT regulatory mandates. - Reporting
Being able to parse the data from several sources enables traditional SIEM solutions to be a centralized reporting source.
Having a traditional SIEM in your organization can improve your overall security posture, but there is one clear limitation to detecting and responding to threats from SIEM logs: the lack of real-time response. Traditional SIEM systems may provide alerts and notifications for security events, but the response often requires manual intervention and coordination across different security tools and systems, leading to delays in acting against threats.
This is where a solution like Blackpoint Cyber’s solution suite, anchored around our SIEM+ functionality comes into play. Not only does Blackpoint Cyber cover the core functions of a traditional SIEM, but it also resolves traditional SIEM response inefficiencies.
Blackpoint’s agent aggregates and correlates metadata from many sources. We then use proprietary detection logic to create real-time alerts regardless of the metadata source. As attack patterns are not linear, our solution will correlate events into a single alert, adding a layer of orchestration and contextual detail. At this point, our 24/7 Security Operations Center (SOC) will then respond and remediate attacks as they are happening in real time. The way Blackpoint can respond and remediate faster than a traditional SIEM can be summed up in one word. Location.
Essentially, traditional SIEMs aggregate data then perform analysis and attempt to find the right patterns after the data has been processed. The way Blackpoint’s ecosystem is built, we are looking for the right patterns (behaviors, tradecraft, and malicious use of tools) at the source and then once that has been done, we send the data to the repository for storage which allows for the real-time response that is desperately needed today.
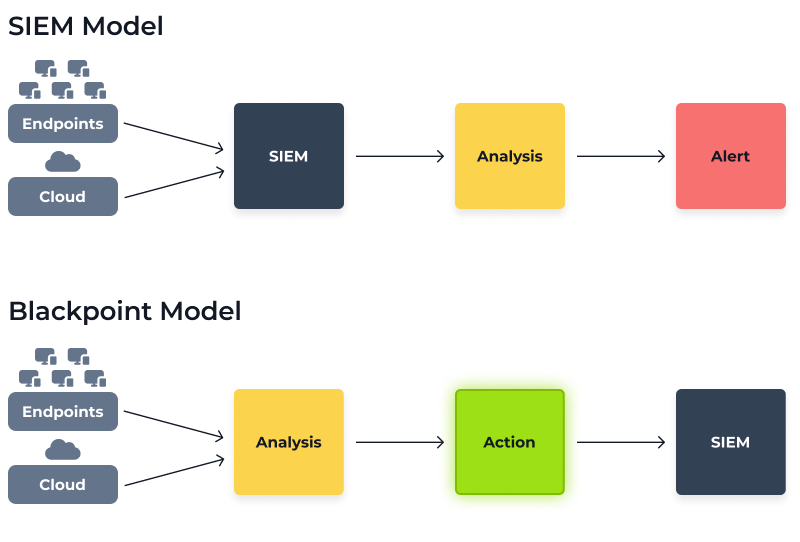
In today’s cybersecurity landscape, Blackpoint’s comprehensive model, featuring proactive analysis and correlation, is key to business resiliency. You must be able to analyze, detect, and respond to threats in real time, along with having the assurance that the event data is stored securely, can be accessed, and reported on.
With Blackpoint Cyber, you get the core functionality of a traditional SIEM—secure data storage, access, and reporting—along with real-time threat disruption needed for today’s most advanced attacks.